
How CAASM improves your IT asset discovery and security posture
Enterprise security teams face huge obstacles in understanding their complete attack surface - CAASM (Cyber Asset Attack Surface Management) could change things. Effective security is built on good visibility.
CISOs and their teams can only protect what they can see, yet most organizations don’t have a complete picture of their IT asset inventory and attack surface.
There are many factors contributing to this problem: legacy systems, hybrid working, complex organizational structures, shadow IT… we could go on. It ultimately means that the average enterprise security team struggles with asset visibility and doesn’t know where they have vulnerabilities. A new technology category is set to change all that. Gartner coined the term CAASM – Cyber Asset Attack Surface Management — in its 2021 Hype Cycles for Security Operations and Network Security.
But why is CAASM better than existing IT asset management tools and how does it improve your security posture?
What is CAASM?
CAASM is a security automation and data analytics platform that combines data from vulnerability and endpoint tools, as well as other security sources, to give organizations total visibility of their asset inventory and uncover vulnerability control gaps. It uses automated security metrics, including business context, to enable security teams to fully understand their attack surface and prioritize remediation against vulnerabilities that carry the most business risk.
Why is asset visibility a problem for security teams?
Asset visibility is a critical challenge, particularly in large enterprises. The rapid and permanent shift to hybrid working has brought many benefits, but also created a headache for security teams trying to keep track of who is connecting to their network and on what devices.
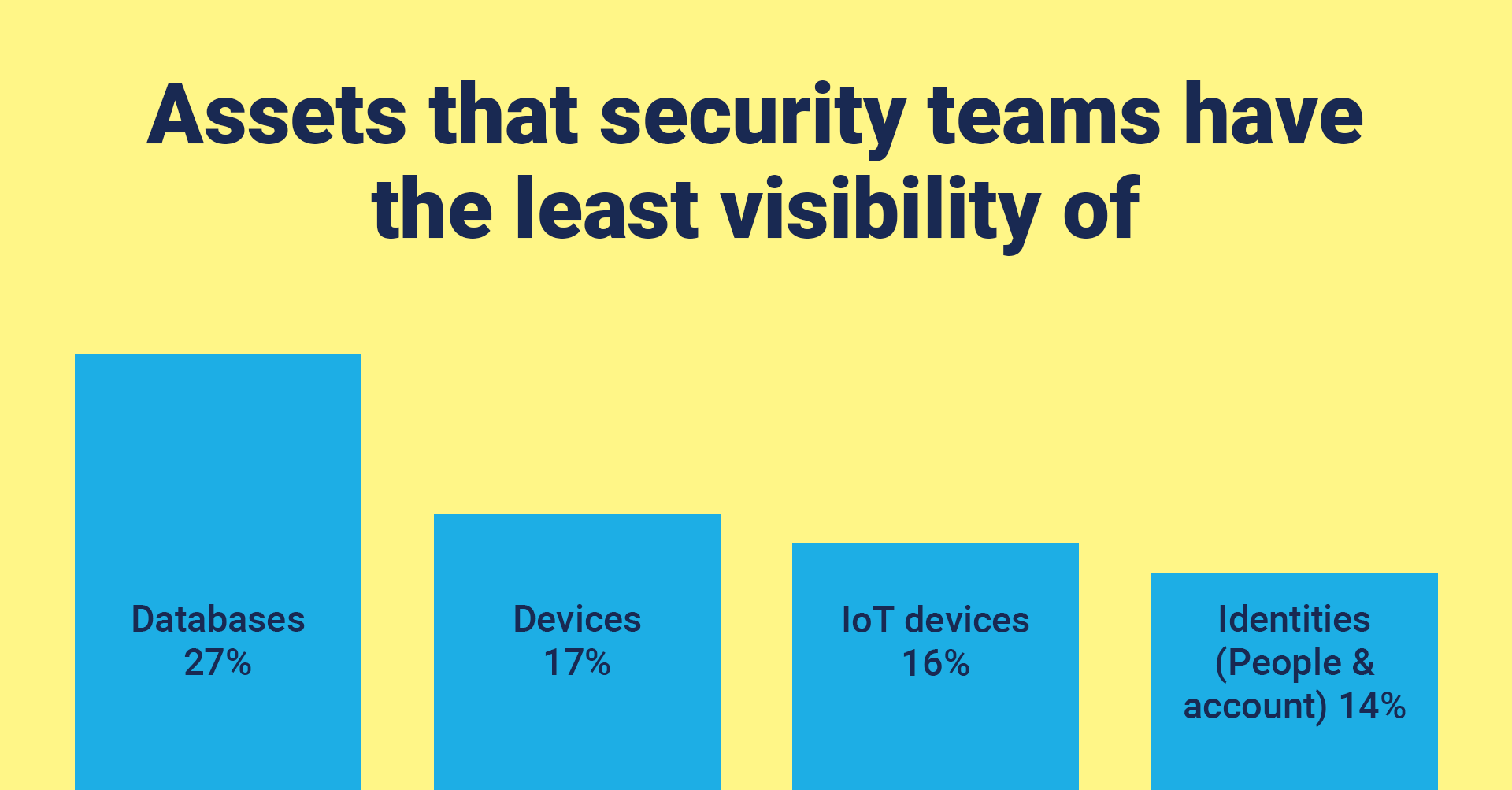
This new stress combines with ongoing challenges of getting visibility across a complex enterprise that could be made up of different legal entities, relying on an IT architecture cobbled together from cloud services and legacy systems, potentially split across different locations and geographies. Our 2022 Security Leaders Peer Report found that databases, devices, and identities were the assets over which security teams have the least visibility. Gaps in visibility lead to gaps in vulnerability controls, putting the organization at increased risk of a breach.
