
Continuous Controls Monitoring: Return of the Category
Gartner has issued a new Innovation Insight on Continuous Controls Monitoring for cybersecurity. This calls for a celebratory pun: Return of the Category. Jedi or King is up to you. Panaseer has been pioneering Continuous Controls Monitoring – CCM – for several years. We adopted the term in 2019 and set about evangelizing and building the category. While CCM was in use by some of the major banks, they had built it themselves. We were the first to productize CCM and make it available to the market. Since then, CCM has grown as a category, with the latest news being Gartner’s recent Innovation Insight for Cybersecurity Continuous Controls Monitoring (you’ll need a Gartner login to read it in full), including Panaseer as a Representative Provider of cybersecurity CCM capabilities. We believe CCM is solving a unique problem.
What is Continuous Controls Monitoring?
Gartner’s definition from the insight research is as follows: “Continuous control monitoring (CCM) automates the monitoring of cybersecurity controls’ effectiveness and relevant information gathering in near real time. Security and risk management leaders can improve their organization’s security posture and their own productivity by adopting this technology. “Organizations of various sizes and in different industries often suffer from resource constraints because their security and IT operational teams are drawn into manual testing of, and reporting on, controls. These controls derive from security standards, frameworks, regulatory obligations and internal policies. Regular testing and monitoring of controls is necessary to ensure they are effective and compliant. This work is not only often burdensome but also, since it is typically done in manual and piecemeal fashion, prone to error and incompleteness, and not reusable. “Process automation for managing controls and meeting compliance requirements is therefore imperative.” That’s what CCM does – automated and continuous monitoring of your organization’s security controls effectiveness to understand your security posture.
What qualifies as Continuous Controls Monitoring?
Gartner outlines four core capabilities that a CCM tool must have: 1. Data integration “A CCM tool must automatically pull and refresh metrics relating to controls’ performance from a broad range of on-premises IT, security systems and clouds. The data collected could be raw system data or already-correlated security posture information. In addition to ready-made data connectors, CCM vendors should support software development kits and APIs that enable custom integrations.” 2. Scoring and alerts “A CCM tool must contextualize and calculate collected metric-related data and present it in a summarized and graphical manner. This makes it easier to conduct statistical analysis and helps functional units beyond security and IT operational teams make risk mitigation decisions.” 3. Control content management and control mapping “A CCM tool must maintain control-related content and offer control mapping across a range of security frameworks and standards.” 4. Visualization “A CCM tool must have reporting and dashboard capabilities. The richness, currency and breadth of visualization depend on the first three sets of core capabilities.”
Benefits and uses of Continuous Controls Monitoring
If you’re reading this thinking CCM is all about using automation to understand your security posture and controls, well, you’d be half right. The high level of automation brings a range of benefits. But that’s only the start. One of the key challenges facing security teams is that they spend far too much time on manual reporting – 59% of their working week according to our 2023 Security Leaders Report. Automation reduces the need for manual effort, so not only do you reduce the risk of human error, you also free up people and resources to actually do security and remediate problems. Indeed, our latest report on optimizing cybersecurity found that security leaders see the main benefits of automation as more efficient use of resources (57%) and improved decision making (46%). Getting ahead of the backlog can help security programs shift towards a more proactive approach to cybersecurity. This saves money in the long term, as it allows you to stop preventable breaches by fixing issues before they become bigger more expensive problems. 