
Metric of the Year: 2022’s top cybersecurity metrics
Someone thought it would be fun if I wrote a “12 metrics of Christmas” blog. I got as far as “partridge in a PAM tree” and decided to do this instead. Over the past year, there have been some great contributors for our Metric of the Month series, exploring metrics that have taken us across the breadth of security measurement.
To round out the year, we’re highlighting the most insightful. Based on feedback from colleagues, fans, and Google analytics, here are the top three metrics of 2022.
1. Metrics for the new CISO
Our nine essential cybersecurity metrics for the new CISO blog from early 2022 became an overnight sensation. So much so that someone mentioned it at our FS-ISAC booth a few weeks later. If only I’d been there.
The CISO role is one of the most challenging in both cybersecurity and business, so when you’re new in role you want to learn from people who’ve done it before. I interviewed one such person, who gave excellent advice when it comes to metrics.
The contributor, who asked to remain anonymous, said you need to get an understanding of the organisation's attack surface from a low-budget outside perspective. And that’s before you start. Or even before your interview. If she were so inclined, “what could my mum find and exploit?” Then we explored the actual metrics to measure when you join a new company. We have a few of the usual suspects, such as asset inventory, multi-factor authentication, and privileged access.
For a broader picture of the metrics we discussed in this article, here is the mocked-up CISO dashboard from our platform:
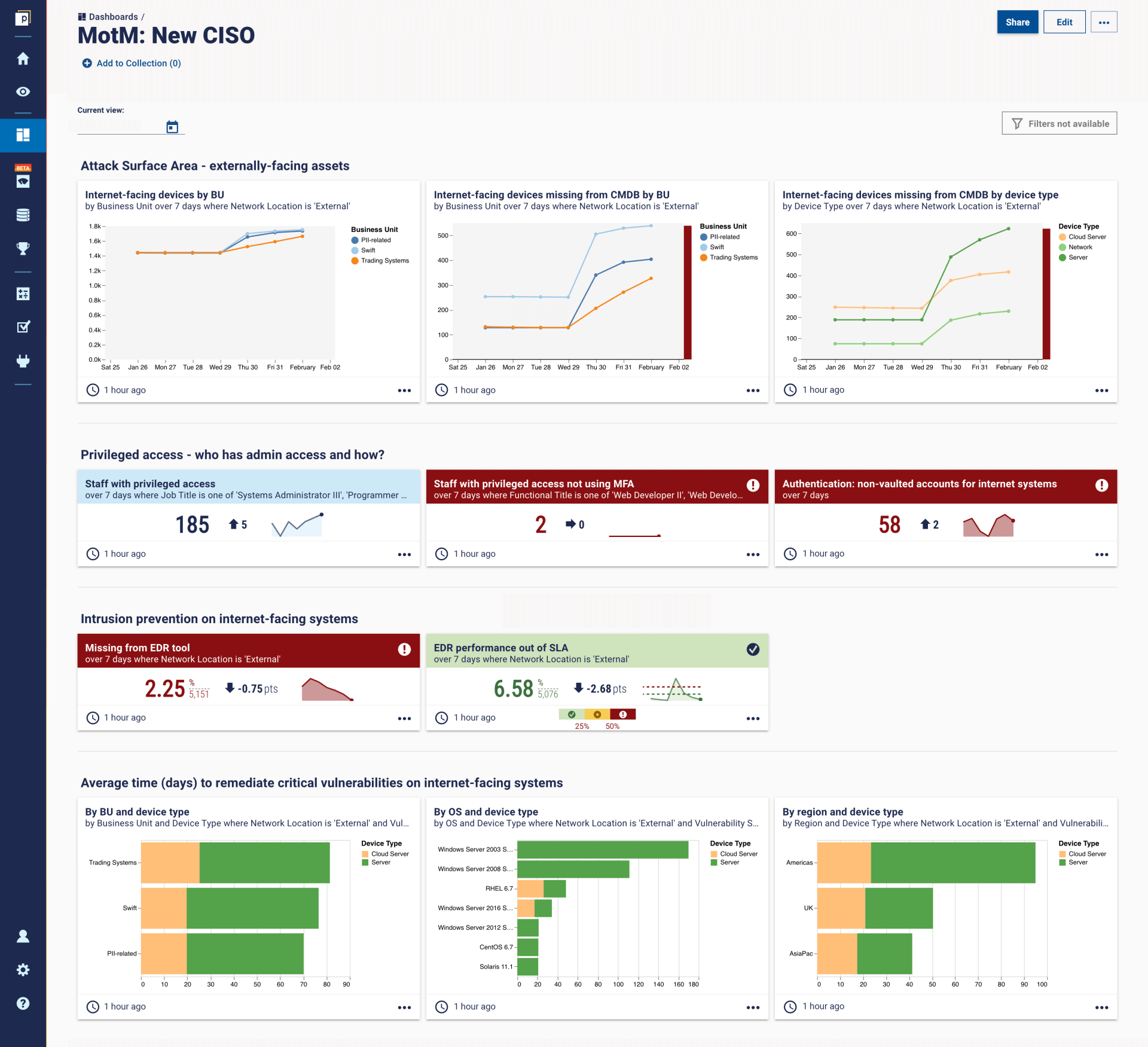
This interview provided a great tip: focus your measurement on internet-facing systems. As a new CISO, potentially creating a new measurement programme, you'll have a list of important things to do. Chief among them: understand the attack surface and prioritize your most important assets.
