
How CISOs can tackle ‘tool sprawl’
‘Tool sprawl’ isn’t unique to cybersecurity. Just about every department in an enterprise environment will rely on a number of different tools and applications to get the job done. But the security product market is particularly fragmented.As security threats and vulnerabilities have evolved over time, point solutions have been developed to address specific problems. But these solutions don’t always work well with other tools, creating silos within the IT and security estate.Each new tool that’s introduced brings with it more complexity and more maintenance. And because they produce data in different formats and languages, gathering insights across multiple different tools can create a lot of additional legwork.In fact, our Security Leaders’ peer report has found that most security teams are running more than 50 different tools. For 70% of respondents, the data gathering, formatting and reporting process was manual, which resulted in teams spending 36% of their time producing reports.The adverse side-effects don’t end there. Forrester have found that the sheer abundance of security tools in play can give security teams a misplaced sense of confidence in their security posture. Having plenty of tools doesn’t guarantee security. In fact, the additional work created and the lack of visibility created by siloed tools and processes can undermine security, instead of improve it.
Having plenty of tools doesn’t guarantee security. In fact, the additional work created and the lack of visibility created by siloed tools and processes can undermine security, instead of improve it.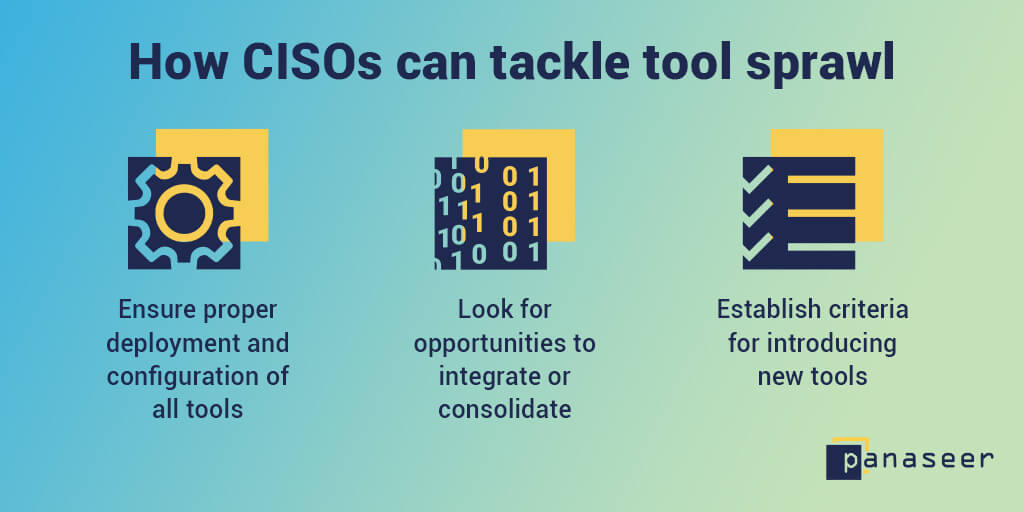 1 - Ensure proper deployment and configuration of all toolsBefore you can find opportunities to consolidate and integrate, you need to be sure that all your tools are doing what they’re supposed to by ensuring they are deployed and properly configured. Then you will be able to assess whether they’re delivering the ROI to justify the business case for running them.Ensuring optimal deployment and configuration of tools requires visibility of every asset in the estate. After all, if you can’t see what you’re trying to defend, you can’t deploy controls against those things.IT infrastructure is always evolving. Digital transformation, shadow IT and BYOD have all contributed to creating a constantly shifting IT environment for security teams to manage. As a result, most tools need to be checked on a regular basis to ensure they are still doing what they’re supposed to.Continuous monitoring of controls gives teams centralised visibility of assets and controls coverage gaps. Security teams can then take the necessary steps to address these gaps, ensuring that all tools are being put to proper use.For instance, anti-virus needs to be updated and configured regularly to receive the latest anti-virus signature updates. Without these, they won’t be scanning for the latest malwares and they may not be scan at the frequency outlined in your policy.
1 - Ensure proper deployment and configuration of all toolsBefore you can find opportunities to consolidate and integrate, you need to be sure that all your tools are doing what they’re supposed to by ensuring they are deployed and properly configured. Then you will be able to assess whether they’re delivering the ROI to justify the business case for running them.Ensuring optimal deployment and configuration of tools requires visibility of every asset in the estate. After all, if you can’t see what you’re trying to defend, you can’t deploy controls against those things.IT infrastructure is always evolving. Digital transformation, shadow IT and BYOD have all contributed to creating a constantly shifting IT environment for security teams to manage. As a result, most tools need to be checked on a regular basis to ensure they are still doing what they’re supposed to.Continuous monitoring of controls gives teams centralised visibility of assets and controls coverage gaps. Security teams can then take the necessary steps to address these gaps, ensuring that all tools are being put to proper use.For instance, anti-virus needs to be updated and configured regularly to receive the latest anti-virus signature updates. Without these, they won’t be scanning for the latest malwares and they may not be scan at the frequency outlined in your policy. Feel free to get in touch on Twitter or LinkedIn to learn more about anything mentioned in this article. And request a demo to learn more about how CCM can help you maximise the value of all the tools in your IT and security estate.
Feel free to get in touch on Twitter or LinkedIn to learn more about anything mentioned in this article. And request a demo to learn more about how CCM can help you maximise the value of all the tools in your IT and security estate.
 Having plenty of tools doesn’t guarantee security. In fact, the additional work created and the lack of visibility created by siloed tools and processes can undermine security, instead of improve it.
Having plenty of tools doesn’t guarantee security. In fact, the additional work created and the lack of visibility created by siloed tools and processes can undermine security, instead of improve it.What are vendors doing to tackle tool sprawl?
