
Nine questions to ask your CAASM provider
As the CAASM (Cyber Asset Attack Surface Management) market is becoming more well-known, more organisations are looking to this new technology to automate their asset inventories. The cyber asset management market had a “golden year” in 2021, as funding grew by 138% to $29.5 billion. It has great appeal for investors, not just because of potential profitability, but because it is essential to quality cybersecurity. But, being a new technology, not all potential customers will know what makes a good CAASM platform. So, we’ve come up with a list of nine questions to ask, based on interactions with customers and prospects, so you can be confident you’re working with the best provider.
1. Can your CAASM tool identify all assets on the network?
To be honest, you shouldn’t have to ask this. It is the point of CAASM. For a stronger response, you’d want to see the CAASM tool create multiple inventories, across various asset types. For example, the most important asset type for CAASM is devices. But other important asset types are people, accounts, applications, and more. With these further inventories, they can be layered to provide great visibility across your attack surface. That way you can identify a device, the accounts that may have access to it, the people using those accounts, the applications on it, and any vulnerabilities it might have. That’s extremely valuable information to have in one place when it comes to protecting that device. This is an excerpt from our CAASM dashboard that shows a device overview, including metrics on total devices, externally facing devices, and devices missing from the CMDB. 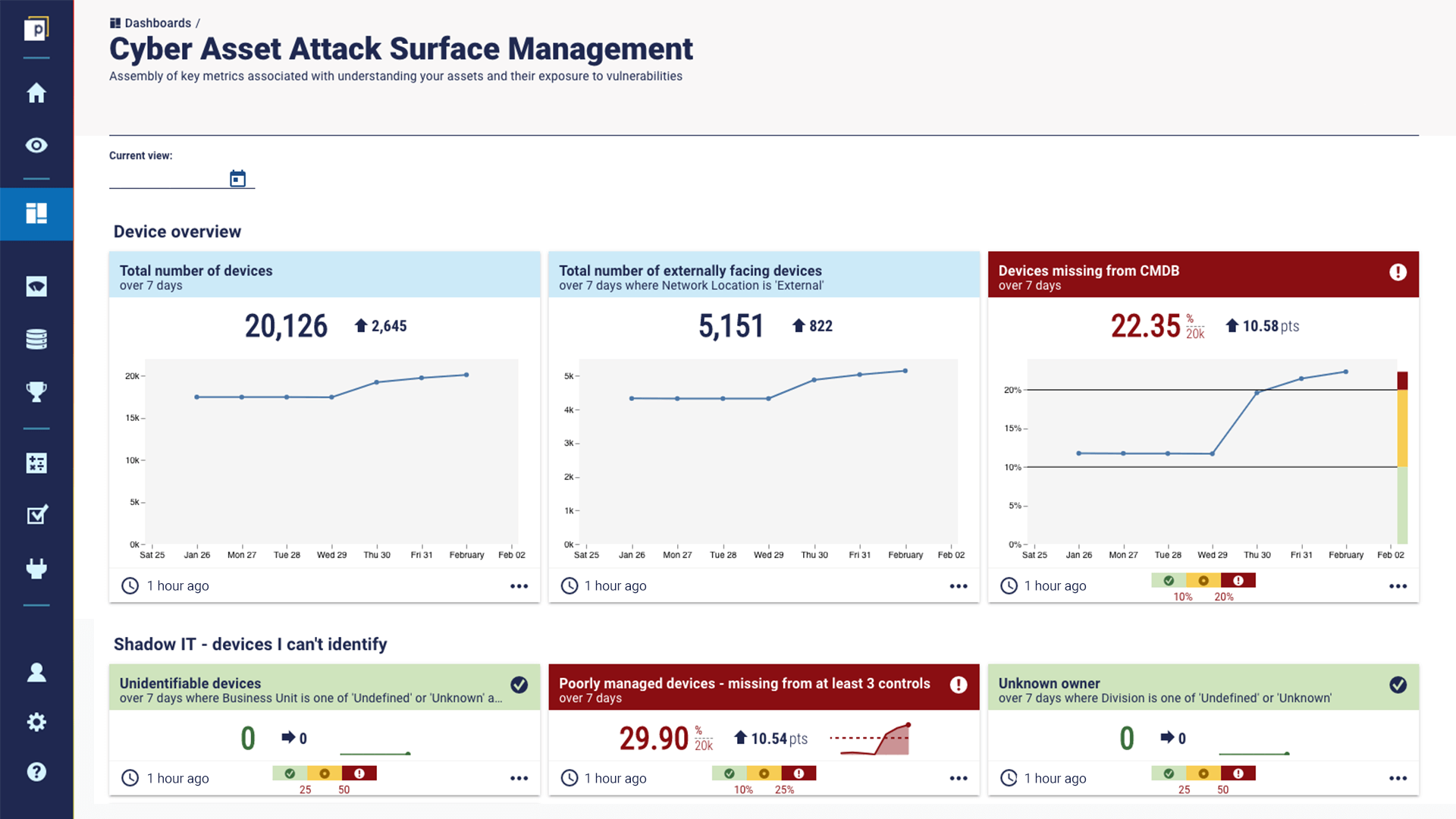