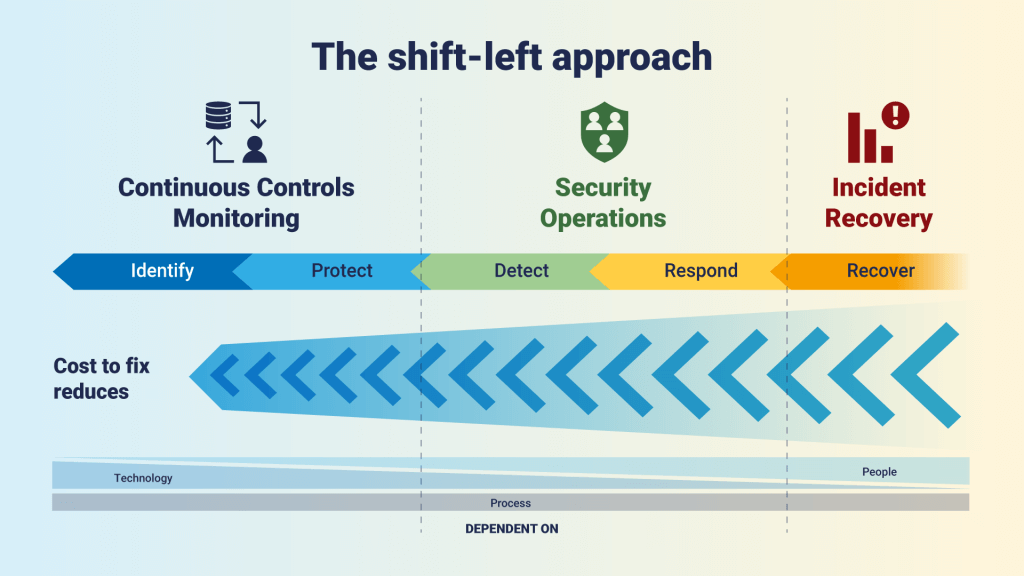 Where security teams are often left scrambling to answer questionnaires about their security controls for audits, compliance, regulations, cyber insurance, and more, a CCM platform puts all that information at your fingertips. There’s no need for a long-winded mission to go out and find the answers. This helps reduce the cost of independent external audits by sharing evidence and avoiding the assessments typically performed by consulting firms. Having access to reliable evidence of your security posture can also help to boost the reputation of your organization in the eyes of regulators, auditors, insurers, and even customers. Panaseer users have often cited CCM as a source for credibility with a range of stakeholders. Beyond automation, though, there is so much more CCM can help with. Here are the primary and secondary use cases that Gartner shared in the insight report:
Where security teams are often left scrambling to answer questionnaires about their security controls for audits, compliance, regulations, cyber insurance, and more, a CCM platform puts all that information at your fingertips. There’s no need for a long-winded mission to go out and find the answers. This helps reduce the cost of independent external audits by sharing evidence and avoiding the assessments typically performed by consulting firms. Having access to reliable evidence of your security posture can also help to boost the reputation of your organization in the eyes of regulators, auditors, insurers, and even customers. Panaseer users have often cited CCM as a source for credibility with a range of stakeholders. Beyond automation, though, there is so much more CCM can help with. Here are the primary and secondary use cases that Gartner shared in the insight report:
- Track and report on control performance.
- Identify control gaps.
- Support security audit.
- Monitor cyber risk.
- Improve security operational efficiency.
- Maintain compliance with regulations and industry standards.
- Enhance IT asset inventory.
- Support DevSecOps.
- Inform threat intelligence management.
That’s quite a lot of use cases, still but doesn’t really cover everything CCM can do. From Panaseer’s perspective, we think some of the most important things that CCM helps with are also:
- Prioritization of risk: When you identify gaps in security controls, you fix them. But where do you start? Our approach is to combine identification of control gaps with business context to prioritize remediation.
- Business context: It’s crucial to helping prioritize remediation. Ingesting and correlating data from tools across security and the wider business means you can identify more information on each asset. This could be geographical location, business unit or process, ownership, and more. This insight lets you prioritize remediation more effectively. If you see a critical vulnerability that could impact BAU, that should be prioritized.
- Data trust: When you talk to enough people about security data, you often hear the question: “If my data is garbage, won’t we just get garbage data out the other end?” One of the biggest issues CISOs have is that they don’t trust their data. Trust is the basis of their credibility with the wider business. Panaseer creates data trust by providing transparency, accuracy, and speed throughout the data lineage process.
- Security controls accountability: The platform finds every asset; identifies any problems on that asset, such as missing protections or vulnerabilities; shows who owns or manages it; and then lets you see any other devices they own/manage. This provides greater accountability and responsibility for fixing the problems on any given asset, all supported by your own business logic.
What are the risks of Continuous Controls Monitoring?
In this section, we aim to explain how Panaseer addresses the risks highlighted in Gartner’s research. Chief among the risks is that a CCM tool doesn’t directly fix problems. It gives visibility and understanding of your security controls and posture. If you don’t act on the information, you can’t improve. Currently, CCM tools don’t have automated remediation (although ticketing and alerts are used), but Panaseer's approach to remediation is three-fold. First, the platform provides insight on what problems to fix first with remediation prioritization. Second, the Remediation Objectives feature tracks remediation over time, measuring the burndown rate to ensure issues are being fixed within agreed SLAs, which can be particularly useful when remediating high priority zero-days. Finally, we also have a dedicated Security Performance Management team who help our customers improve their security posture with guidance, best practices and actionable recommendations.
Where does CCM fit in the organization?