The fact is that many IT asset management tools aren’t capable of providing an accurate inventory in a modern enterprise. Not only do they present a static, out of date and incomplete view of an environment, but it often requires manual effort to correlate the data against other tools.
To get a more complete view of their attack surface, security teams need automated data processes that provide a dynamic view of their IT asset inventory and vulnerabilities.
How does CAASM improve IT asset discovery?
With CAASM, security teams have much greater visibility and insight into their assets and vulnerabilities. The key difference is that IT asset discovery isn’t left up to one or two asset scanners, which might not be configured properly or are failing to scan the entire environment. Instead, data is taken from across endpoint and vulnerability tools, as well as Active Directory, CMBD, and HR systems, and brought together in a single centralized view.
This is achieved through data science techniques that correlate data from different sources to remove duplicate records and create a golden master record, which is a single source of truth and a more complete inventory of assets, devices, and people. It means security teams can be confident they have fewer blind spots and a more accurate understanding of their attack surface, including cloud and shadow IT. As a result, they won’t be caught out by vulnerabilities in systems they didn’t even know existed.
How does CAASM improve your security posture?
CAASM’s benefits extend beyond providing greater visibility of your attack surface. Enhanced IT asset discovery is just the starting point on an organization’s path to a more data-driven, automated security program. Rather than relying on a ‘point in time’ reading, security teams can continuously monitor their vulnerability controls and quickly spot coverage gaps. Again, this provides far better monitoring than a traditional SIEM system, which can only scan assets it knows about.
Often the SIEM isn’t reporting any problems, but its visibility is obscured by shadow IT. Our own CAASM platform presents this data in user-friendly dashboards, as well as allowing customizable and automated data queries.

However, while uncovering vulnerability control gaps is valuable, security teams still face the challenge of deciding which issues to fix first. Our CAASM platform solves this problem by enriching the data with information about business context, criticality, and asset ownership.
This means security teams can better prioritize remediation efforts on vulnerabilities that carry the most business risk and hold people accountable. Finally, CAASM enables organizations to improve their security posture by proactively reducing their attack surface. For example, security teams can identify devices that are missing from security controls coverage, have vulnerabilities, or are at the end of life. They can then either implement controls, patch them or remove them from being externally facing, thereby reducing their cyber attack surface.
Who's responsible for remediation?
The issue of accountability is important when trying to deliver accurate reporting of improvements to your security posture. Security teams typically struggle to understand who’s responsible for a particular asset or system and rely on service desk ticketing to prove whether a vulnerability has been patched.
This is obviously open to human error. With CAASM, data is taken from the underlying tools so security teams can evidence whether a vulnerability has genuinely been fixed. When combined with historical data, this gives teams the ability to understand and measure remediation burn-down rates, which has clear benefits for security posture and audit reporting.
