
Seven tips for automated security reporting
The majority of organisations waste time and resources on uncoordinated cybersecurity reporting. The need for automation is self-evident. Our Security Leaders Peer Report found the average enterprise security team has 76 security tools. This represents a 19% increase since 2019, when the figure was 64. 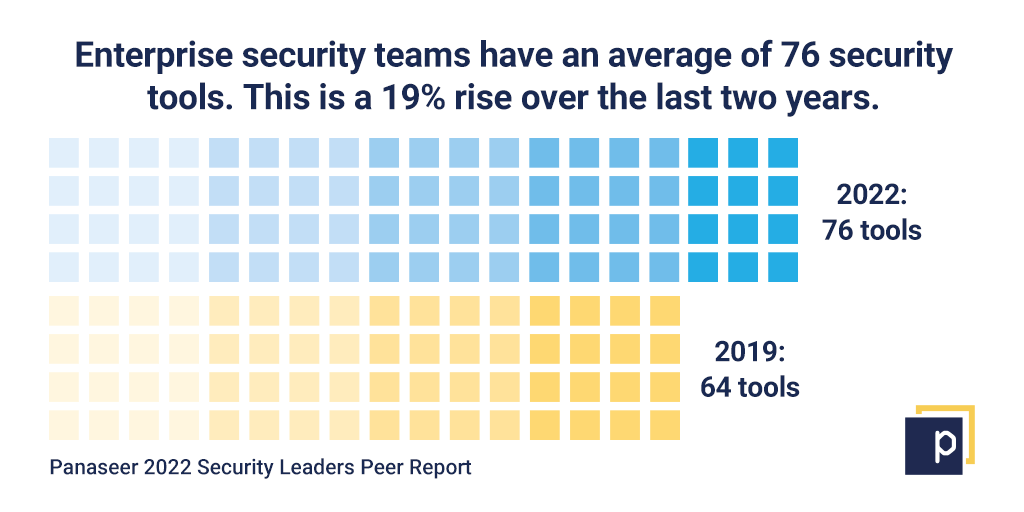 This proliferation of tooling is creating oceans of data for security teams to parse, manipulate, understand, format and report. It’s becoming untenable. Security teams are now spending 54% of their time on manual reporting. And it’s getting worse — the 2019 figure was 40%.
This proliferation of tooling is creating oceans of data for security teams to parse, manipulate, understand, format and report. It’s becoming untenable. Security teams are now spending 54% of their time on manual reporting. And it’s getting worse — the 2019 figure was 40%. 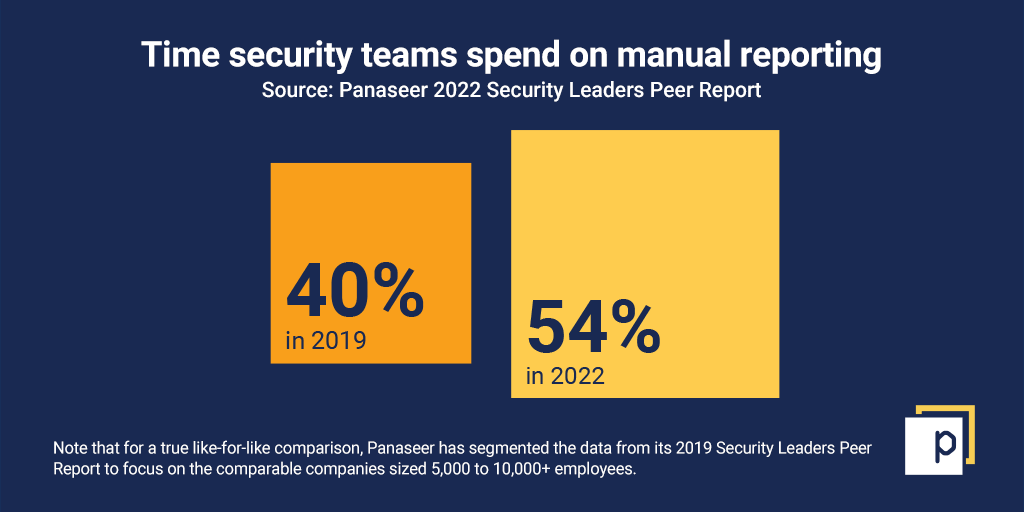 Security teams should be spending their time improving security, rather than reporting on it. Not only that, but for the people actually doing this manual reporting, it’s dull and repetitive.
