
How to mitigate ransomware with Continuous Controls Monitoring
In this blog, we will show how Continuous Controls Monitoring (CCM) can be used to help mitigate the growing threat of ransomware and how to measure specific ransomware controls.
Ransomware is a big topic in security right now. We are not trying to push FUD when we say that ransomware is on the rise and is an increasing threat to enterprises. There have been a number of high-profile attacks in the news in recent months that help put ransomware top of mind for increasingly cyber-aware boards. But it isn’t just scaremongering – the rate of ransomware attacks has increased.
As per Verizon’s 2021 DBIR: ‘The major change this year with regard to action types was Ransomware coming out like a champ and grabbing third place in breaches (appearing in 10% of them, more than doubling its frequency from last year).’ (Another note, up from 2% in 2016).
Fundamentally, there isn't anything you can do that will stop ransomware attacks from happening. But there are absolutely steps to take to reduce the risk of them being successful.
Security controls to mitigate ransomware
Ransomware is a huge problem because there are so many ways that it can enter the organization and spread within. You need to deploy a really broad set of security controls to mitigate as many attack techniques as possible. If a ransomware attack is successful, it means that one or more of those controls have failed.
Failed controls bring us to the reason that the new CCM category exists: 'Many incidents are not due to a lack of conception of controls but due to failures of expected controls’. This is a quote from Phil Venables (now CISO at Google Cloud) that has stuck with us since we first saw it on Twitter about two years ago. It hits the nail on the head. Every enterprise will have controls in place to stop ransomware. But barely a handful of those will be able to say, with confidence, if their controls are working effectively, or how well protected they are against a potential ransomware attack.
