
The fundamental cybersecurity metric: Asset inventory
‘There are so many things you could measure. When you’re running a security programme, you want to use metrics to improve your security, or at least gain some visibility into what you are dealing with. Let’s start at the beginning. One of the basic problems we’ve been trying to solve for as long as I can remember is really just understanding what assets we have. Or put as a metric: ‘Number of assets on the network’.’  In the Metric of the Month series, we discuss some of the most important and valuable security metrics with experienced risk and security pros. In this instalment, we talk to Raffael Marty, an expert in security analytics and data visualisation, and a renowned speaker and author. We caught up to discuss the basics – inventory and asset management metrics. When it comes to measuring cybersecurity, it doesn’t get more fundamental than understanding what assets you have in your environment. In fact, the first CIS control is asset inventory and it’s a key part of the NIST ‘Identify’ function.
In the Metric of the Month series, we discuss some of the most important and valuable security metrics with experienced risk and security pros. In this instalment, we talk to Raffael Marty, an expert in security analytics and data visualisation, and a renowned speaker and author. We caught up to discuss the basics – inventory and asset management metrics. When it comes to measuring cybersecurity, it doesn’t get more fundamental than understanding what assets you have in your environment. In fact, the first CIS control is asset inventory and it’s a key part of the NIST ‘Identify’ function.
What is an ‘asset’?
‘When running a security metrics programme, there needs to be a common understanding of terminology. It is such an important conversation to have, and many people underestimate that’, says Raffy. With that in mind, let’s define what we mean by an ‘asset’. To keep things simple, we’ll start by defining an asset as a device that has an IP address, for example a laptop, server, virtual machine, phone, or even an IoT device. However, more mature security programmes may increase the scope of assets to include applications and people. We’ll address expanding the definition of an asset later.
Why is it important to know how many assets you have?
You need to understand how many assets there are in your environment because almost everything else you measure has a relationship to the number of assets. Absolute numbers are not necessarily very meaningful, so the total number of assets is a baseline that provides context for your other metrics.
‘You need to understand how many assets there are in your environment because almost everything else you measure has a relationship to the number of assets’, says Raffy. Part of what makes a good metric is that it needs to be presented in context: ‘Absolute numbers are not necessarily very meaningful, so the total number of assets is a baseline that provides context for your other metrics.’ To give an example: ‘If a metric says there are 100 vulnerable devices on our network, is that good or bad? If you have 100,000 devices, it’s good. If you have 101 devices, it’s really bad.’ The simple baseline metric is purely ‘how many devices are on the network’. It is a powerful metric as it always provokes more questions: ‘How many devices do I have today? More or less than yesterday? What are the new ones? What dropped off? Who owns those? What about devices that are turned off? They should still be in the inventory. But how do I know if that device is going to come back? Has it been decommissioned?’
What are some of the challenges with establishing a good asset inventory?
In a Metric of the Month panel discussion, Raffy led our panelists in discussion around the challenges with asset inventory: https://www.youtube.com/watch?v=LF0mznLJ0f8&ab_channel=Panaseer
You could challenge any company right now to prove that they have an up-to-date asset inventory and 99% would fail.
‘You could challenge any company right now to prove that they have an up-to-date asset inventory and 99% would fail’, says Raffy. Why is that? ‘Even looking around your house, your device inventory is constantly changing. There will be several laptops, your iPad, smart TV, Alexa, your kids’ Nintendo. Maybe an older work laptop in a drawer somewhere. There are various widgets and gizmos that will pull an IP address. Phones are coming in and out. You had a barbecue the other day – who knows how many people logged into your guest Wi-Fi?’ Even in this very simple network, it’s hard to keep track of everything. ‘At the larger scale of a company, or a multi-national enterprise with thousands of employees, it becomes exponentially more difficult. Inventory is constantly fluctuating.’ While there are tools out there that can help, they aren’t always in play: ‘Unfortunately, a lot of people still track their inventories in Excel spreadsheets. There is more uptake of asset discovery tools that actively scan the network and look at log files or network captures to see what IP addresses are alive and work out what assets are behind them. Sometimes you will see companies using a CMDB or managing everything in Active Directory, but there are still a lot of hand-cobbled-together solutions out there’.
