
How to accelerate remediation of the MOVEit zero-day vulnerabilities using Panaseer
Zero-day vulnerabilities like CVE-2023-34362 and CVE-2023-35036 require an urgent response. Find out how the Panaseer platform can help you remediate critical problems quickly and efficiently.
Security teams have been dealing with another zero-day in recent weeks following the discovery of two SQL injection vulnerabilities in Progress Software's MOVEit Transfer tool.
A series of breaches using the initial vulnerability have been attributed to ransomware group Clop, with victims including the US State of Illinois, the Minnesota Department of Education (MDE), the BBC, British Airways and UK healthcare retailer Boots. Many of these organizations were breached in a supply chain attack through payroll provider Zellis.
Based on Clop’s previous activity, the US Cybersecurity and Information Security Agency has warned that it expects to see “widespread exploitation of unpatched software services in both private and public networks."
Panaseer customers have been using our Continuous Controls Monitoring (CCM) platform to measure their potential exposure to the MOVEit vulnerability, known as CVE-2023-34362 and CVE-2023-35036. This article explains how we can help make remediation more efficient, along with a step-by-step guide of how it works.
Using Continuous Controls Monitoring to remediate the MOVEit vulnerability
When a new zero-day is discovered, security teams need to respond quickly to understand their potential exposure and remediate any issues. The Panaseer platform makes this process more efficient using Continuous Controls Monitoring (CCM), giving a near real-time view of your exposure to vulnerabilities enriched with business context so you know what to fix first. The platform also provides several other benefits that improve how security teams remediate critical vulnerabilities.
1. Improved prioritization and accountability
While CVE-2023-34362 and CVE-2023-35036 only impact the MOVEit Transfer software, critical vulnerabilities are often more widespread across your environment. Prioritization is key so your security team can focus on fixing the instances that pose the biggest risk to your organization. The Panaseer platform solves this problem by applying business context that’s unique to your organization. It means you can see where vulnerabilities appear on internet-facing systems that could be directly exploited, as well as the affected business unit, geographic location, the specific business process it relates to or if it’s among the organization’s crown jewels. You can then prioritize remediation and quickly identify the accountable teams. This functionality, which we refer to as Evidenced Remediation, enables you to measure remediation against internal or external standards and ensure systems are patched to agreed deadlines.
2. Single source of truth
When you have more than one vulnerability scanner monitoring your IT estate, which one do you trust when they give you conflicting information? And how do you begin to query and cross-reference the data? The Panaseer platform automates this through our entity resolution process, bringing together data from across your vulnerability scanners and correlating it with data from other security and business tools. It enables you to understand every asset, the status of all controls, and how those assets relate to each other and the business. This unified view is fundamental for accurate analysis of your security posture and exposure to vulnerabilities — without it, it would be challenging to even determine how many endpoints you have.
3. Efficient remediation
Remediation efforts are commonly managed using a ticketing system, however these often fail to accurately track how long it takes to fix a problem and are open to human error. Using our Remediation Objectives, you can identify all instances of a specific vulnerability, track remediation over time and measure the burndown rate to ensure issues are fixed within agreed SLAs. This makes remediation more efficient and proves to stakeholders that your security efforts are proactively reducing risk to the business.
How to measure your exposure to the MOVEit vulnerability using Panaseer
Using Panaseer, you can quickly create a dashboard that shows your exposure to CVE-2023-34362 and CVE-2023-35036. This is similar to the process our customers used when remediating Log4Shell and can be replicated for any vulnerability, including zero-days.
This process includes suggestions on key business attributes to breakdown your analysis to allow additional prioritization for remediation. This can be initiated within Panaseer through ITSM integration and tracked through our Remediation Objective functionality.