And that’s a question they may well be asked by their board, if they haven’t already.
This is the case for a number of our customers. They’ve got their CCM platform, so they know all they can about their security posture. But then they get the ransomware question from the board. With CCM they have all the information they need to answer the ransomware question, it's just a case of presenting it appropriately, hence the ransomware-focused dashboard initiative.
As part of that initiative, we built out-of-the-box capability leveraging insight from our customers, framework organizations, and thought leaders like Andrew Jaquith, author of Security Metrics: Replacing Fear, Uncertainty, and Doubt, who is an expert on both security metrics and ransomware. You can see what he had to say in our recent Metric of the Month article on ransomware protection metrics. Andrew’s method is to measure with ransomware in mind, aligning to a three-step attack path. This is a particularly effective and relatively condensed story that a board audience can digest without a security background.
Mapping key ransomware controls to attack paths
Putting all that together, we mapped key ransomware controls to the MITRE ATT&CK framework and built a dashboard that measures some of the most effective security controls at three stages – infiltrate, propagate, and exploit.
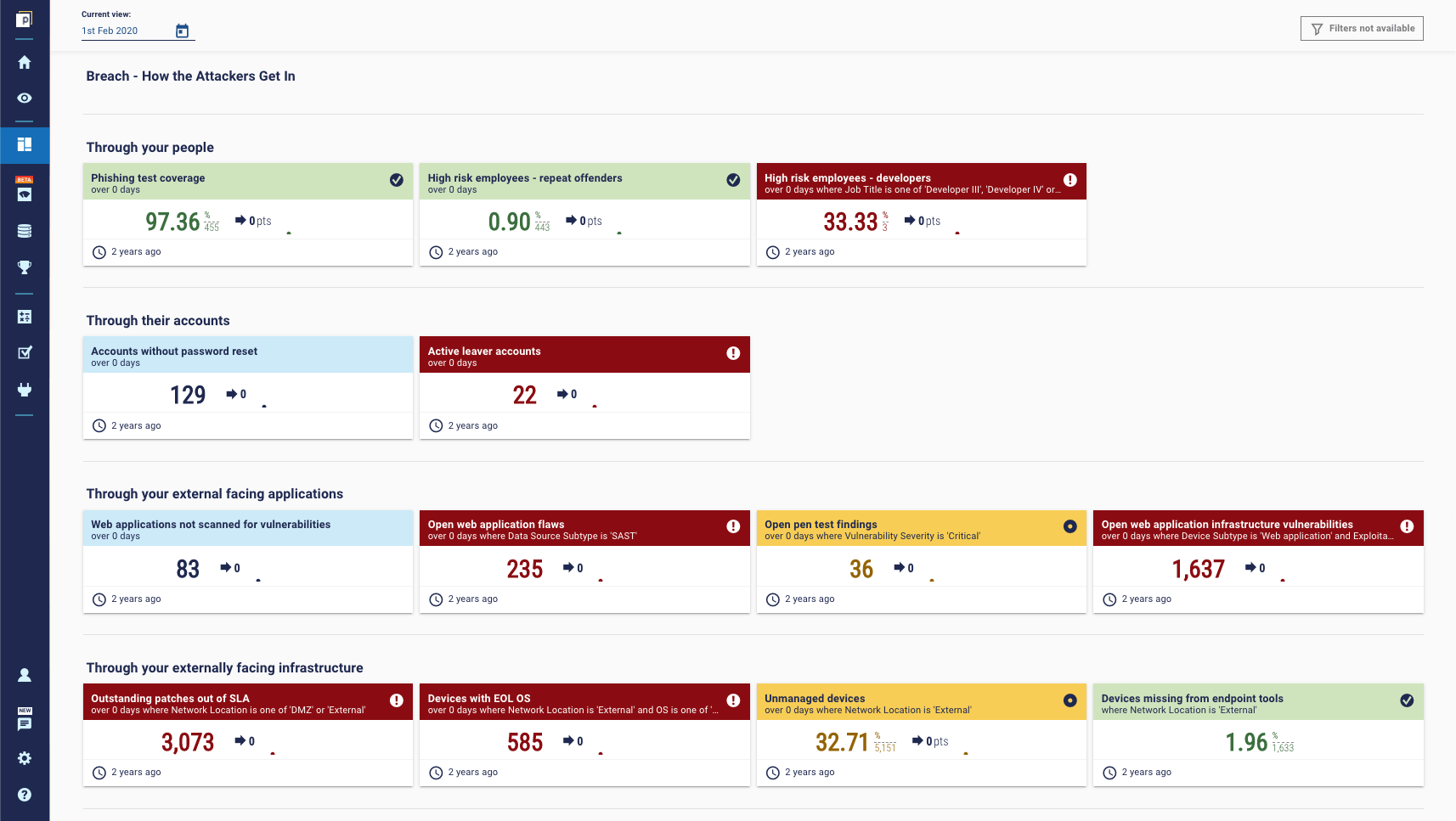
Infiltrate - How to mitigate ransomware at the perimeter of the organization.
There are various ways that ransomware can get on your network:
- Through your people. So, you’ll need to look at stuff like phishing, especially among particularly high-risk employees like developers or admins.
- Through their identities. Keep on top of password resets and active leavers.
- Through external applications. Scan those web apps, test that penetration.
- Through externally facing infrastructure. Check for patches, end-of-life software, and unmanaged devices. All that good stuff.
Here's how it looks on a dashboard:
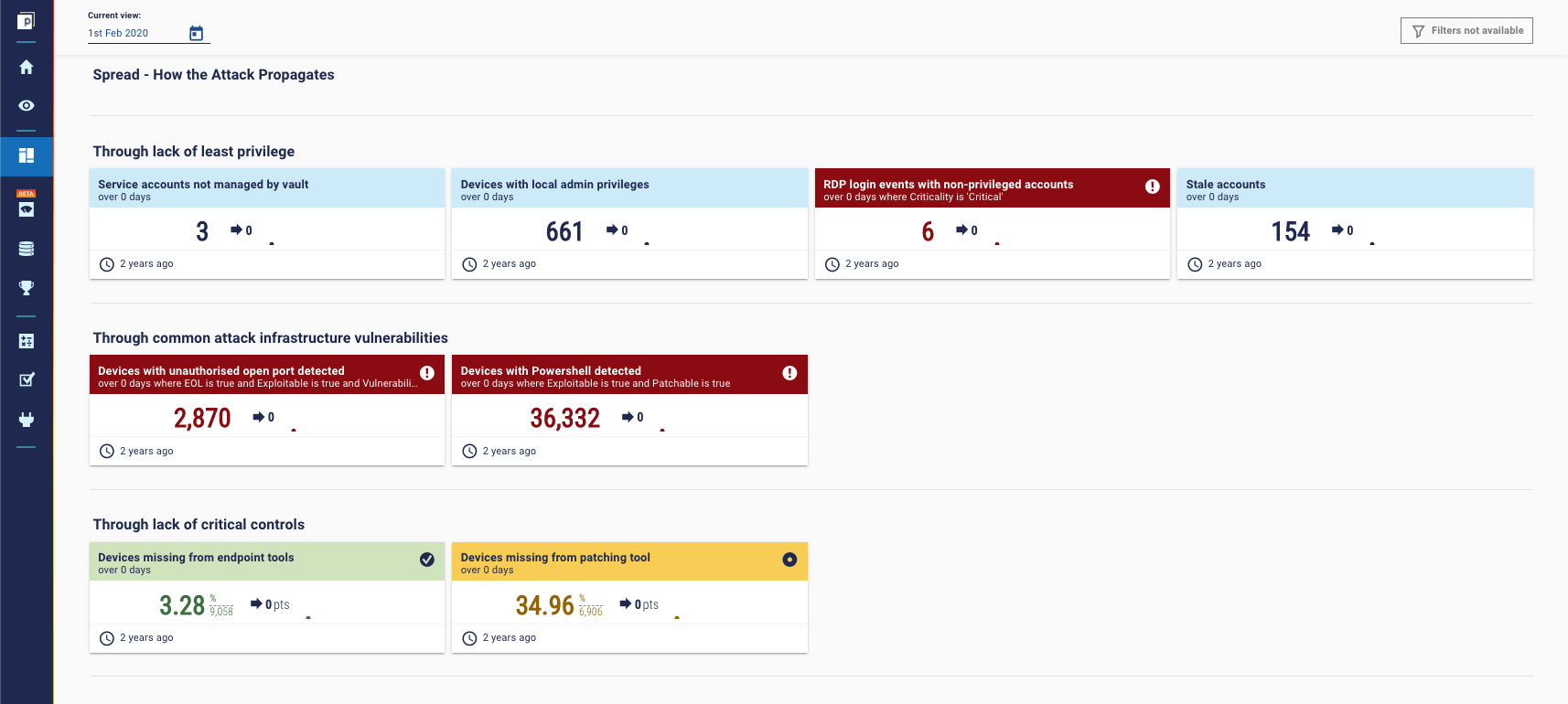
Propagate - How to mitigate ransomware inside the organization.
These controls are in place to help reduce the chance of an attacker gaining ‘domain dominance’ if they get inside. The attack can spread in a number of ways:
- Through lack of least privilege. Here we want to keep on top PAM, of course.
- Through common attack infrastructure vulnerabilities. Monitor for common exploit kit vulnerabilities that are active out in the world.
- Through lack of critical controls. Key controls like endpoint security and patching tools should have the best coverage possible.
Here’s the dashboard view:
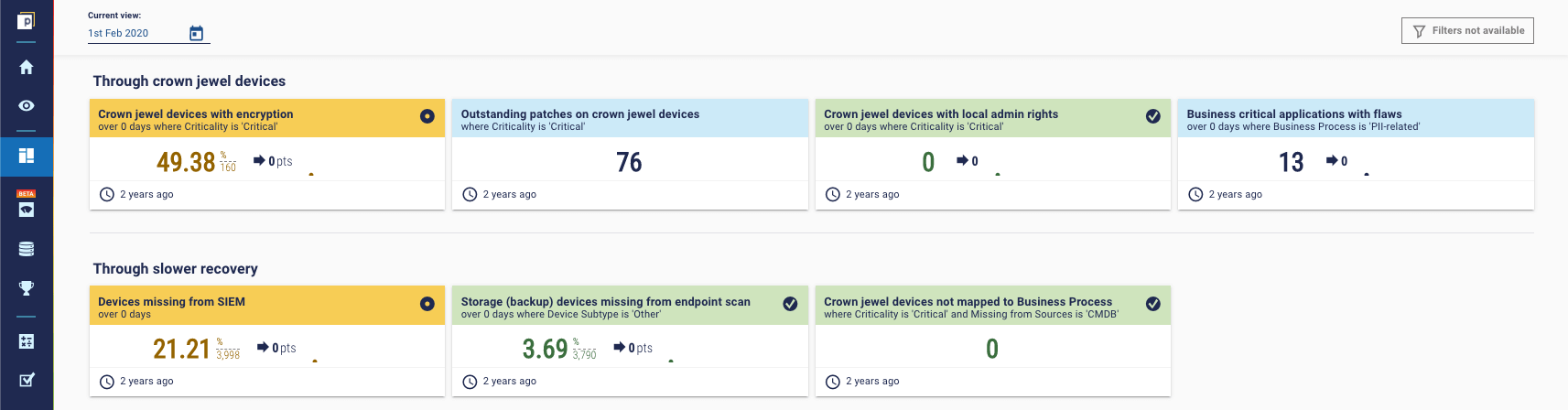
Exploit - How to help mitigate the potential damage from ransomware.
If the ransomware attack is successful, you need to be able to respond and recover. That means protecting the most business-critical assets in your enterprise. Beyond the obvious ransom, a ransomware attack can exploit you in several ways:
- Through your crown jewels. Ensure your most important devices have encryption, are up to date with patches, have appropriate admin controls. These things can all help.
- Through slower recovery. To speed up recovery, you want to have all your devices covered by your SIEM, ensure your backups have endpoint protection, and that, fundamentally, you know which devices are your crown jewels.