2. Is your CAASM tool fully automated?
Automation is essential for not only creating the asset inventory, but also keeping it up-to-date. Without high levels of automation, a CAASM tool will only add to the manual processes you’re already doing to keep your inventory consistent and measure your attack surface. Automation is a crucial part of CAASM. It drives consistency and trust in processes. The more automation in a process, the less likely it is that human or manual error can sneak in.
3. What does your CAASM tool tell you about your assets?
It’s one thing to know how many assets you have on the network, but you really need a lot of information about each one. Let’s take devices as an example. You will want to know the device type – endpoint, server, cloud server, virtual machine, etc. You’ll want to know what operating system it’s running. You need to know where it is in the world, what business unit it belongs to, who owns it. Context is crucial.
4. Can your CAASM tool show security controls coverage?
Controls coverage is difficult to measure. It requires that the tool have complete inventories, plus evidence of the efficacy of various security controls in place on each asset in those inventories. You have a lot of security controls and tools protecting your organisation. Our 2022 Security Leaders Peer Report found that the average enterprise has 76 security tools. If you want to know how effective your controls and tools are, CAASM can help with that. For example, Panaseer’s CAASM platform continuously monitors vulnerability and patch controls, highlighting gaps in coverage. That way you can easily see where to remediate toprevent control failures, which are one of the leading risks for cybersecurity breaches. Here's an example dashboard of how our CAASM platform shows controls coverage gaps: 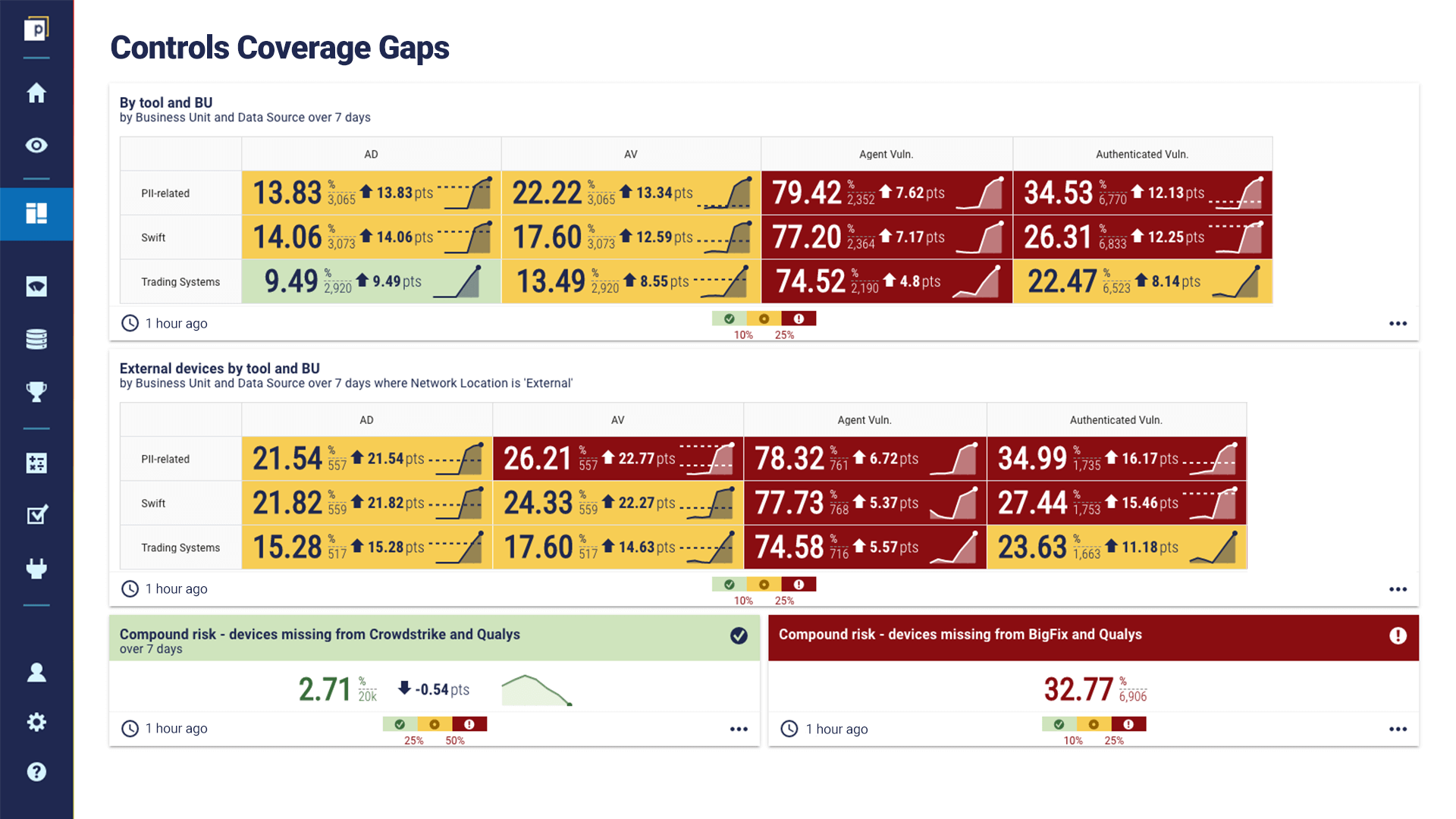
5. Can it help to prioritise remediation?
