
Seven cybersecurity metrics for basic cyber hygiene
The Microsoft Digital Defense Report found that basic cyber hygiene protects against 98% of attacks. We explore crucial areas of cyber hygiene and highlight key supporting metrics.
We're joined by Stuart Aston, National Security Officer at Microsoft UK, and cybersecurity veteran. He’s been in the industry since the late ‘80s and has been making public impassioned pleas about the importance of cyber hygiene since 2006. I can neither confirm nor deny whether he had a hand in the aforementioned report, but he quoted it unprompted several times.
Nevertheless, when you’ve been in the game for decades there’s always some wisdom to share. In this article, we explore a range of protections and metrics such as:
- What is cyber hygiene and why is it important?
- Metrics to support cyber hygiene
- Asset management
- Anti-malware
- The principle of least privilege
- Multi-factor authentication
- Patch management
- Permitted programs and applications
- Data security
What is cyber hygiene and why is it important?
“Cyber hygiene to me is doing the minimum amount of work in order to maximize the amount of work the bad guy has to do,” explains Stuart.
“The majority of work that we security practitioners see comes as a direct failing of a bucket of things that we call cyber hygiene. 98% of attacks that we see could be defeated with cyber hygiene. And that’s across the 23 trillion signals we see every single day at Microsoft.”
Cyber hygiene isn’t about stopping every attack, it’s about getting the basics in place so you stop commodity attacks.
“If they’re determined enough and willing to spend enough money, ultimately the bad guys can get in. Genuine zero-days and high-level tradecraft are rare and expensive attack techniques. The challenge really is that if you don’t have basic cyber hygiene, they’re getting in for free, with minimal effort.” You want to break the threat actor’s value chain and destroy their return on investment. Cyber hygiene is about putting controls in place to make the bad guy’s job difficult.
Most organizations will have these tools and controls in place already, but deployments are prone to gaps and control failures. Therein lies the challenge.
Metrics to support basic cyber hygiene
Stuart outlines seven areas of cybersecurity that support cyber hygiene: asset management, anti-malware, privilege, multi-factor authentication, patching management, permitted programs, and data security.
He talks us through each section and provides example metrics.
1. Asset management
