Despite resources spent, metrics mistrust is the norm
June 01, 2020
The recent 2020 Financial Services Security Metrics Report found that security teams are spending an inordinate amount of time on processing and reporting on security. Yet, with all this time and resource spent on producing and reporting these metrics, security leaders still do not fully trust them.
Security metrics are now essential to any mature security programme, so much so that 96% of security leaders utilise metrics to measure their cybersecurity posture. It is, however, not an easy task, as we will explore.
So why is it taking all this time?
At the risk of sounding like a broken record, this is a very important question to ask, especially given the findings of the new report.
There is an overload of requests for metrics from a large variety of stakeholders: regulators, risk/GRC, IT, the board, the business, audit, customers – just to name those highlighted in the report.
Ultimately, these stakeholders are looking for reassurance that the security function is doing everything within its power to keep the organisation as secure as possible. Perhaps that’s a nice way of saying: ‘see how far they can stretch already tight resources’.
Here’s a graphic detailing the frequency of requests from various stakeholders:
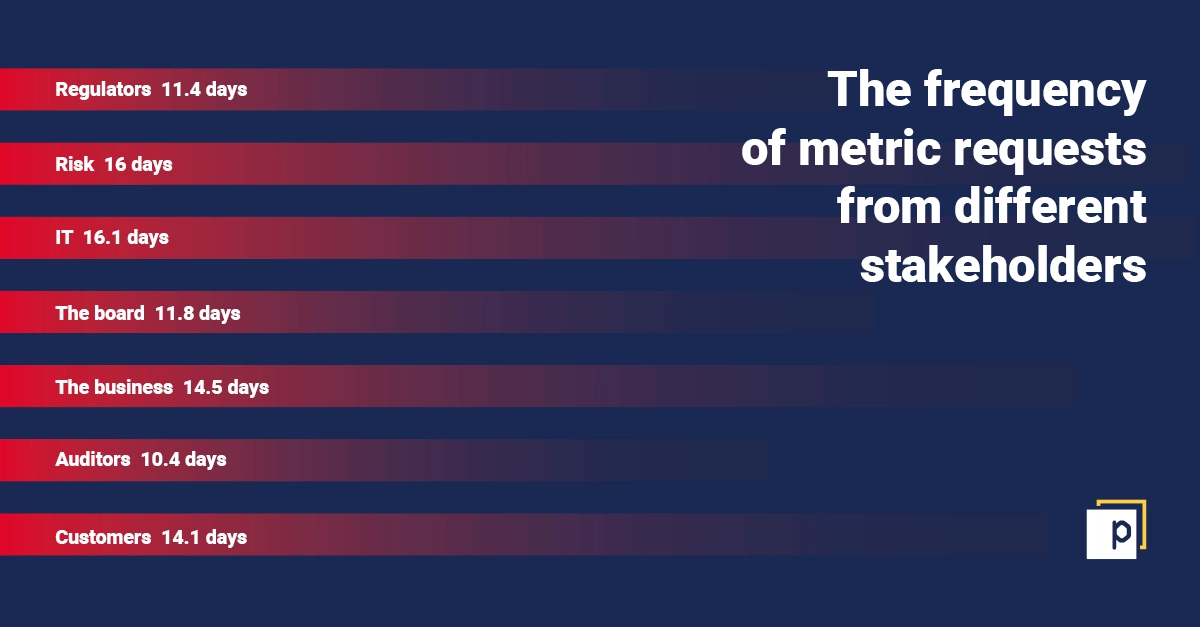
It will come as no surprise that requests are coming most frequently from auditors (every 10.4 days), regulators (every 11.4 days) and the board (every 11.8 days).
Regulators across the world are upping their game. In recent years, new regulations have come into effect: GDPR in Europe, the SHIELD Act in New York, CCPA in California. And there is an upward trend. For example, the MAS Cyber Hygiene Notice in Singapore, seen by some as an indicator to future regulations, requires that banks ensure controls are present on every asset – which is far more difficult to prove to the regulator. On top of all this, it is more than likely that each regulator requires the same information in a different way, only adding to the burden of resources.
This regulation trend likely will result in more thorough and frequent audits. As the graph suggests, this may already be the case. It is by no means uncommon for security initiatives to be driven by audit points as security audits are one of the key indicators of security posture in many organisations. Hence, we see a high frequency of requests for information in that category.
Equally, the board needs to see metrics in order to ascertain a clearer picture of the organisation’s security posture. Gone are the days when a board would ask for a qualitative opinion of an IT leader, who might rely on gut feel or just quote the number of security tools they had purchased. This is no longer accepted. The board wants demonstrable data, effectively communicated. The report shows that a third of respondents say boardrooms want data at least 4-6 times per week, or even every day.
And that’s only three of the seven key stakeholder categories. It takes time to respond to these requests sufficiently. Security teams allocate around 5 days per month for each of the main stakeholder groups. This means that virtually every day there is someone in the security team working on metrics for a stakeholder group. While that may be an important role, automating this process frees up valuable time and resources to actually do security – investigate incidents or address alerts. That is to say, proactively help improve security rather than reporting on it.
All this effort, but there is still a lack of trust
Despite all the effort and resources going in to creating a mature security metrics programme, many security leaders do not trust the results. The study highlights that the biggest challenge in reporting across all stakeholders is a lack of trust in the data.

Part of the blame can be put at the door of tool sprawl. While this problem is hardly unique to cybersecurity, the average arsenal of security tools can be particularly fragmented. A 2019 report found that most security teams are running more than 50 different tools. Similarly, a study from Forrester found that this abundance of security tools can have an adverse effect on security, as it can lead to a false sense of security in your security (sorry).
The issue is that most security tools are not explicitly designed to be used in tandem, so manual collation of data from multiple tools is required to answer even the simplest of questions or produce basic metrics. While there are some vendors trying to overcome this with various integrations and packages, data is still siloed across the plethora tools. Unfortunately, manual efforts to bring that data together can be long-winded and error-prone.
In many organisations, there is no single source of truth, no set of organisation-wide data that can be trusted by every stakeholder.
Creating the single source of truth
Creating that single source of truth and automating that process is the key to alleviating these pains.
Once this is created (this is where Continuous Controls Monitoring works its magic ) all the stakeholder groups we spoke about above – IT, regulators, risk, audit, the board, the business, customers – can all get eyes on the same set of data. CCM can also provide the ability to self-serve, saving yet more time and resource in by eliminating the middleman.
These stakeholders need different perspectives and cuts, but there should only be one version of the underlying data so that all the answers to all the questions these stakeholders have are reliable and trustworthy.
If you’re looking for more information on how to overcome these challenges, get in touch at contact@panaseer.com.