When you’ve got thousands of vulnerabilities in your network, how do you prioritise which ones to remediate first? Most usually go for a severity scale – critical, high, medium, low. Go for the criticals first, then the highs, and maybe the mediums if you get time. Probably ignore the lows. But what if you have more criticals than you can handle? How do you prioritise those? A good CAASM tool can help. We mentioned above the importance of context around your assets. If you have 1,000 critical vulnerabilities, but you know that 100 of those are on internet-facing systems, you would go for those first. If you know that 10 of those 100 are on internet-facing systems that are also crucial to a business-critical process (such as payments), then you know to go for those first. That’s the power of a good CAASM tool. It allows you to focus on the vulnerabilities that carry the most risk to the business. 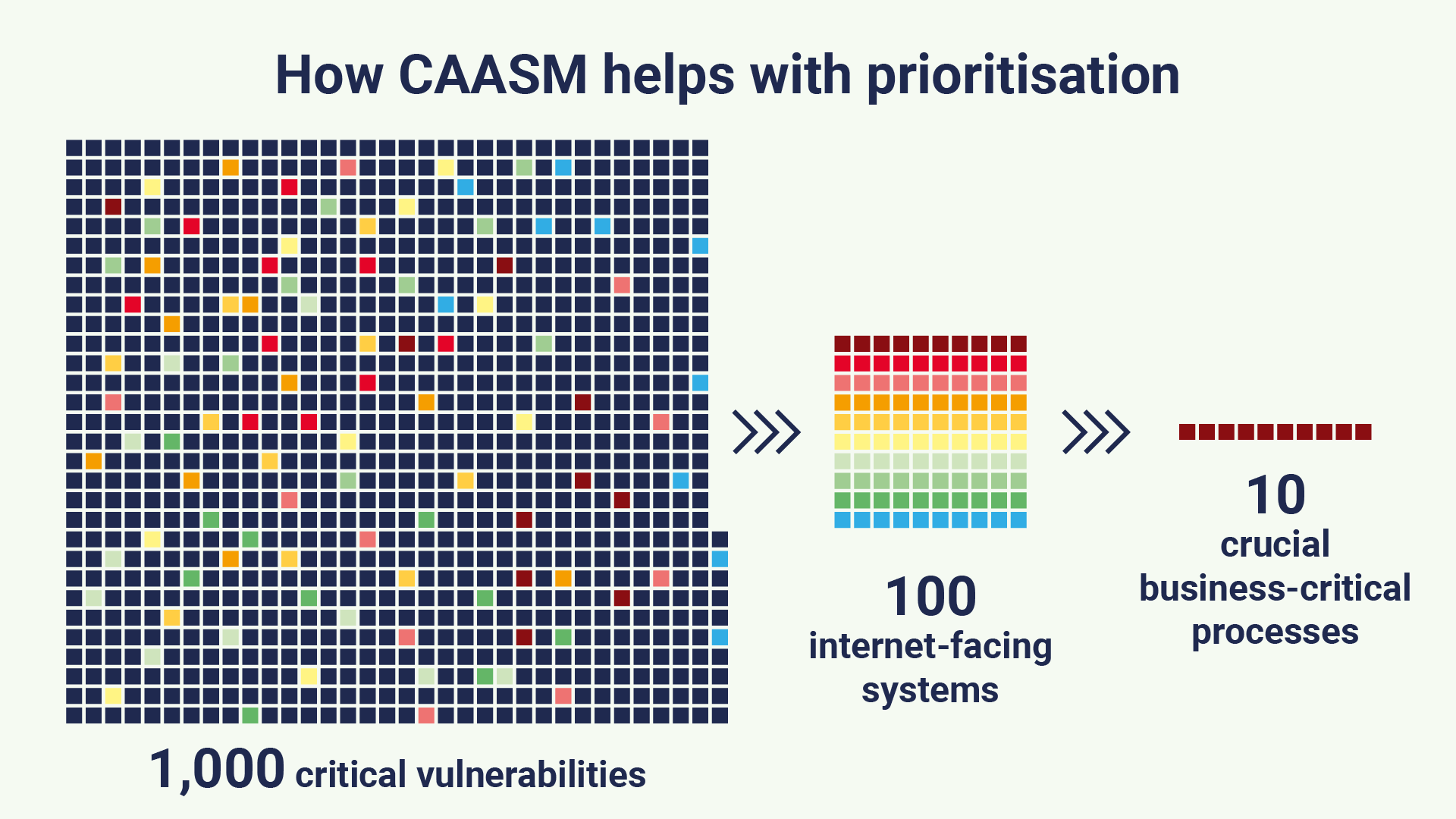
6. Can you share dashboards with key stakeholders?
Security is a company-wide effort. You’ve got to report it to multiple stakeholders across the business and beyond. The board, IT, GRC, audit, regulators, and more. They all need to rely on the information you’re providing to make important decisions to reduce cybersecurity risk. That means your CAASM tool must be able to share and tailor dashboard views. There’s no point sharing information with someone if they won’t understand it. You may need to report the same thing to both the board and IT remediation team. There’s a knowledge gap there that needs to be bridged with tailored dashboards for appropriate audiences.
7. Can you query the data?
CAASM tools bring together data from across multiple security, IT, business and HR tools. You’ve got fantastic, powerful dashboards at your fingertips. But what if you get an ad hoc question that isn't covered by any of your dashboards? You need to be able to query all that data in order to answer such questions.