Security teams should be spending their time improving security, rather than reporting on it. Not only that, but for the people actually doing this manual reporting, it’s dull and repetitive.
What do we gain from automated security reporting?
Automating security reporting brings several benefits. The more automation you bring into a repeatable data science process, the more it improves quality and consistency. When it comes to security reporting, human error can creep in. You pull together the same information every day/week/month. Download the same CSV file, apply the same filters, make the same bar charts, and build the same report. This kind of drudgery is hardly the most exciting part of cybersecurity. Automation drives consistency. When a process is automated, we know that we get accurate results every time, so we can be confident in the validity of those results and the data is not in question. Similarly, security functions always need to keep operational costs in mind. Automating processes helps reduce costs and maximise productivity by taking all the manual effort out, reducing hands in the process and required resource. And fundamentally, automating the process of security reporting gives you a consistently up-to-date “single source of truth” view of your security posture.
Seven tips for automated security measurement and reporting
Here at Panaseer we’ve been pioneering automated security measurement for seven years now, having been inaugural vendors in two relevant Gartner categories – CCM (Continuous Controls Monitoring) in 2020 and CAASM (Cyber Asset Attack Surface Management) in 2021. Through deployments with our customers, discussions with industry experts, and our own team, we’ve picked up a few things about security measurement and reporting. Naturally, all security programmes have their differences, but these seven tips can provide you with guidance on getting started.
1. Establish your objectives.
What do you want to achieve with your metrics? Based on your security strategy and risk appetite, your security reporting programme will have unique goals. These could be defined either in house or inspired by audit results. When it comes to individual metrics, there’s no point measuring and reporting something just for the sake of it. Measure something useful, report the result, and aim to improve it. I saw a blog by Phil Venables where he said: "Count what counts, not what you can count.” When it comes to your metrics programme as a whole, you will have wider business goals. Are you saving the cost of resources by reducing manual involvement? Improving efficiency? Aiming for operational excellence? Looking to improve your compliance? These are all things to keep top of mind.
2. Know your audience.
Who are you reporting your metrics to? What are the needs of each audience? And how does each of them understand value? As the security function comes under more scrutiny, more and more stakeholders need to consume information on your security posture. Our Security Metrics Research Report found that security teams are under increasing pressure to meet demand for metrics from all over the organisation, for example: IT and risk teams, regulators, auditors, the board, business stakeholders, and customers. It helps to define the needs of each audience individually. Use a common set of data points to create important insights that are relevant to each audience. But crucially, think about not just the data you’re presenting, but the language you’re using. Different audiences have different levels of understanding, so reporting needs to reflect that.
3. Align to a framework.
Frameworks, such as NIST or CIS, are an important way to align your security reporting to an industry standard. For example, the CIS Implementation Groups are a good guideline to prioritise implementation of security controls based on essential cyber hygiene. They are very useful, especially when it comes to benchmarking and tracking over time, but remember your organisation’s situation is always unique, so what a framework prioritises may not be as important in the context of your organisation. In our Metric of the Month article on cybersecurity frameworks, Phyllis Lee, Senior Director for the CIS Critical Security Controls, spoke about the integral link between cybersecurity metrics and controls frameworks. She said: “It’s not just about cleaning up once a year before an audit. Automation is key. You need to be continuously monitoring controls to make sure that your metrics are within your threshold and you’re doing what you need to do to stay compliant and stay secure.”