Step one
After doing a vulnerability scan of your environment, you can create a new dashboard in Panaseer to highlight your risk exposure using the "New Dashboard" button on the Dashboards menu. 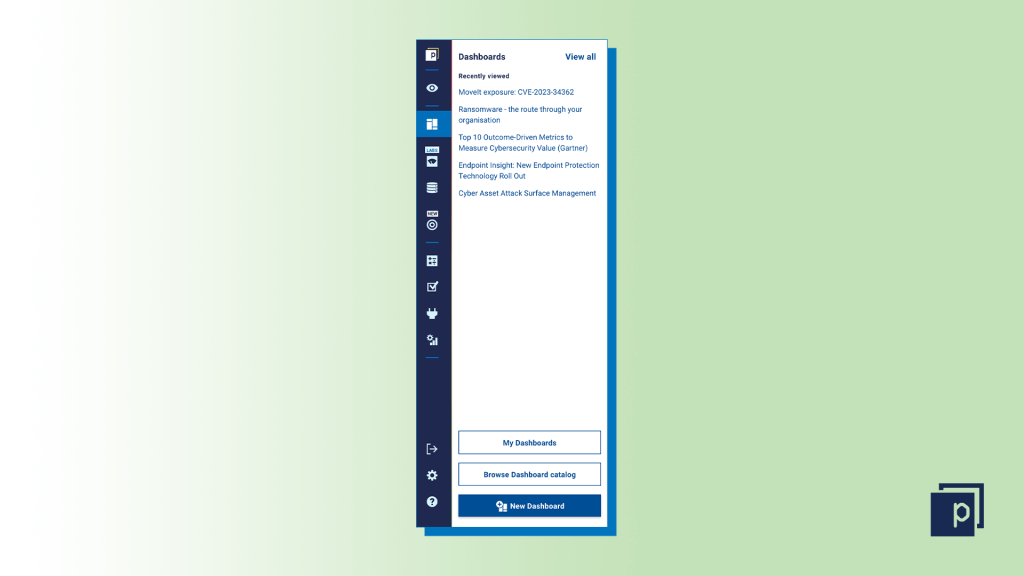 Step two
Step two
Search for the metric "Vulnerability detections by vulnerabilities" in the metric search bar, and drag and drop it into the dashboard ‘Section’ on the right-hand side of the screen. 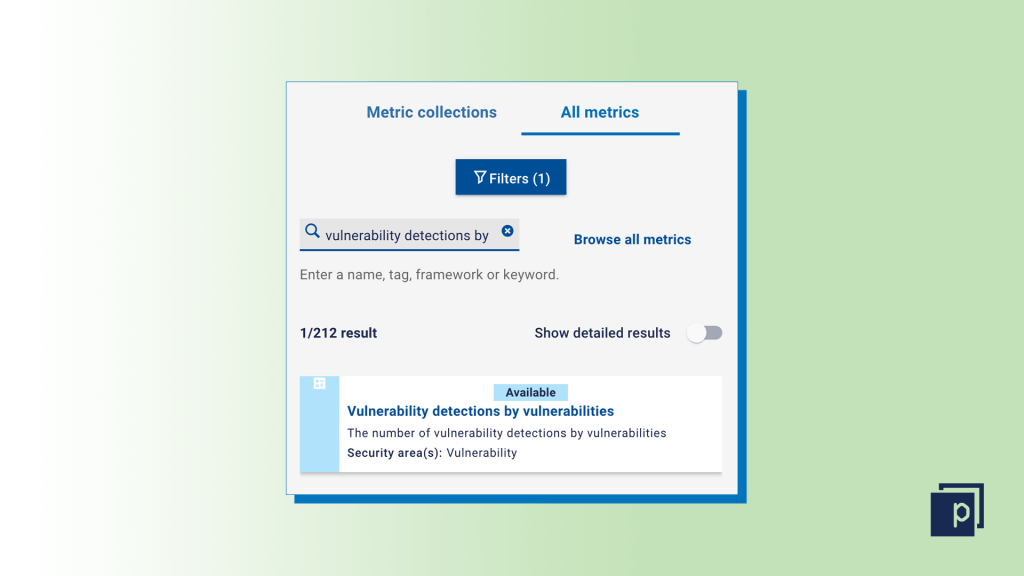 Step three
Step three
Click on the down arrow on the right-hand side of the metric title, and choose the "Filters" button to apply the required filter for either "CVE ID" CVE-2023-34362 or CVE-2023-35036. 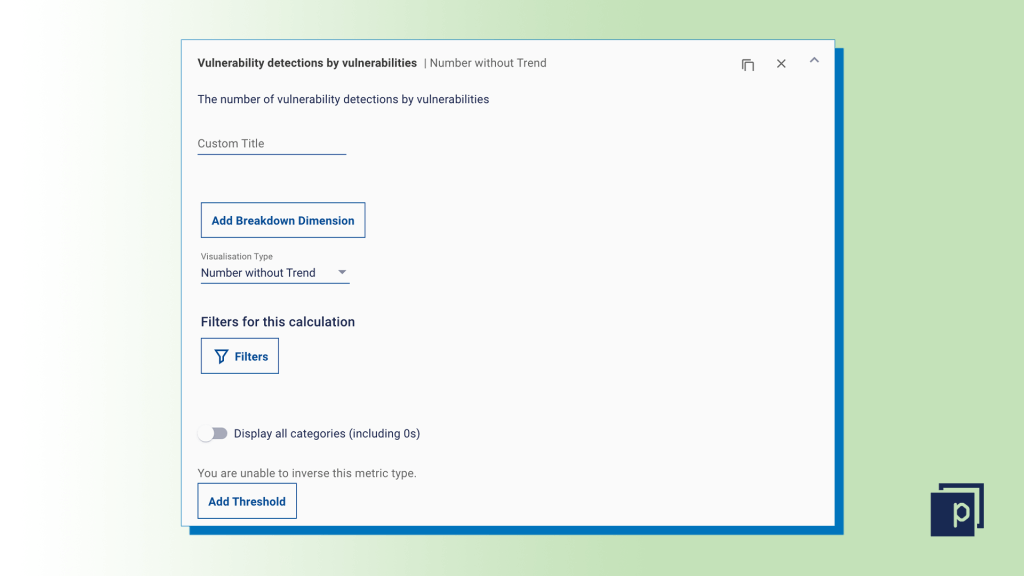 Step four
Step four
