Continuous Controls Monitoring gains momentum
Momentum Cyber's Cybersecurity Almanac 2021 highlights current trends that will shape the future of cybersecurity, including security measurement, monitoring, and increased visibility.
They suggest: ‘Organisations require a better understanding of their security stack and performance', and, 'pressure from board members and regulators will drive firms to adopt better measures of real-time security controls.’ Continuous Controls Monitoring (CCM) is the next gen technology that will guide this trend, and Momentum Cyber acknowledged Panaseer as a representative vendor.
The team here at Panaseer has been pioneering the Continuous Controls Monitoring category for several years. It’s a tribute to this hard work that organisations like Momentum Cyber are recognising the necessity of the category we have helped to build, and that it ‘will shape the future of cybersecurity’.
In the wake of Gartner's recognition of the CCM category last year, this endorsement continues to validate those efforts. Momentum Cyber points out that there are three elements driving the growing need for real-time security measurement: scrutiny, visibility and insurance. Let’s look at each of these trends.
Scrutiny
The growing and changing threat landscape has led to a significant increase in security spending and an understandable tendency to buy the latest security tools to address the evolving threats. Enterprises don’t want to be caught out by a lack of tooling. This means there’s a proliferation of tools and a growing number of security silos.
Together, these produce an overwhelming amount of data that is fragmented, often contradictory, and lacks business context (and even the context of all of those other tools). This approach is fundamentally flawed.
The tools know where ‘they are’ but don’t know where ‘they are not’, and cannot provide a reliable view. The tools are simply not designed to communicate together or present a joined-up picture for the security team and they are unable to translate that data into the language of the business.
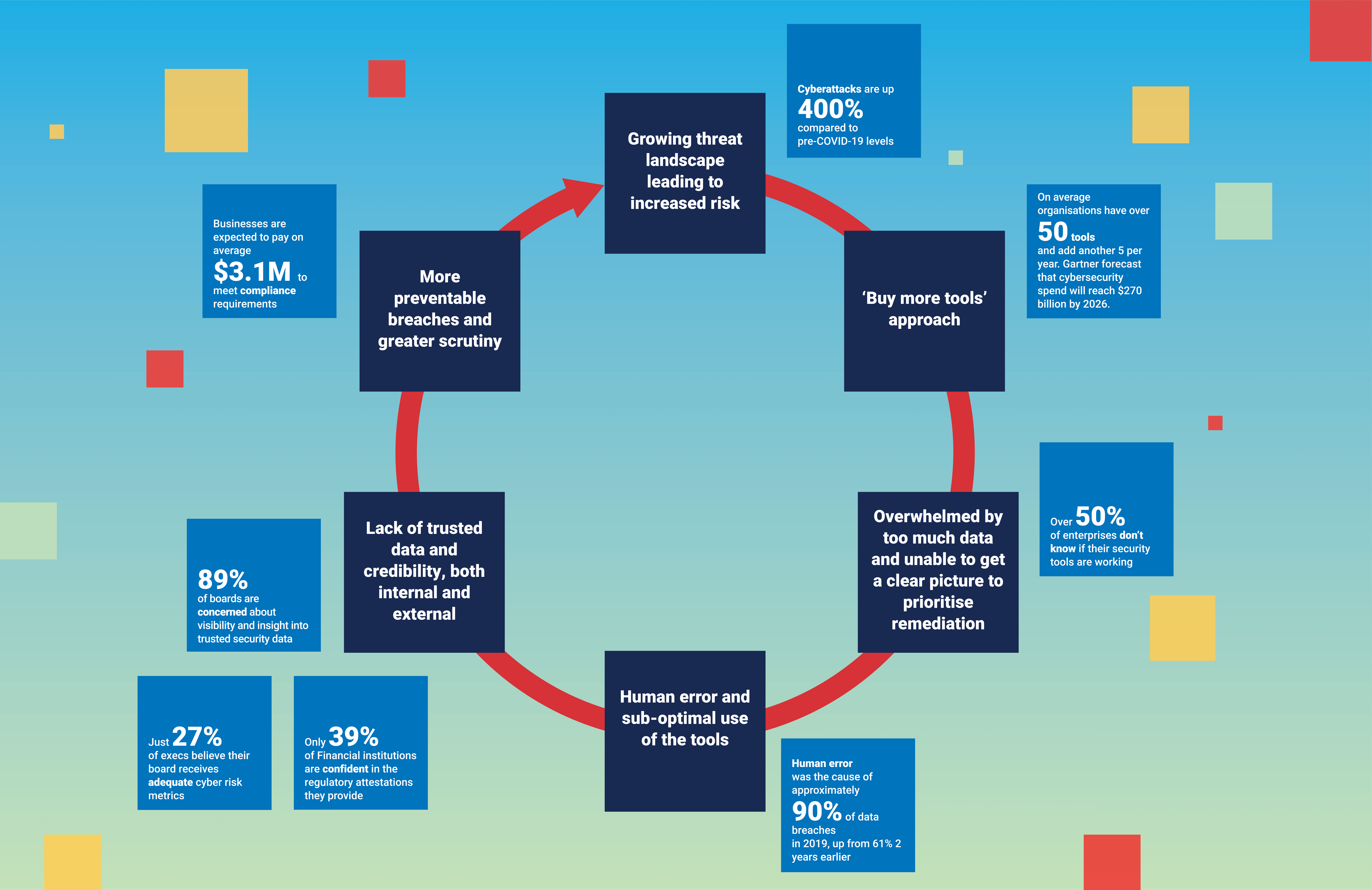
Despite the increased security spending, the number of breaches continues to rise, which then leads to greater levels of scrutiny of the security function. This scrutiny comes from inside the organization (the board, audit, GRC, lines of business) and from external bodies (with increasing regulatory pressure).
It's creating something of a self-fulfilling negative spin:
 Scrutiny is also increasing because the speed of business is accelerating at a time when cybersecurity is now mission-critical to most organizations. There are new business opportunities and markets to navigate as well as the need to adapt to competitive threats, both from traditional competitors as well as 'come from nowhere' disruptive competitors.
Scrutiny is also increasing because the speed of business is accelerating at a time when cybersecurity is now mission-critical to most organizations. There are new business opportunities and markets to navigate as well as the need to adapt to competitive threats, both from traditional competitors as well as 'come from nowhere' disruptive competitors.
Organizations need to adopt new technologies at a faster pace and the business needs the security team to be able to respond at the ‘speed of business’. When only 40% of security leaders can confidently answer the question ‘How secure or at risk are we?’, it's hard for security teams and leaders to build credibility across the business.
On top of that, when security teams try to drive security improvements across functions, they are hampered by the lack of credible and trusted data. Too much time is spent challenging the security data. This lack of clarity erodes trust and accountability, which hurts the organization’s ability to drive competitive change.
Visibility
'It's not what you don't know that kills you, it's what you know for sure that ain't true.' - Mark Twain
The scrutiny challenge is largely a consequence of a lack of trusted data, or in other words, a lack of visibility. This is partly due to the previously mentioned explosion of tools. There are huge data challenges when it comes to measuring security posture because it’s so difficult to get real-time visibility across so many tools that aren't made to work together. You’re overloaded with data and, crucially, you don’t know how tools are performing against an organizational baseline.
This lack of visibility means people are operating in the dark. There’s a lack of trusted security metrics for all assets and therefore a lack of understanding of how those assets relate to business processes and priorities. In fact, 53% of experts admit they are in the dark about how well the technologies they have are meeting expectations and protecting the network. Similarly, only 41% say their organizations are effective in determining and closing gaps in controls coverage. The security team is simply not set up for success. They have more data than ever before, but they are ‘blind’ and ‘overwhelmed’.
More tools actually lead to reduced visibility. The requirement is to resolve the data across all the siloes of tools and to add business context.