Focusing your metrics on internet-facing systems allows you to do both. Inventory metrics about internet-facing assets give you your attack surface, while also showing you the most important systems to prioritise for protection and remediation.
2. Cyber hygiene metrics
The Microsoft Digital Defense Report found that cyber hygiene protects against 98% of cyber-attacks. So, who better to discuss cyber hygiene metrics with than Stuart Aston, National Security Officer at Microsoft UK? In seven cybersecurity metrics for basic cyber hygiene, Stuart explained that fundamental controls can help stop most attacks, especially the commodity ones.
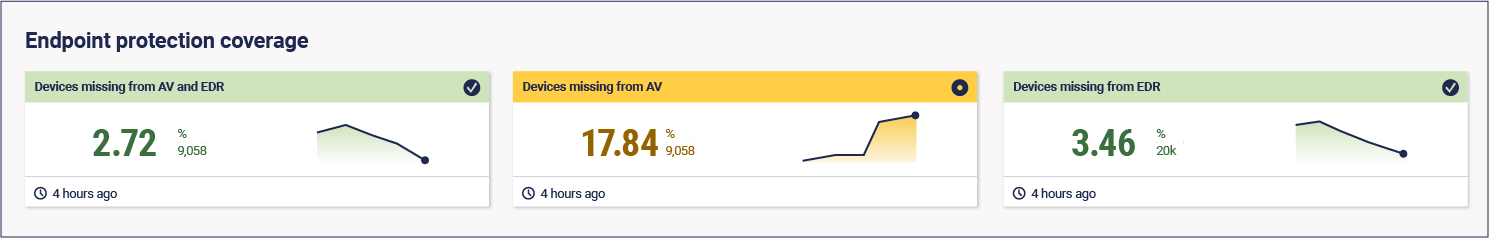
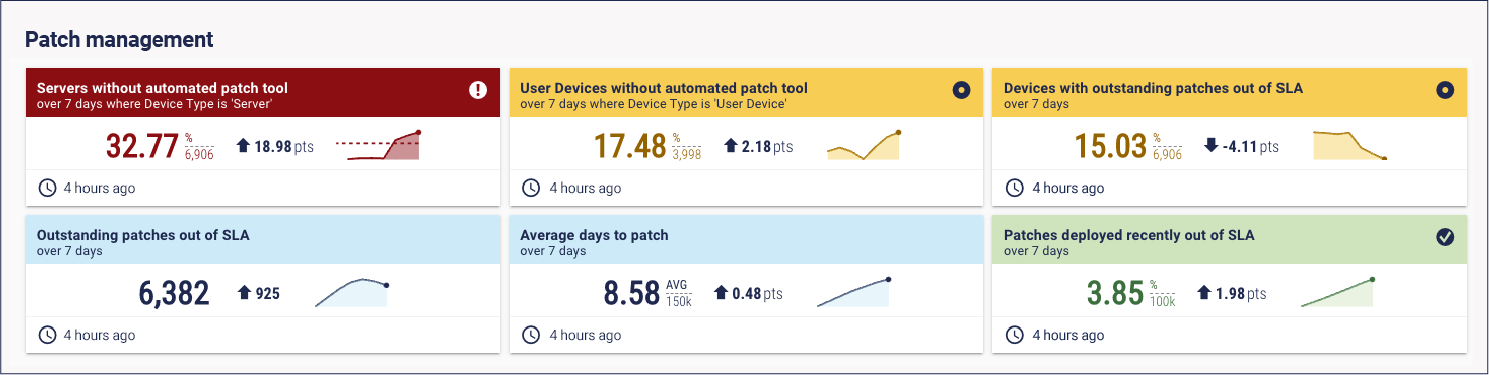
And cyber hygiene metrics are all about measuring the effectiveness of those controls. He shared key metrics for seven areas that enterprise security programmes will likely already address: asset management, anti-malware, privilege, multi-factor authentication, patching management, permitted programs, and data security. Here are a few examples: Inventory completeness (in this case, % devices in the CMDB)
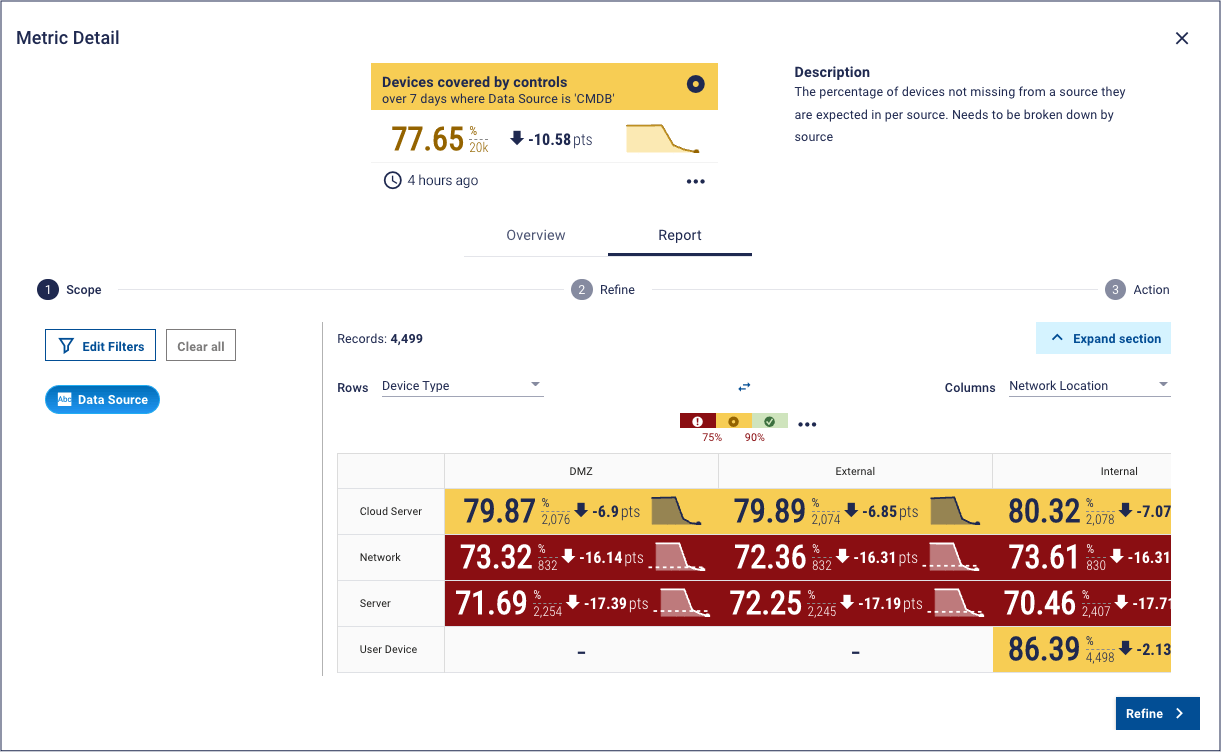
Anti-malware tool coverage
Percentage of critical and high vulnerabilities patched within seven days
3. Threat modelling metrics
Threat modeling was a bit of a departure from our regular programming, but our 11 metrics to empower your threat modeling program article with Adam Shostack was as well-received and insightful as any other article this year. Adam shared an approach to measuring the effectiveness of threat modeling that focuses less on data sources and tooling, and more on asking key questions:
- What are we working on?
- What can go wrong?
- What are we doing about it
- Did we do a good job?
In threat modeling, it isn't just about the tools you’re using, it’s about cultural change. “Culture eats strategy for breakfast. If we can change engineering and development so that those four questions become innate and automatic, you infuse safety and security into the culture and therefore, the technology you’re building.”
The final word
There are a few types of metrics that have really jumped out this year. Specifically, the articles on both new CISO and cyber hygiene metrics highlight the importance of:
- Inventory and CMDB
- MFA
- PAM
- Patch and vulnerability management
It’s no coincidence. These are some of the absolute fundamentals of any good security measurement program. So, if these metrics aren’t in your letter to Santa this Christmas, maybe they should be.