Apply the CVE ID or associated vulnerability ID in the Search field and check the boxes. If your searched value doesn’t appear, the vulnerability hasn’t been detected by your vulnerability scan or the scan hasn’t yet taken place to find these vulnerabilities. 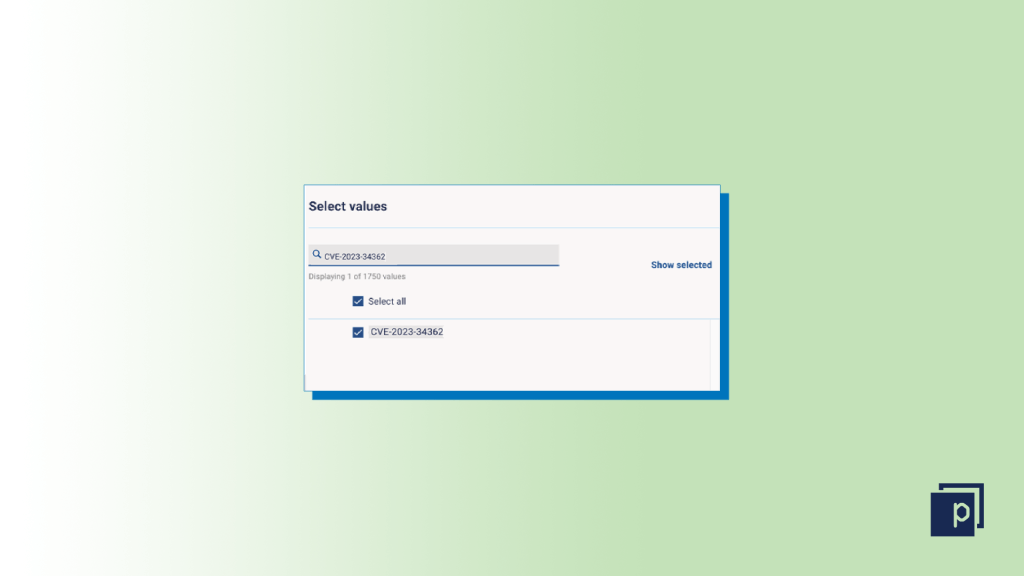 Step five
Step five
The next stage is to customize the reporting. You can choose the visualization type (for example, a time series chart will help you monitor exposure over time), rename the metric, apply thresholds or add in extra business-aligned filters or breakdown dimensions. Suggested filters or breakdowns which can help improve prioritization and accountability include:
- Network location – find detections on externally facing devices.