How can you start to improve your inventory?
For a less mature security function, Raffy advises that you start simple. ‘I wouldn’t start with trying to find every single asset on the network in real-time. Don’t boil the ocean. Start somewhere that matters – your most critical network. Find out what’s really in that network compared to your last documented state. Then put controls in place to know when something changes’. Once you have the riskiest network in your organisation under control, expand from there to slowly mature your metrics programme.
What does ‘good’ look like?
‘That’s a hard question,’ says Raffy. ‘What you are really asking is: how do you know whether the number of assets on your network is correct? ‘The challenge is that you don’t know what you don’t know. And that uncertainty is what you need to get a grip on. And like we said before, you might not get to a cross-organisational 100% correct metric. Start small.’
How can Continuous Controls Monitoring help inventory and asset management metrics?
Introducing Continuous Controls Monitoring (CCM) technology is a great way to get an up-to-date inventory and asset management metrics, and then build on that to develop a more mature and high-quality security measurement programme.
Expanding your definition of ‘asset’
CCM brings value by mapping your organisation, building a graph of all the relationships between assets and linking them all together.
At the beginning we defined an asset as a device that has an IP. In the context of CCM, you expand your definition to include not just devices, but also people, applications, accounts, and more – because a device will have a relationship with people, applications, accounts and more. ‘CCM brings value by mapping your organisation, building a graph of all the relationships between assets and linking them all together’, says Raffy. In addition, you start assigning attributes to the assets. Who owns this device? What other devices do they use? Do they have access to business-critical applications? Does their device have the latest patches? These kinds of insights are really valuable.
Automation
CCM is a technology that, put simply, automates security metrics and measurement. The first step of which is automating the creation and maintenance of a complete asset inventory. Raffy provides an example about a company he worked for trying to fix their inventory: ‘Our CISO was running an asset discovery project. We looked at all the IP addresses we could find on the network, and basically just asked: ‘what are they?’ We thought we had 8,000 assets. It turned out we had 10,000. And we had no idea about the asset type or owner of 40% of those. ‘We had to email people in the company to find out who owned each IP address. Someone would respond, saying it’s a server with a specific function. Did they still need it? If yes, we added it to the inventory. If not, we shut it off. But there were devices that no-one claimed. So, then we looked at lines of communication between devices, found a link to an owner, perhaps it was part of a group. Did they still need it? And so on. Sometimes, though, we just didn’t find an owner. ‘Doing this kind of manual discovery is really common, and it’s a long process.’ If you can automate this process, it saves so much time, effort, and resource for the team fixing your asset inventory.
