
Cybersecurity measurement trends and predictions for 2022
We’ve experienced major changes in cybersecurity over the past 18 months. The pandemic, an increase in financially damaging ransomware breaches, and third-party compromises have security teams under more pressure than ever.
For security measurement, this means an increase in assurance to oversight bodies, adapting measurement techniques to accommodate changes in working practices, and an increased need for accurate information to hold internal stakeholders accountable.
Before we dive into my cybersecurity measurement trends and predictions, let’s look at the current state of play. Here’s what our 2022 Security Leaders Peer Report reveals about the impact of the pandemic on cybersecurity:
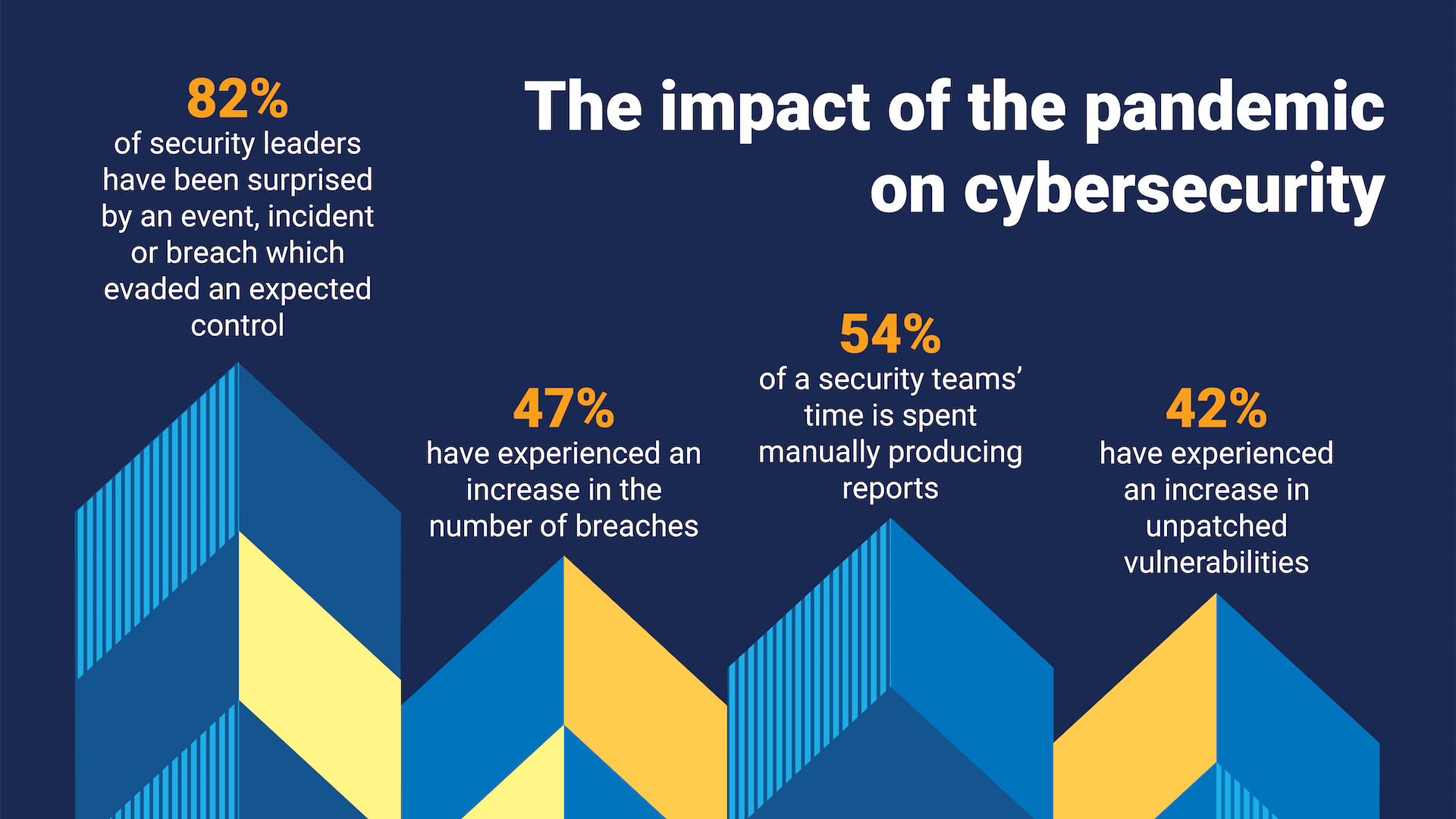
The first stat is telling – in conversations with CISOs, the number one pain that keeps them up at night is suffering a breach through control failure. And it’s no surprise, as highly conscientious people, CISOs want to be diligent and prepared. If they’ve invested in a control, they don’t want to be liable for a breach due to that control failing.
