
US cybersecurity legislation: Winds of change all blow in one direction
US regulators are placing greater scrutiny on how organizations measure and mitigate cybersecurity risk.
The Biden/Harris National Cybersecurity Strategy is just the latest in a steady stream of significant developments in security legislation coming from the USA in recent years. States, commissions, agencies, and national administrations have all created requirements for organizations to formulate, measure and evidence cyber risk and associated policies, as well as placing more of the accountability onto boards.
A common theme of these developments is that the requirements are principle based, rather than prescriptive, and focus on how the risks presented by cyber threats are being provably managed.
Every organization, no matter how mature they are from a cybersecurity perspective, will be pressured to do more for cyber threat assessment, risk management and ultimately resilience – and should expect further reporting and oversight in these areas.
A strategic response to SolarWinds
A few weeks before the inauguration of the 46th president of the United States, the enormity of one of the most serious cybersecurity breaches to date, namely the compromise of the popular SolarWinds Orion software, was coming to light. Departments including Homeland Security, Health, Energy, and the national Nuclear Security Administration were among the many victims.
This attack compromised the update delivery mechanism of a highly-regarded security company and remained undetected for almost a year despite successfully infecting many organizations with world-leading security teams. It was the very definition of a sophisticated cyber-attack.
It’s no coincidence, then, that one of the earliest Executive Orders from the Biden/Harris administration was EO14028, signed 12 May 2021, simply titled “Improving the Nation’s Cybersecurity”.
It stated: "It is the policy of my Administration that the prevention, detection, assessment, and remediation of cyber incidents is a top priority and essential to national and economic security. The Federal Government must lead by example. All Federal Information Systems should meet or exceed the standards and requirements for cybersecurity set forth in and issued pursuant to this order." This EO mandated improving security through:
- Removing barriers to sharing threat intelligence
- Modernizing federal government cybersecurity
- Enhancing supply chain security
- Establishing a cyber safety review board
- Standardizing playbooks and improving detection of vulnerabilities, as well as investigative and remediation capabilities
The order mandates principles such as adopting zero trust strategies and ensuring SBOMs are available throughout supply chains, and also technical requirements that include the use of MFA, risk-based authentication, conditional access and EDR as examples.
NIST is one of the agencies assigned responsibility for delivering against this EO, and its summary is telling. It’s all about supply chain:
"Section 4 directs NIST to … identify existing or develop new standards, tools, best practices, and other guidelines to enhance software supply chain security. Those guidelines, which are ultimately aimed at federal agencies but which also are available for industry and others to use, include: criteria to evaluate software security, criteria to evaluate the security practices of the developers and suppliers, and innovative tools or methods to demonstrate conformance with secure practices."
The need to use innovative tools or methods to demonstrate conformance is striking. It suggests that the challenge here isn’t in having extra controls, but rather in ensuring that such controls are actually in place.
Improving public disclosure on cyber incidents and cyber governance
Away from the highest branch of the Executive, the Securities and Exchange Commission on 9 March 2022 proposed new rules on cybersecurity risk management, strategy, governance and incident disclosure. It will impact all public companies, with the following rationale:
The proposed amendments are designed to better inform investors about a registrant’s risk management, strategy, and governance and to provide timely notification of material cybersecurity incidents. Consistent, comparable, and decision-useful disclosures would allow investors to evaluate registrants’ exposure to cybersecurity risks and incidents as well as their ability to manage and mitigate those risks and incidents.
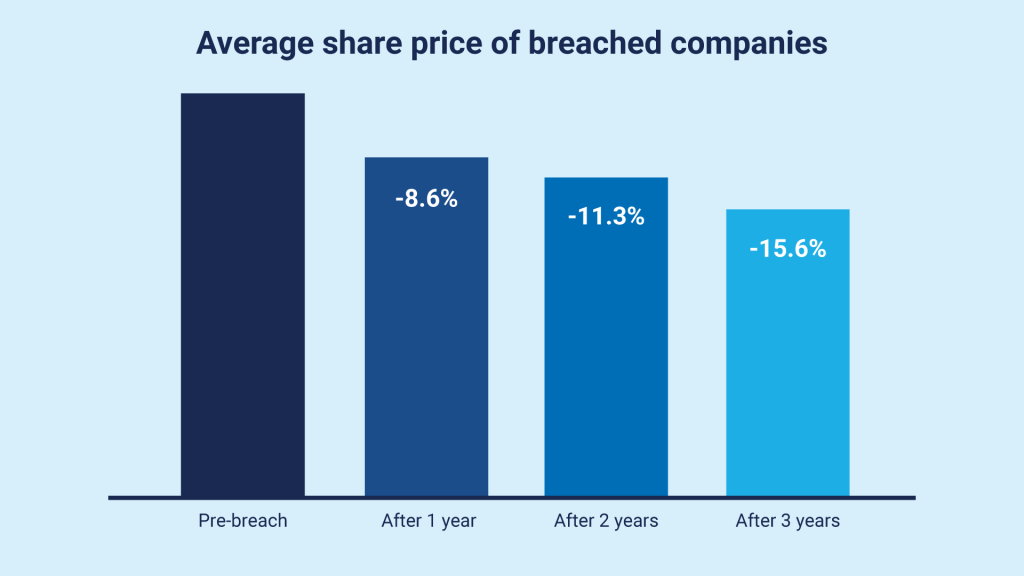
There have been many examples of where a company’s stock has been significantly hit following disclosure of cyber-attacks. Research from Comparitech found that breached companies suffered an average 8.6% drop after a year, which continued downwards to 11.3% after two years, and 15.6% down by year three. The SEC must have decided enough was enough, and investors needed better information around risk on which to base their decisions.