The interesting thing about CCM is that it brings together different data sources and different knowledge repositories. The more the better. That’s where you can get extra context.
Additional context
Earlier we mentioned the importance of context. ‘The interesting thing about CCM is that it brings together different data sources and different knowledge repositories’, notes Raffy, ‘the more the better. That’s where you can get extra context’. You can see which of these assets are managed or unmanaged. You’ll be able to see not just the number of devices, but device type, operating system, whether there’s an endpoint agent running, who is logging in, the applications running on it, patch levels, where it’s located, what business unit it belongs to, and so on. This level of context is valuable when it comes to understanding your estate and the risks that each asset holds. Your inventory and asset management metrics might look something like this: 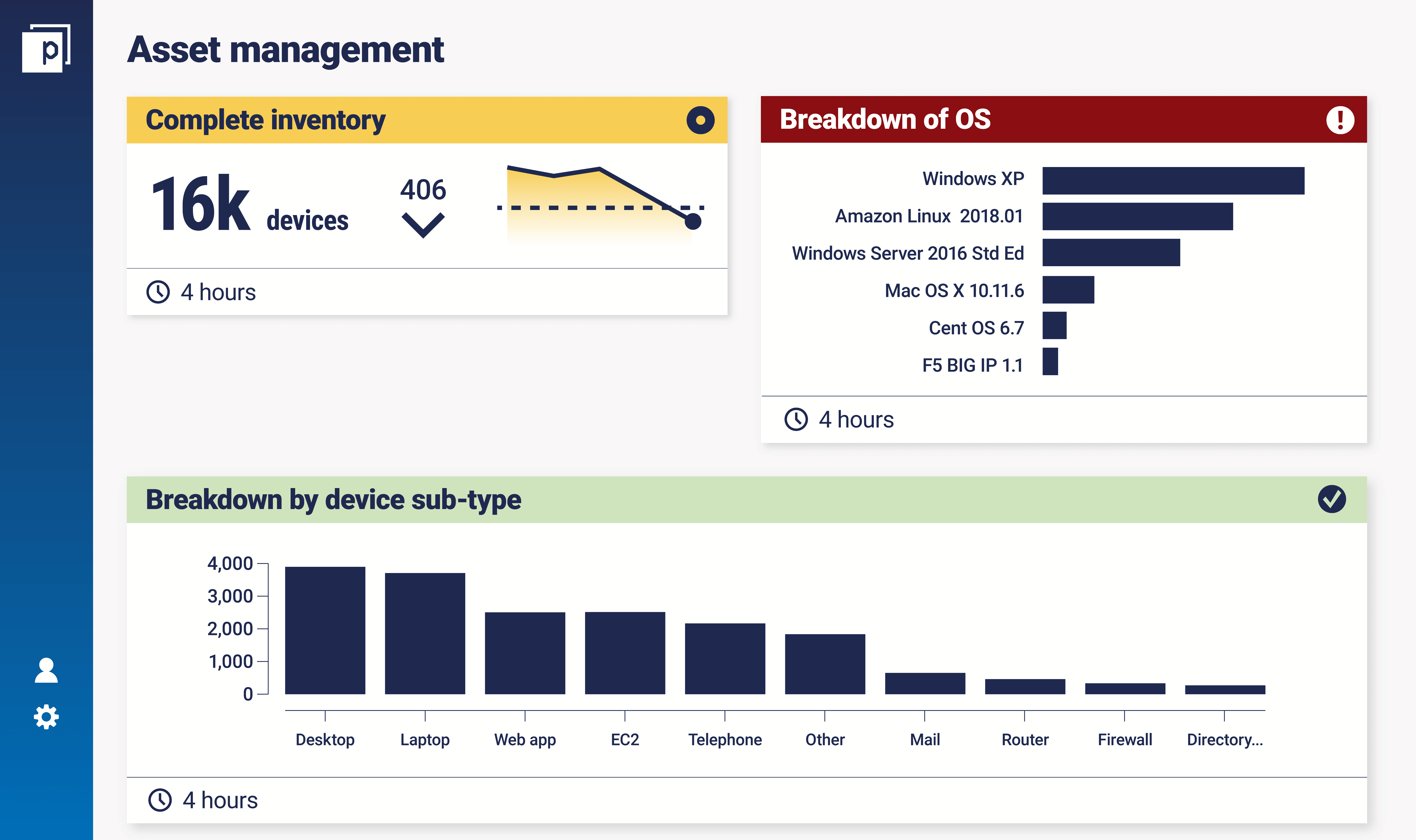
Controls
Once your inventory and asset management metrics are up-to-date, they become the list of assets you need to protect through your security controls. Raffy used an analogy of it being like a three-layered cake: ‘The bottom layer is your assets – you need to discover the assets first to form your foundation. The middle layer is your control framework – these are the knobs and switches you can control to try to create an impact. The top layer is the risk that you are trying to reduce.’ It’s a good, simple model to use. CCM lets you monitor controls on assets, seeing what controls are attributed to them versus what controls should be active. This reveals controls coverage gaps, showing you where you need to remediate to raise the baseline security posture of the organisation. ‘As you progressively get more detailed with your inventory and asset management metrics, you can reach a level where you track controls over time’.
The bottom line
While an up-to-date asset inventory can be difficult to obtain, understanding the assets you have in your environment is absolutely fundamental to any security metrics programme because:
- It’s key to understanding almost every other metric.
- It's a starting point to explore further with deeper questions. What’s the asset type? Who owns it? What operating system is it running?
- It develops into the building blocks to understand where your security controls are in place and where they are missing. Then you can start to raise the baseline security posture of the organisation by remediating those gaps. This can be supported by CCM.
‘There are so many things to consider when trying to understand this apparently basic metric of how many assets are on your network. I find it fascinating that such a simple metric leads to so many advanced and useful conversations’, says Raffy.