- Business unit.
- Department.
- Criticality (e.g. crown jewel devices).
- Region.
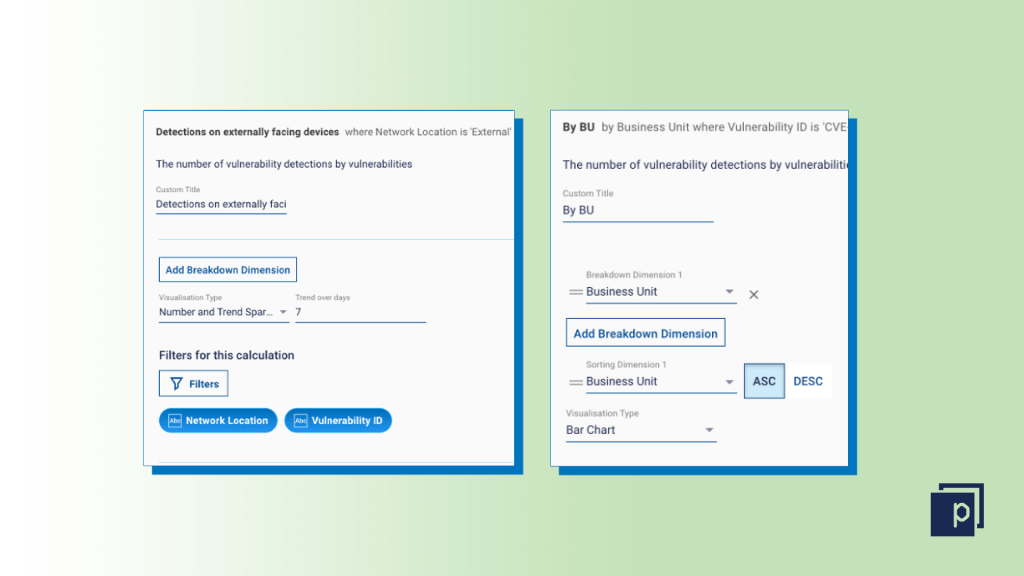 Step six
Step six
Give your dashboard a title and hit "Save and preview". You can also publish your dashboard for others to view. 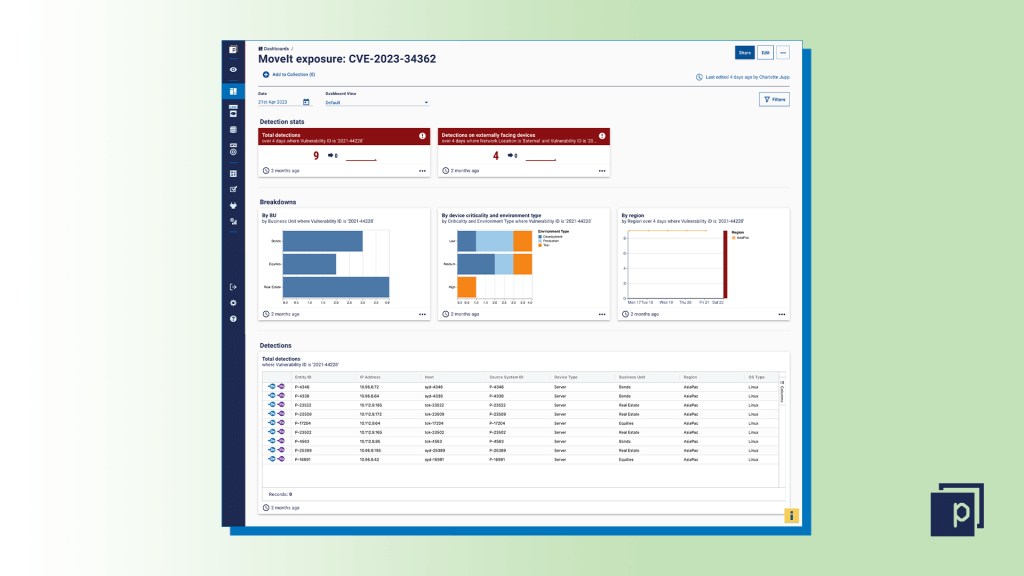 Step seven
Step seven
Finally, make sure you use your dashboard and Expanded Cards to initiate your remediation efforts and track progress. Click into any metric and use the "Action" tab to export the data to CSV, raise a ticket directly into your ITSM and remediation workflows, and create a Remediation Objective to track the progress of that remediation. 