We’ve seen more events, incidents, and breaches. More unpatched vulnerabilities. More time spent remediating, rolling out tools, and reporting. Security teams are working harder than ever. In this article, I’ll look at the following themes in cybersecurity measurement:
- Ongoing security trends
- Ransomware
- Cyber insurance
- Oversight and stakeholders
Ongoing security trends
When I started the company in 2014, there were critical challenges driving the need for automated cybersecurity measurement. Those are still relevant today and will remain so in the future:
More breaches. A few years ago, a major breach was front page news. Now it barely gets a mention. The number of breaches continues to rise, and the cost of a breach continues to rise.
More scrutiny. As the frequency and impact of breaches have increased, so has the level of scrutiny on security teams. Externally, this includes regulators, auditors, customers, insurers, enquirers, and partners. Internally, this means risk and compliance, the board, and internal audit. And it's not just the number of people demanding information, the breadth and depth of data required has grown. It's no longer enough to state an intent to do good security, it's often necessary to provide empirical evidence.
More accountable stakeholders. Every individual, department, and function has an impact on cybersecurity posture. To reduce risk, security teams must now deliver increasingly high-quality metrics to a wider variety of stakeholders that need to be held accountable using language and formats they can understand.
More tooling. To help deal with the evolving threat landscape, organizations continually invest in new tools. Our research found the average enterprise now has 76 security tools – an increase of 19% over the last two years.
More data. This influx of tooling means data silos. Each tool requires expertise and management and adds to the complexity of understanding all assets and controls in the enterprise. Our research indicates that this problem is contributing to enterprise security teams spending (some would say wasting) half their time on manual reporting.
Scarcity of security pros. The need for security professionals is growing faster than we can train them. The security skills shortage gap is a real problem, and while there are things we can do to overcome it, it will continue for the foreseeable future.
These are fundamental challenges in cybersecurity, they have deteriorated over the last seven years, and I predict they will continue to deteriorate.
Ransomware
Ransomware is the risk du jour in cybersecurity, and it will only grow in 2022. There has been a considerable increase in ransomware attacks in 2021, according to a Trend Micro report, with the banking industry seeing a 1,318% year-on-year increase in attacks.
The Verizon 2021 DBIR also noted an increased frequency of ransomware attacks and expects that to continue. Often the negative impact of a cyber breach can be ambiguous and hard to quantify. But in the case of ransomware, money goes out the door and business operations are shut down. These are easily measurable and communicable, and I believe that’s why they’ve had such a dramatic effect on the industry.
Ransomware is a board-level risk. Leaders outside of security are rightly concerned about the potential for major disruption and damage. Indeed, there are also physical consequences – we saw the impact of the Colonial Pipeline attack. We have seen cyberattacks on healthcare organizations lead to patient deaths. Events like this will unfortunately get worse before they get better.
Cybersecurity measurement is critical in combating ransomware. As the old adage goes, if we can’t measure it, we can’t manage it. Attackers use well-understood techniques to gain entry, establish a foothold, move laterally, and lock down a victim’s computer systems and services. These attacks can be thwarted by a fully deployed, effective set of security controls. But the only way to ensure defenses are always fully operational is through continuous monitoring of assets and controls to provide constant assurance.
Not only that, but ransomware also has a critical impact on…
Cyber insurance
Cyber insurance used to be straightforward – you would answer a short questionnaire, get a decent premium for multi-million dollars of cover, and in the event of a breach, the insurer would pay out. As brokers and underwriters competed for market share in this new and burgeoning market, customers were the winners.