Turning on the lights is now a data science problem. CCM gives you the power to do so. It aggregates all the data from across your tools into a single platform, whether that data comes from security, IT, or other business tools. This provides a complete cybersecurity metrics platform for the security team to use and share, giving you complete visibility of the security posture across your entire estate. Beyond aggregation, the platform performs advanced data science via its entity resolution engine. It collects, cleans, unifies, enriches and links data across people, endpoints, servers, accounts, databases, applications, and more.
Entity resolution is the secret ingredient that combines all the fragments of data from all your siloed data sources and understands every asset, the status of all controls relating to those assets and how those assets relate to each other and the business. It provides context so that you can prioritize security metrics according to business impact, business priority, or business owner, allowing focus on the crown jewels. This process can be entirely automated, free from human involvement, and continuously available. For the first time, security teams can present security posture in the language and context of the business. Instead of working from outside, the security team can now facilitate collaboration with the business. Gone is the blame, mistrust and finger-pointing. Credibility from trusted data puts everyone on the same page. Ownership and accountability are clear.
CCM and insurance
The Almanac suggests that CCM technologies may improve the cyber insurance industry, both by encouraging enterprises to accelerate the adoption of better measurement and management of their security tools and posture, as well as by allowing cyber insurers to better understand the risks of enterprises. The Almanac shares some staggering insurance statistics – 74% of businesses do not have cyber liability insurance, so it stands to reason that the cyber insurance market size is expected to increase 186% by 2025.
The cybersecurity insurance industry model is fast becoming outdated. Currently, policies are generalized and non-specific, which can be problematic both for the enterprise and the insurer. With an increasing demand for cyber insurance, particularly in industries such as finance, healthcare, and IT, cyber insurers will need to adopt a different approach.
There’s also a level, or lack, of trust on the part of the insurer. They don't have objective evidence of their insured organization’s defenses. That means there’s a big risk to the insurer, which in turn means higher premiums.
The application of continuous, objective security metrics provided by CCM benefits both parties. CCM helps optimize your security posture, therefore insurers may give discounts or preferential rates to organizations deploying CCM. Then perhaps later, CCM will be used in the same way as ‘black box’ car insurance – setting premiums based on the quality of the organisation’s security posture. And eventually, insurers may require CCM for organizations to get cyber insurance.
That means a cyber insurance industry with less risk for insurers and better premiums for policyholders. CCM is fundamentally about reducing risk and preventable breaches, which benefits the insured and the insurer. Essentially, the insurance-driven trend around CCM comes back to scrutiny and visibility. Insurers will want more visibility on the risk and security posture of enterprises in order to provide an appropriate policy. And the enterprises will have to deal with this new level of scrutiny coming from insurers.
'Organisations require a better understanding of their security stack and performance’
The increased demand for CCM is based on the fact that ‘organizations require a better understanding of their security stack and performance’. The average enterprise has a plethora of security tools deployed, but this doesn’t translate to improved security. It’s a web of disjointed technologies that makes it difficult to aggregate risk data for reporting. CCM is required to optimize your ROI on security tooling and controls. With that comes a comprehensive list of assets across the organization, real-time visibility of security posture, and automated reporting and dashboards across the enterprise.
So, do you need to buy more tools, or can you get more juice out of the tools you currently have?
CCM tech can be used to escape this negative spiral. Instead of buying more tools and continuing further and further ‘into the darkness’, wouldn’t it be better to ‘turn the lights on’ and to find a way to aggregate data in a way that you could trust it and get a complete view?