 There are two major topics proposed in the amendments, covering incident disclosure and risk management, strategy and governance disclosure.
There are two major topics proposed in the amendments, covering incident disclosure and risk management, strategy and governance disclosure.
Disclosure of a material cybersecurity incident needs to happen within four days of discovery of the incident. Previously disclosed incidents require updates and also “multiple previously undisclosed individually immaterial incidents that have become material in the aggregate” must be disclosed. A four-day reporting window appears generous, but in the heat of an incident this adds pressure to organizations, so preparation is key.
Risk management, strategy and governance requires disclosure of policies and procedures (“if any”, the proposal notes!) for the identification and management of risks from cybersecurity threats. It also requires the board’s oversight of cybersecurity risk to be shared, along with management’s role in assessing and managing cyber risk and in implementing policies, procedures and strategy around cybersecurity.
Tellingly, board members’ experience with cybersecurity must be disclosed, including the nature of any expertise on an individual-by-individual basis.
These proposals place new reporting requirements on organizations, and there’s a subtext there that policies and expertise are going to be material in the decisions investors make. Public companies will simply have to be able to demonstrate their cybersecurity posture and associated exposure management approach to secure investor confidence. It’s not enough to merely have such policies, evidence of adherence and efficacy of those policies will be of critical importance.
How do you evidence your security posture?
Shortly after the SEC’s proposal landed, the Biden/Harris administration issued a National Security Memorandum. Which built on the previous year’s EO14028. This was a significant change that extended the scope from federal civilian networks to national security systems. And stipulated that organizations must be able to prove that their security posture would be effective against evolving cyber risks. Tellingly, there is a lot made of zero trust architecture among the hard deadlines for all agencies to abide with.
Moving forward to November 2022, the New York State Department of Financial Services – which regulates all financial service institutions chartered in New York state – issued a proposed amendment to their current cybersecurity regulation. This adds further principle-based requirements around governance, policy implementation and evaluation based on more regular cyber risk assessments, puts the CISO firmly on the hook for cybersecurity risk and mitigation, and – similar to EO14028 – mandates certain technologies be used such as MFA, EDR and more.
"With cyber-attacks on the rise, it's critical that our regulation keeps pace with new threats and technology purpose-built to steal data or inflict harm,” said Superintendent Harris. “Cyber criminals go after all types of companies, big and small, across industries, which is why all of our regulated entities must comply with these standards – whether a bank, virtual currency company, or a health insurance company.”
These regulations update existing requirements and will place further reporting demands as well as technical and training demands on financial institutions. It's somewhat akin to the EU’s Digital Operational Resilience Act (DORA) in intent and once more requires continuous monitoring of controls.
Expanding strategic visions for cybersecurity
Most recently, the Biden/Harris administration announced its National Cybersecurity Strategy, which aims to secure the full benefits of a safe and secure digital ecosystem for all Americans. It will rebalance responsibility for defending cyberspace “onto the organizations that are most capable and best positioned to reduce risks for all of us”, and realign incentives to favor long-term investments, rather than give a short-term view on urgent threats.
"The United States will reimagine cyberspace as a tool to achieve our goals in a way that reflects our values: economic security and prosperity; respect for human rights and fundamental freedoms; trust in our democracy and democratic institutions; and an equitable and diverse society. To realize this vision, we must make fundamental shifts in how the United States allocates roles, responsibilities, and resources in cyberspace." The “Digital Ecosystem” must be defensible, resilient and values-aligned, and the strategy sets out five pillars:
- Defend critical infrastructure, driving further minimum cybersecurity requirements, enabling public/private sector collaboration at speed and scale.
- Disrupt and dismantle threat actors, using all tools of national power, getting the private sector involved in disruption, and taking a federal and international approach to ransomware.
- Shape market forces to drive security and resilience by promoting privacy, shifting liability for software products and services to promote secure development practices, and ensuring federal grant programs invest in infrastructure that is secure and resilient.
- Invest in a resilient future through reducing systemic vulnerabilities in the foundation of the internet and across the digital ecosystem, prioritize cybersecurity R&D, and develop a diverse and robust national cyber workforce.
- Forge international partnerships to pursue shared goals, leveraging international coalitions, increasing partner capacity to defend against cyber threats and working with allies to create trustworthy global supply chains for ICT and OT products and services.
These are bold objectives, and in some cases imply significant changes. Bearing in mind the ultimate aim is to shift responsibility for cybersecurity to those that are best positioned to provide it, this will have significant impact on service, solution and software providers across the entirety of the US.
Proving compliance with continuous controls monitoring
All these developments are clearly pointing in the direction of driving more visibility, more accountability, clearer policies that mitigate cyber risk, and more evidence of policy, procedure and compliance to more parties.
In turn, this mandates an approach to cybersecurity threat exposure management that changes compliance and audit from being point-in-time exercises to a continuous process in order to properly manage risk, which demands an automated approach to cybersecurity posture management.
This requires a platform that can understand the totality of your cybersecurity tooling, with business context to give risk perspectives. The data needs to be verifiably accurate to drive the change in accountability for security posture that needs to happen throughout organizations.
It needs executive oversight and to give insight, as well as delivering the capabilities to implement and evidence cybersecurity policies. Panaseer can help with all aspects. We’re uniquely placed to help evolve your cybersecurity approach to the levels expected by these regulations and others being passed throughout the world.
Book a demo of the Panaeer platform to see how it improves the way you enforce cybersecurity policies and ensure compliance with regulations.