8. Can you benchmark against best practices?
There are two ways a CAASM tool can support benchmarking against best practices. The first is measuring against or aligning to security controls frameworks or regulations. According to Phyllis Lee Senior Director for the CIS Critical Security Controls: “Every organisation has limited resources, so you really need to align yourself with a security framework that helps your organisation prioritise within your business needs.” Frameworks are crucial to any security controls or measurement programme, so it is important that your CAASM tool has that capability. The second is measuring against your own thresholds or SLAs. Our platform has what we call Control Checks, which are tailored to your organisation’s specific goals or unique standards, which may differ from an established external benchmark.
9. How long does your CAASM tool hold data?
The goal of a CAASM tool is to show you an up-to-date view of your cyber assets and attack surface. That’s extremely valuable. But, what if you are breached and want to look at your cyber assets and attack surface on the day of that breach? Ideally, you’d want to query your CAASM tool to find out. Similarly, once you’ve got your CAASM tool, you’ll be putting in a lot of effort to improve the numbers it shows you. You’ll therefore want to see your performance over time, so you can measure drift and track improvements. A good CAASM tool will hold historic data in perpetuity (or however long you want it to), so that you can go back and look at a specific date, as well as track your goals over time.
The final word
These are just a handful of questions we suggest you think about or ask when looking for a CAASM tool. If you want to learn more about CAASM, get in touch to speak to one of our team and arrange a 30-minute demo.