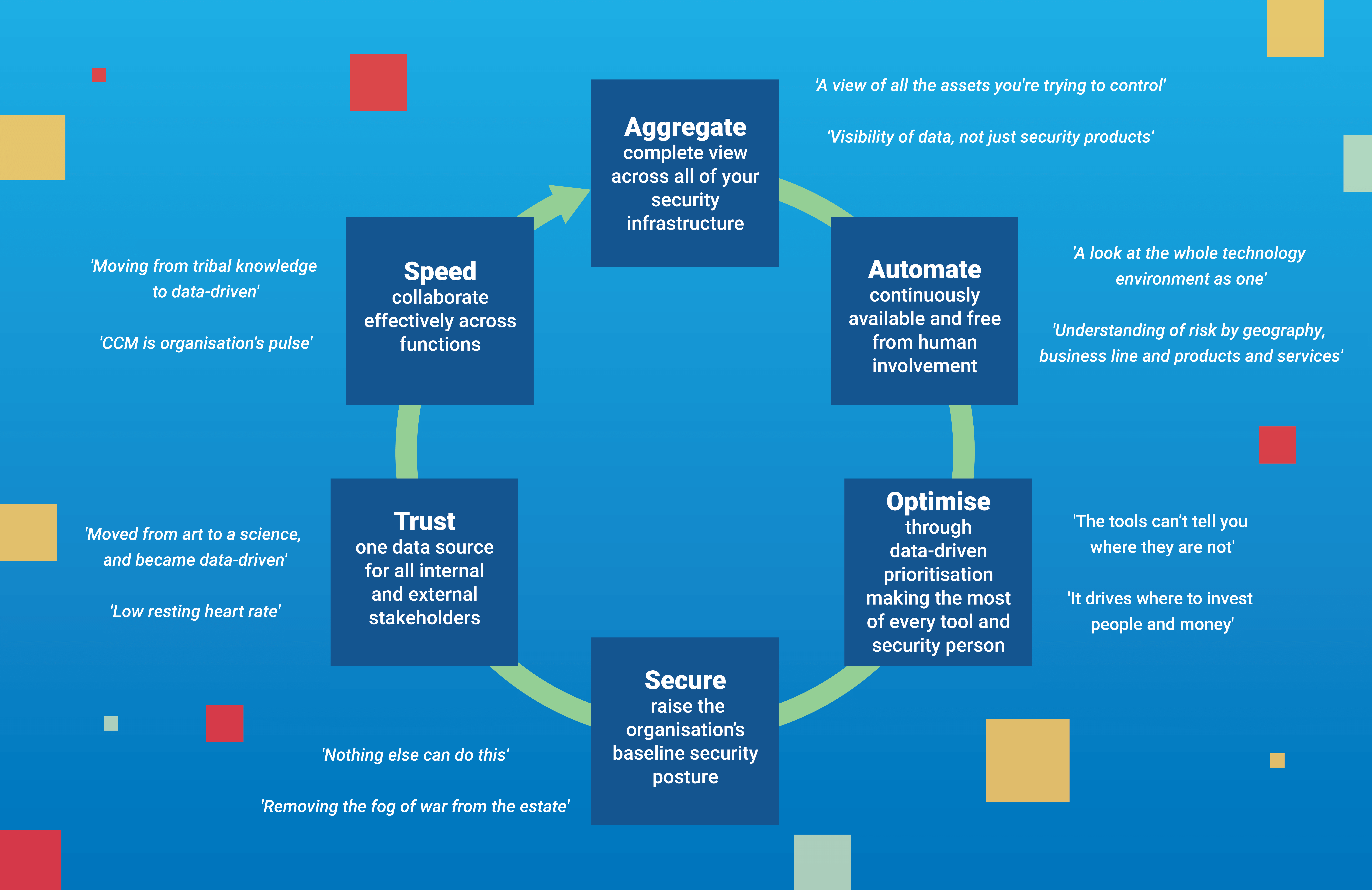
CCM helps you create a self-fulfilling positive spin (with some quotes from CCM users):
Automate the process. Optimize your current arsenal. Raise the organization’s baseline security posture. There’s more cross-functional trust. It’s easier to work at a higher speed across functions.
We are very proud of the role Panaseer has played in enabling the CCM market to come of age. This recognition from Momentum Cyber is further validation that now is the time for businesses to invest in CCM technology.