The Gartner research says: “Monitoring systems like CCM tools continuously provide control status and security posture information, which needs to be consumed. If this output is not captured and used, problems are not resolved. If the monitoring system is not embedded in the organization’s processes, the investment will be a failure.” However, as discussed above, the range of benefits that CCM supports means it can help multiple aspects of the business. This graphic explains how Panaseer’s CCM platform is strategically positioned to support GRC, TDR, and security optimization: 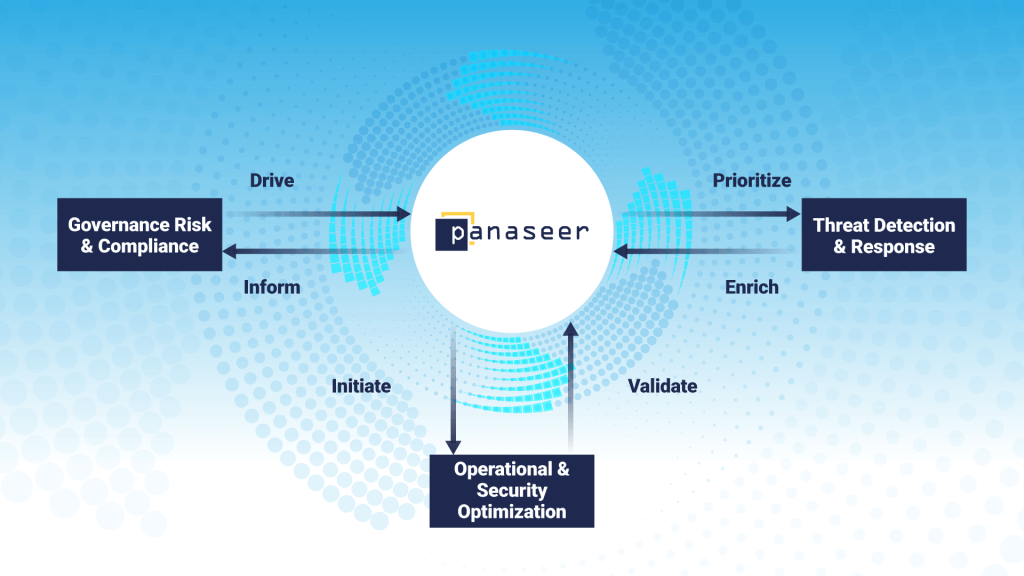
Data connectors
There may be some questions around access to data. Panaseer’s flexible data schema means it can connect to any data source with an export capability, such as an API, that aligns to a security area covered by our platform. This includes a range of security tools, such as CMDB, vulnerability, EDR, patch tools, and more. It’s also essential to ingest data outside of cybersecurity, such as business or HR tools, to enrich the data set with business context. This gives you unique insights that provide a more complete view of your controls and business risk, plus more effectively prioritizing risk remediation.
Data trust
The Gartner research says that “CCM technology cannot solve problems with the data quality of the originating tool or other source. Those responsible for controls must manage them in such a way that reliable statements can be made about controls’ effectiveness. Security teams need to work with clearly assigned control owners to improve data’s usability.” But Panaseer can be used to solve the data quality challenge, as well as supporting efforts around the responsibility and accountability of cybersecurity controls. Every organization that has used Panaseer has found assets they didn’t know about. Some have found only a few, some have found many thousands. By aggregating data from a range of sources, deduplicating, applying business logic, and adding requisite filters, the platform creates an inventory of total unique active devices. This can then be used to fix the gaps in the original data sources. For example, if your original data source is a CMDB (and many CISOs don’t fully trust their CMDBs) you may find it is only 70% complete, so you can run a campaign to populate it to align with Panaseer’s unique asset inventory. Data trust is also brought into question. Gartner states that: “Aggressive data correlation can lead to misleading statements. From the user’s perspective, calculations must be transparent about the correlation of data. Also in consequence, when calculating compliance status based on a control framework, some flexibility must be built in to allow for ad hoc corrections.” Panaseer gives customers total data transparency, so they can understand the data science and entity resolution engine that go on under the hood. This transparent data lineage leads to trust, accountability, and credibility.
Overlap with other tools
This has been one of the key challenges that CCM vendors have faced in the last few years. While Cyber Asset Attack Surface Management (CAASM) is a valuable tool for security teams to understand their attack surface, discover their assets, and basic control gap analysis, it represents only a small part of the full range of benefits offered by the CCM toolkit. A CCM tool like Panaseer would likely use CAASM as a data source, which can help enrich CCM as broader tool, with wide-ranging uses across all lines of defence in security, and the wider business – security and IT operations, reporting, monitoring, GRC, audit. As a single source of truth that can be trusted by stakeholders throughout the business, Panaseer provides insights for all levels of strategic decision-making. Whether that’s day-to-day security vulnerability prioritization or at the board-level.
The final word
CCM is back in town and here to stay this time. If you want to get ahead of the curve, speak to the original and best by requesting a demo. As CCM sees the Return of the Category, then you could consider Panaseer to be a hybrid of Luke Skywalker and Aragorn.