“Asset management is absolutely key,” says Stuart. “Put simply, if I don’t know where my machines are, how can I know they are appropriately controlled and managed? If I don’t know what machines I have, I almost certainly don’t know all the software running on those machines. If I don’t know all the software I have, how can I keep it up to date?” There’s a reason security frameworks start with asset management.
Metric: Inventory completeness (in this case, % devices in the CMDB)
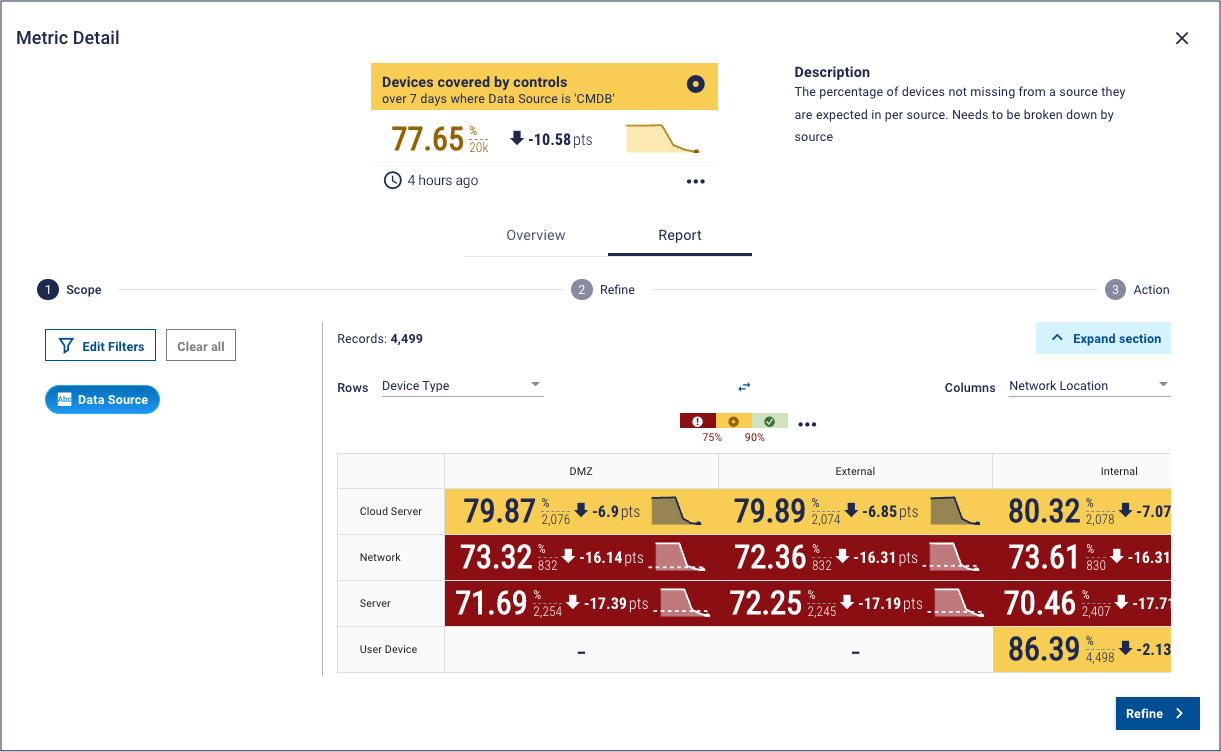
This dashboard from the Panaseer platform shows how we help in this area. By taking data from across a range of security tools, the platform creates a complete “smart inventory”. This metric compares that “smart inventory” to the organization’s CMDB, creating a coverage metric for inventory completeness. The second part of the metric specifies a view of inventory completeness for device type and network location, which can help to identify areas for prioritization.
2. Anti-malware
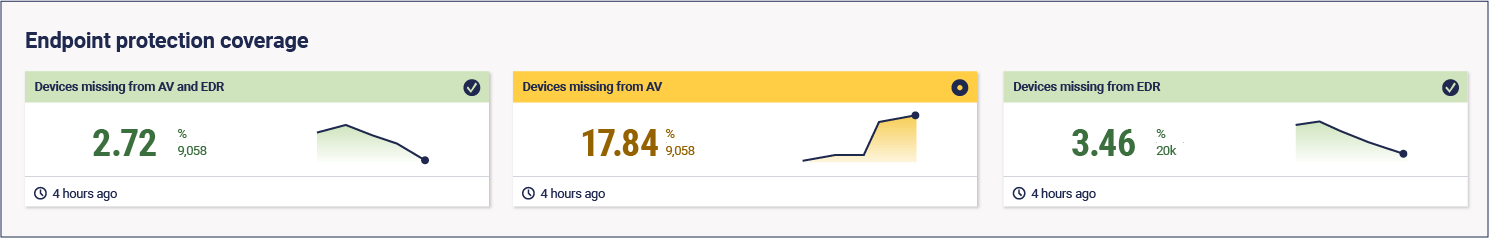
Using anti-malware software is essential for cyber hygiene. Whether it’s a high-flying next-gen EDR tool, platform native antivirus, or ideally both, anything is better than nothing. It’s also important to keep that software up to date – not just with patching vulnerabilities, but with the latest versions of your anti-malware software too.
Metric: anti-malware tool coverage
3. The principle of least privilege
“Most organisations will give a person the full set of privileges they need to do their job, and then leave them there. This is great news for an attacker.”
A common attack path is to compromise someone who has unnecessary local admin rights and then look for lateral movements to find higher privileges. But if a threat actor compromises a domain administrator (which can be done with a well-crafted attack), then they don’t need to escalate privilege once inside the organisation because they own it already. “Compromising one single person can compromise the entire organization.”
That’s why we should be utilizing the principle of least privilege. Instead of having permanent privileged accounts, domain administrators should be provided with single-use accounts as and when required, which are used then discarded.
Stuart added: “This reduces the window of opportunity for the adversary, and more importantly, removes their ability to persist in a meaningful way. This is an effective way to reduce blast radius in the event of compromised privilege.”
These single-use accounts can also act as “canaries” in your organization. The account is “dead” to you, so if you see any activity on it, you know that it has been compromised and you must take action.
“Done right, least privilege is a 2-for-1 deal.”