But now, thanks in part to the proliferation of ransomware-driven claims during the pandemic, cyber insurers have been forced to pay out on underpriced policies, pushing their portfolios towards being loss-making.
The result is that the market has hardened, insurers have withdrawn and it’s much tougher for customers to get insurance at all, let alone good value on a policy. I predict that an inability to purchase cyber insurance will become another driver for improved cybersecurity measurement. As insurers increasingly choose only the best-looking customers to insure, organizations will need to improve the way they communicate their security posture.
Looking beyond 2022, I expect a consistent form of measurement and reporting to emerge for insurance, where clients can compare like-for-like policies across insurers, and insurers can compare customers’ security risk, again on a like-for-like basis. This will involve standardization of metrics and measurements, and a willingness to share more data to collaborate towards lower risk and therefore lower premiums.
The future of the cyber market looks like car insurance’s telematics. Our research supports this. We asked 1,200 security leaders from large organizations across various industries the following questions:
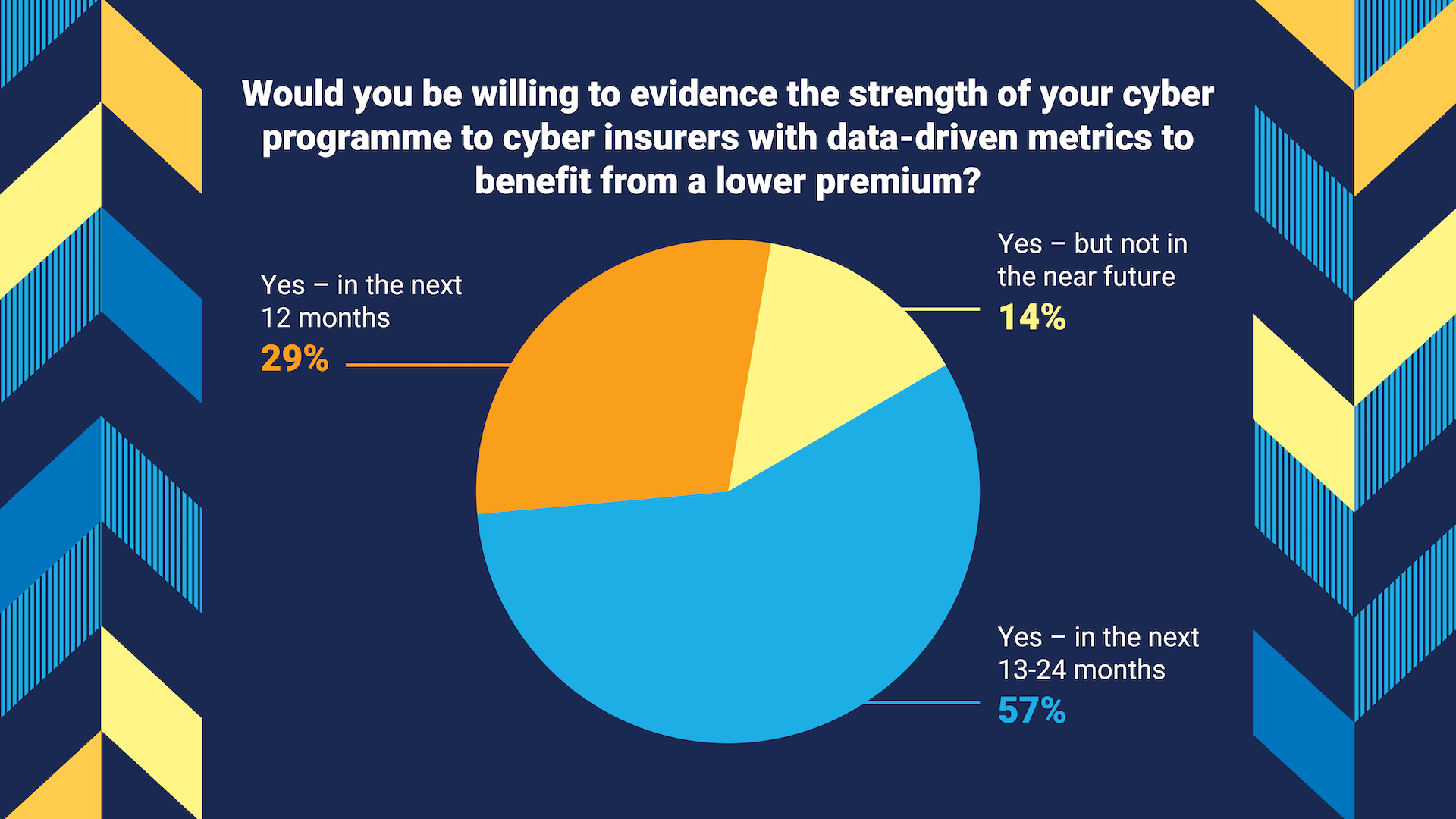
This shows that organizations would be on board with this idea. We just need to get the insurers to sign off. It will bring its own challenges, but it seems like a clear win-win.