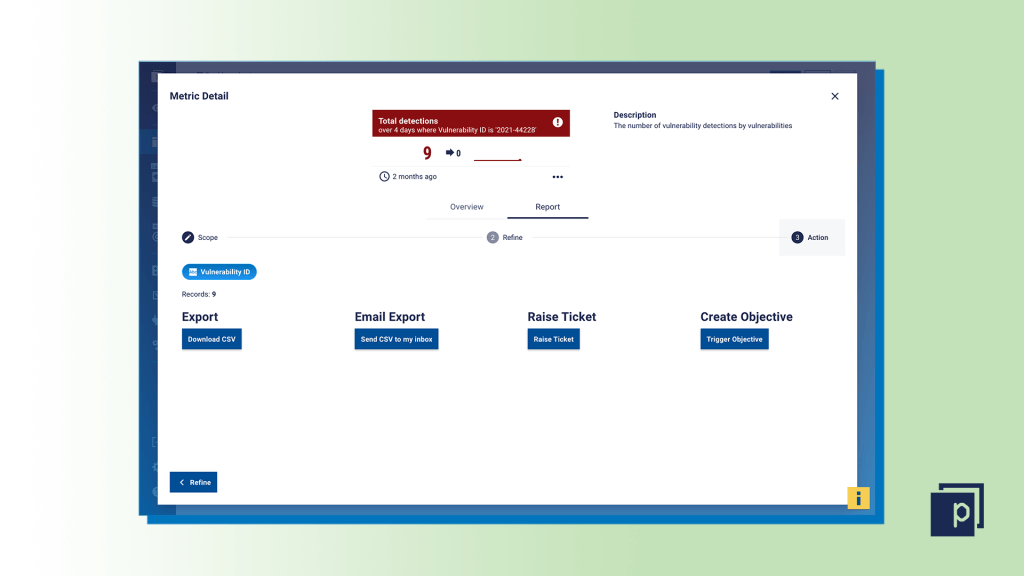 Our customers are already using the Panaseer platform to measure their exposure to the MOVEit vulnerabilities using this process, giving them confidence they’re actively reducing risk to their organizations. For further updates and details of patches go to Progress Software’s security center.
Our customers are already using the Panaseer platform to measure their exposure to the MOVEit vulnerabilities using this process, giving them confidence they’re actively reducing risk to their organizations. For further updates and details of patches go to Progress Software’s security center.
Request a demo to find out how the Panaseer platform can improve how you measure and remediate your exposure to zero-day vulnerabilities.