There are some efforts within the industry to address these issues. The Open Cybersecurity Alliance is a group of “like-minded cybersecurity vendors, end users, thought leaders and individuals who are interested in fostering an open cybersecurity ecosystem.”The alliance’s goal is to establish common data standards and procedures to help vendors develop tools that support, or are closer to, ‘out of the box’ interoperability.Consolidation - either by way of acquisition or by vendors rolling their own tools into one another - is another strategy. But both of these things take time. And in the meantime, CISOs and their teams are struggling under the weight of all the tools they have acquired.What can CISOs do today to tackle tool sprawl?
In this post, we’ll look at how CISOs and their teams can maximise the value of their current tool set, identify opportunities for consolidation, and manage the number of new tools they add, without compromising on data integrity or security.We've broken it down into a three-step process:- Ensure proper deployment and configuration of all tools
- Look for opportunities to integrate or consolidate
- Establish criteria for introducing new tools
 1 - Ensure proper deployment and configuration of all toolsBefore you can find opportunities to consolidate and integrate, you need to be sure that all your tools are doing what they’re supposed to by ensuring they are deployed and properly configured. Then you will be able to assess whether they’re delivering the ROI to justify the business case for running them.Ensuring optimal deployment and configuration of tools requires visibility of every asset in the estate. After all, if you can’t see what you’re trying to defend, you can’t deploy controls against those things.IT infrastructure is always evolving. Digital transformation, shadow IT and BYOD have all contributed to creating a constantly shifting IT environment for security teams to manage. As a result, most tools need to be checked on a regular basis to ensure they are still doing what they’re supposed to.Continuous monitoring of controls gives teams centralised visibility of assets and controls coverage gaps. Security teams can then take the necessary steps to address these gaps, ensuring that all tools are being put to proper use.For instance, anti-virus needs to be updated and configured regularly to receive the latest anti-virus signature updates. Without these, they won’t be scanning for the latest malwares and they may not be scan at the frequency outlined in your policy.
1 - Ensure proper deployment and configuration of all toolsBefore you can find opportunities to consolidate and integrate, you need to be sure that all your tools are doing what they’re supposed to by ensuring they are deployed and properly configured. Then you will be able to assess whether they’re delivering the ROI to justify the business case for running them.Ensuring optimal deployment and configuration of tools requires visibility of every asset in the estate. After all, if you can’t see what you’re trying to defend, you can’t deploy controls against those things.IT infrastructure is always evolving. Digital transformation, shadow IT and BYOD have all contributed to creating a constantly shifting IT environment for security teams to manage. As a result, most tools need to be checked on a regular basis to ensure they are still doing what they’re supposed to.Continuous monitoring of controls gives teams centralised visibility of assets and controls coverage gaps. Security teams can then take the necessary steps to address these gaps, ensuring that all tools are being put to proper use.For instance, anti-virus needs to be updated and configured regularly to receive the latest anti-virus signature updates. Without these, they won’t be scanning for the latest malwares and they may not be scan at the frequency outlined in your policy.2 - Look for opportunities to integrate or consolidate
Integration and consolidation is about maximising the collective value of all the tools in your estate. The easier it is for your tools to share data and information, the easier it will be to create automated workflows, reducing the manual work required from your team. Solutions that can work together will leave fewer gaps, making them better able to prevent, detect and respond to security incidents.However, as security expert and Panaseer advisor Jim Doggett told Intelligent CISO last year, tool consolidation should be approached strategically:“Each security tool implemented should reduce risk to the company, be able to measure the reduction in risk and be capable of sustaining that reduction. This usually means the tool must be combined with processes and other tools to provide an end-to-end process that manages a particular security risk.”3 - Establish criteria for introducing new tools
Because integration is so important - and lack of integration so costly - interoperability should be a key factor when deciding whether or not to invest in a new tool or solution.Tools which can share data and information with other tools in your system and increase overall visibility should be prioritised over those that can not. Likewise, tools which can automate manual processes or reduce additional work should be prioritised over those that create more.You may want to create a formal policy or decision-making framework around when to introduce new tools into the environment. Jim shared some useful criteria with Intelligent CISO on this subject last year as well:As we implement security processes and tools, we need to ensure that the end solution:- Covers the entire intended landscape across the company. For example, if we are only scanning 70% of the environment for system vulnerabilities, we may not be adequately reducing risk to the company
- Provides sufficient information to act. For example, if we select a system vulnerability scanner and it provides great detail on the vulnerability and inherent risk but does not provide context to the importance to the company or context as to the owner of the system, then the tool/system is not providing sufficient information to reduce the risk sufficiently
- Lastly, it sustains the control, meaning it should automate the control and monitoring processes. Otherwise, the risk will grow again after expending efforts and monies to remediate
Continuous Controls Monitoring can provide accurate and up-to-date visibility of all security tools
There are no be-all-and-end-all solutions in cybersecurity. You’re always going to need multiple tools in order to protect the organisation and its assets. However, Continuous Controls Monitoring (CCM) can help establish visibility of all assets, controls and tools in your environment, giving you ready access to insights and metrics that can improve decision-making and speed up reporting.In fact, Forrester Consulting recently found that 91% of companies reported that a solution like CCM would have a significant or substantial positive impact on their ability to proactively identify, prioritize, and remediate risk. Feel free to get in touch on Twitter or LinkedIn to learn more about anything mentioned in this article. And request a demo to learn more about how CCM can help you maximise the value of all the tools in your IT and security estate.
Feel free to get in touch on Twitter or LinkedIn to learn more about anything mentioned in this article. And request a demo to learn more about how CCM can help you maximise the value of all the tools in your IT and security estate.