4. Mind your resources.
Almost every security team in the world is stretched for resources. That means prioritising and finding quick wins. There are a few factors to think about that can help. We’ve already mentioned alignment to objectives and relatability to your audience, but you should also look out for low resource cost opportunities. If you can get quick access to data that supports your objectives and is relevant to your team, prioritise that metric for a quick win. 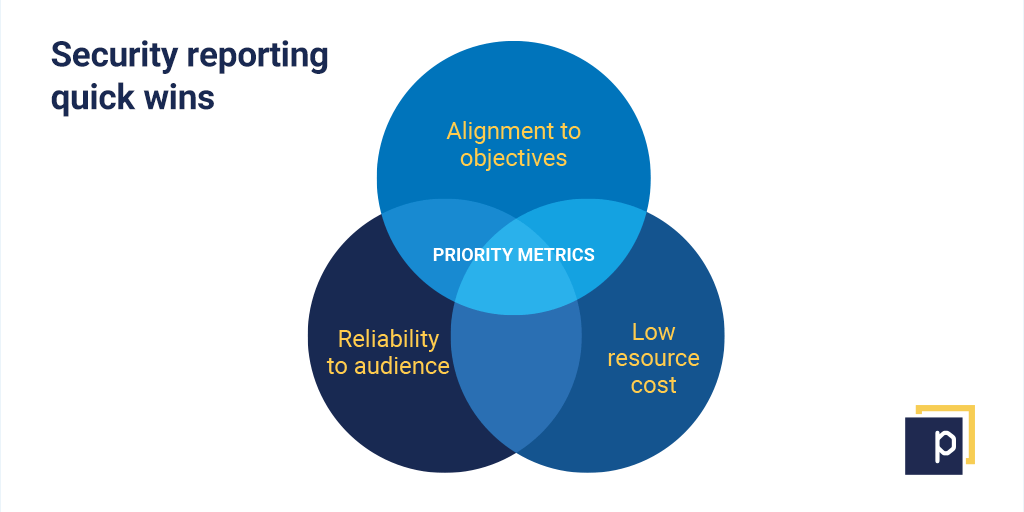
5. Don’t follow the data.
When you have a lot of tools, it can be easy to follow the data. But this is a crucial mistake. Though the data available to you can provide some direction, it is more of an indicator of what you can measure than what you should measure. As we have said, there’s no point measuring something just for the sake of it.
6. Walk before you run.
Rome wasn’t built in a day, and neither was an automated security measurement programme. Tackling the whole security measurement space is a recipe for overwhelm. A step-by-step approach outlined at a high-level can provide concrete help and guidance down the line. Start by using automation for your fundamental measures. For example, Implementation Group 1 from CIS suggests asset inventory, software inventory, and data protection. The aforementioned Phyllis Lee calls these the essentials: “You have to know what software you’re running. And you have to know where your sensitive data is.” CAASM provides direct support with CIS controls, especially around automating inventory of assets and software. Then once you are confident in those processes, you can automate more metrics, layer them up, and mature your measurement programme over time.
7. The right tools, not more tools.
We said at the top of this article that the average enterprise security team is using 76 tools. Tool bloat can cause real challenges and swamp you with data, so many organisations are looking to streamline their security toolkit. Overly complex or legacy tooling is a killer, particularly for older organisations. Every security manager will look forward to an ideal world with less complexity where there is no reliance on legacy systems. But, investing in the right tools can help. Technology like CCM (Continuous Controls Monitoring) can help aggregate data across a variety of tools to create a single source of truth. That way you can eliminate finger pointing and arguments about mismatched data from different tools. The whole organisation, across teams and functions, can rely on a single tool and read from the same page.
Automated security reporting in practice
For many years now, Panaseer has promoted the importance of automating security measurement and reporting. CCM allows enterprise security teams to do just that. Our Security Leaders Peer Report found that 20% of enterprises use CCM to automate their security measurement and reporting, while 79% are looking to implement it within the next two years. To find out more about how CCM can help put automated security reporting into practice, book a demo.