Oversight and accountable stakeholders
We can put security stakeholders into two main categories – oversight and accountability.
- Oversight. These are the stakeholders that our security teams need to demonstrate security posture to, with trustworthy and understandable security metrics and measurements. These include auditors, the board, regulators, customers, and insurers.
- Accountable. These are the stakeholders being held accountable by the security team, including IT, business lines, operational functions, and third-parties.
Fundamentally, they all need to see metrics about the status of security. We’ve already explored cyber insurers, so let’s have a look at a few more that I predict may come to the fore in 2022.
Third-party assurance – Like cyber insurance, third-party assurance was once the realm of paper-based questionnaires and tick-box exercises. But as cyber risk rises, so do the inherent risks taken on when third-party organizations hold data that doesn’t belong to them.
According to a report by BlueVoyant, 93% of companies have suffered a cybersecurity breach because of weaknesses in their supply chain/third-party vendors, and 97% of companies have been negatively impacted by a cybersecurity breach that occurred in their supply chain. We’ve seen the increasing burden put on security teams in both managing third parties and being managed as a third party – this doesn’t scale and new ways of working will emerge.
I predict that organizations will require third parties to prove their security status using metrics and measurements aligned to standards such as NIST or CIS. Similar to the car insurance telematics idea mentioned in insurance – if a third party can give data-driven evidence of good security posture, then they can pass stricter third-party assurance checks.
Regulatory drivers – Regulators will continue to want more up-to-date, granular security metrics, with high levels of data quality, more frequently. As regulations become stricter, which they inevitably will, organizations will be required to provide reliable metrics and measures rather than survey-based attestations.
Accountable owners – Security teams are only able to directly impact a small percentage of an organization’s security posture. Most of the exposure sits with teams, individuals, and infrastructure outside of their direct remit. The challenge is to raise awareness, influence those individuals and teams more strongly, and hold them accountable. Security teams need to provide tailored metrics alongside credible plans of improvement to influence owners of risky applications across the business.
But security tools aren't built with this requirement in mind, so producing business and application-specific metrics and KPIs is challenging. I expect to see a continual increase in the security team's workload as the need to prepare these business-relevant measurements grows, and accountable stakeholders become more interested in the detail behind the numbers. As mentioned in the graphic above, our research found security teams are already spending over half their time on manual reporting, and that's a considerable rise since 2019, when it was 40%.
The final word
To protect the services we all rely on, we must urgently improve data quality in security measurement which is exactly what our platform is capable of doing through Continuous Controls Monitoring (CCM). Security teams and their stakeholders need access to timely, complete, accurate information, produced automatically and continually, with consistency and integrity.
This will not be optional in the future, in the same way, it’s not optional for a company to file a correct income statement or balance sheet. Whether the need is driven by cyber threats, supervisory bodie,s or our business partners, we’ll need to use automation to improve the range and quality of our security measurements and protect our security teams from being overwhelmed.
Request a demo of our platform today to learn more about how Panaseer can resolve your tracking and reporting challenges through automated CCM.