And here’s the dashboard:
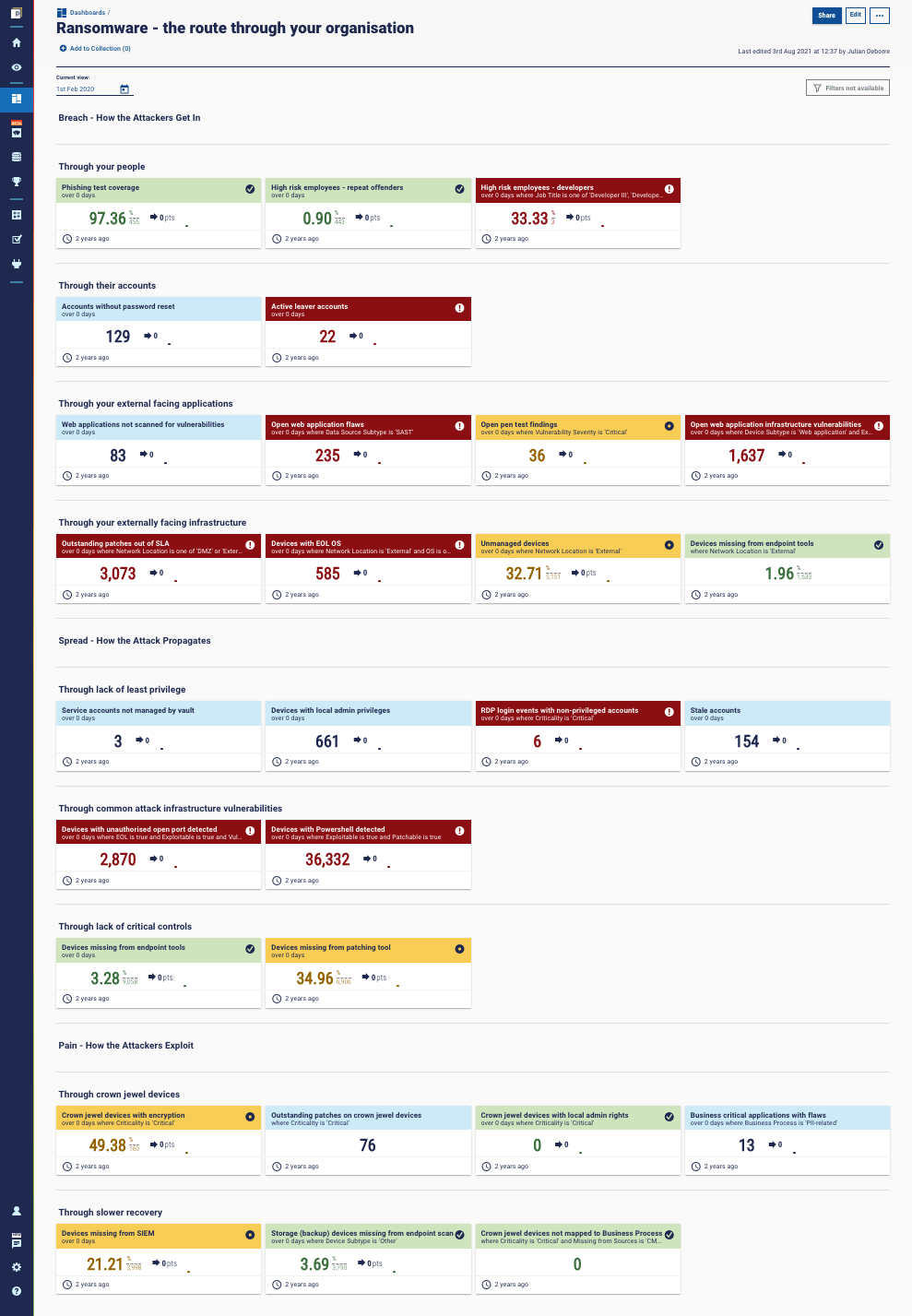
Ransomware mitigation is now a core platform capability
So, we put it all together as a core platform capability for our customers. When we initially brought this new dashboard to our customers for feedback, we saw positive reactions.
We heard that ransomware was a common topic in communication between the security team and the board and that boards are seeking to understand the threat to their specific organization.
Our customers are sharing the dashboard with the board to easily talk in-depth about the current status and the mitigations needed to improve, with a straightforward RAG alignment to risk appetite.
Hopefully, this blog has provided some guidance on how to mitigate ransomware by measuring the appropriate controls. Control failures are one of the leading cyber risks to enterprises, and it is essential to overcome this challenge not just to mitigate ransomware, but to improve security in general.
If you’re looking to see more of our ransomware-focused dashboard, get in touch or book a demo.