Foundations for proactive security posture
CAASM delivers immediate benefits for your security posture, bringing greater visibility, prioritised remediation and more efficient reporting. It also creates the foundations for a broader transformation of your security programme, enabling you to adopt a proactive approach with Continuous Controls Monitoring (CCM). The journey from CAASM to CCM
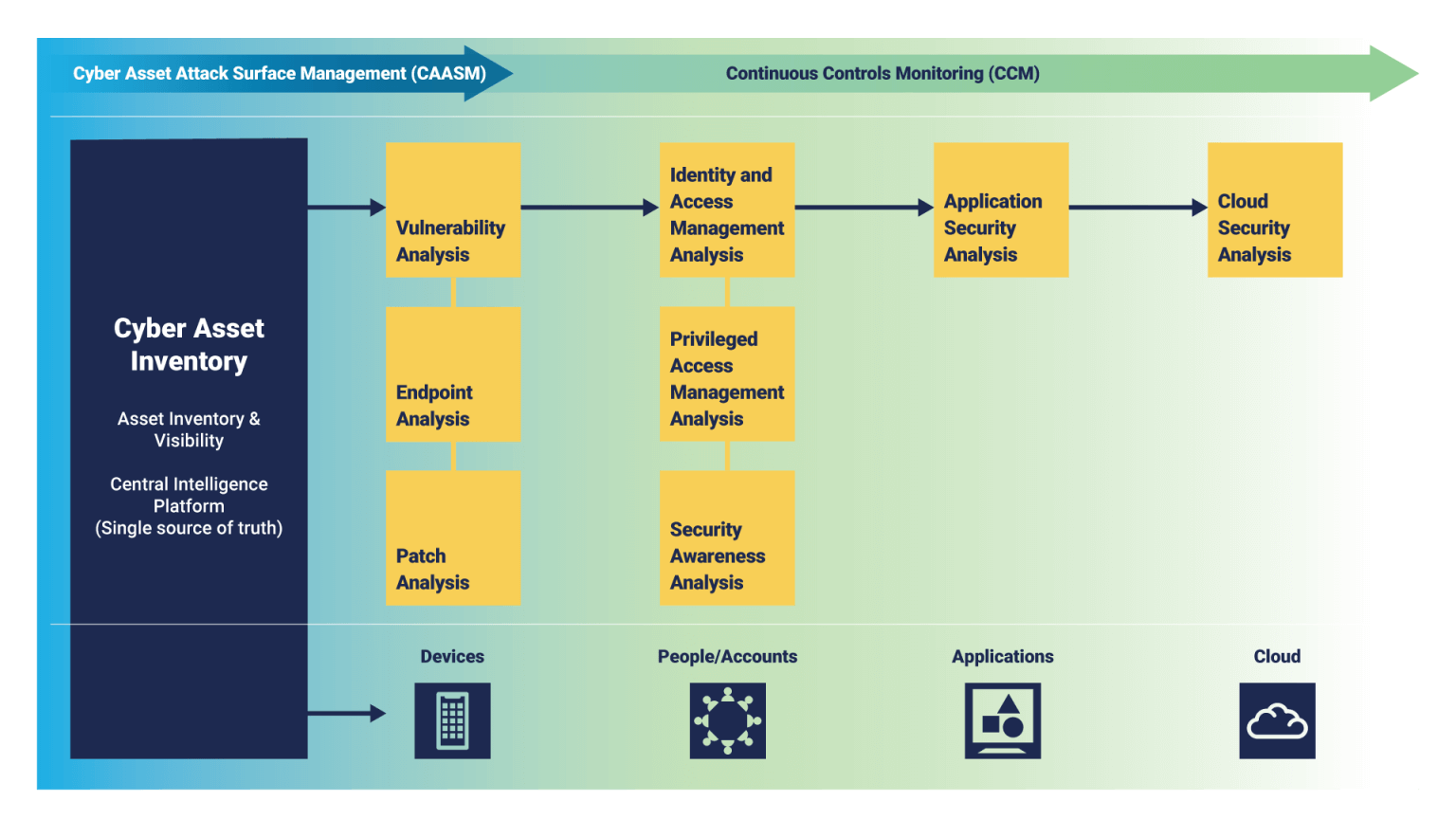
While CAASM brings together vulnerability and endpoint analysis, CCM combines data from all your security tools to give total visibility, accurate metrics, and reporting across nine security domains.
Our 2022 Security Leaders Peer Report shows that security teams are currently grappling with more than 76 security tools and spend more than half their time (54%) creating manual reports. A platform that brings all that data together, enriches it with business context, and automates reporting has the potential to make security teams more efficient and deliver tangible improvements to your security posture.
Book a demo to find out how CAASM gives a more complete view of your IT asset inventory and improves your security posture.