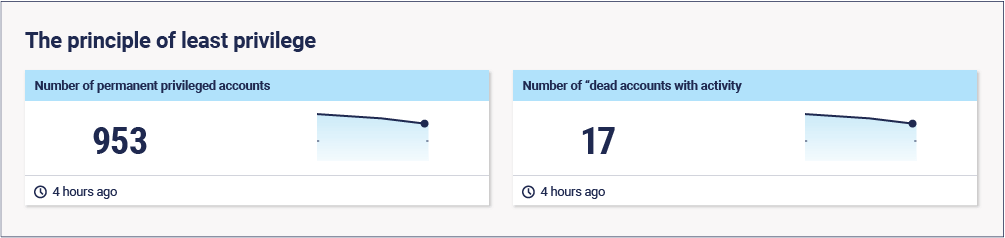
Metrics:
- Number of permanent privilege accounts (lower is better)
- Number of “dead” accounts with activity (lower is better)
4. Multi-factor authentication
“If 98% of attacks can be defeated by cyber hygiene, around 90% of those will involve a compromised identity. The majority of identity compromises come from simple password sprays.”
“Often people use the same password for every account,” says Stuart. “There is a certain dating site that will remain nameless that was compromised. Thanks to the frequency of re-using passwords and signing up with work email addresses, this led to the further compromise of many passwords at a large global enterprise, which will also remain nameless. So, it does happen.”
Using multi-factor authentication eliminates this problem. “Using a second factor of authentication that’s meaningful is so powerful. It mitigates attacker persistence and access, plus it provides an additional alert signal in the event of an attack.”
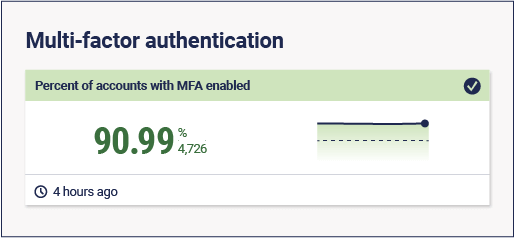
Metric: % accounts with MFA enabled
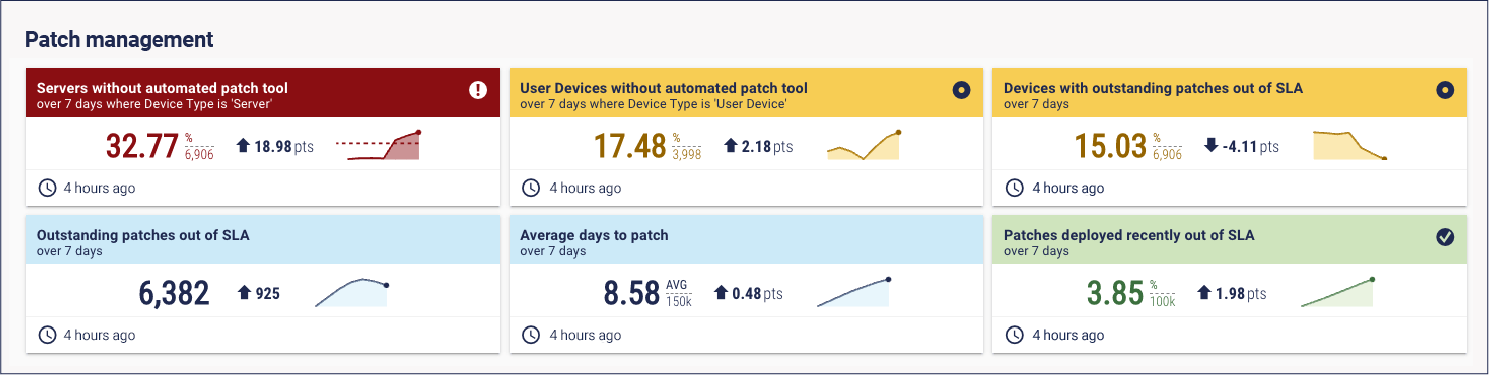
5. Patch management
“This is the thing I’ve been talking about since 2006. Keep your software up to date.” As with many aspects of cybersecurity, it’s easier said than done.
“An adversary does not want to utilize a zero-day attack. They want to exploit existing software vulnerabilities, because it’s cheaper and easier. Adversaries can reverse-engineer exploits in minutes. That means, ideally, we would be patching in real-time. That’s not realistic, though, so we should aim for seven days.”
But patching isn’t that easy. “Most patches are straightforward these days, but someone will always remember that patch that failed in 2006 and ruined their life.” People can be apprehensive about patching. But the fact is you need to do it, and the quicker the better.
Metric: % critical and high vulnerabilities patched within seven days
6. Permitted programs
Every organization should have a list of permitted programs and applications. Permitted applications and folder protection is built into every version of Windows. There’s no excuse not to use it.
“And while you’re at it,” says Stuart, “you need to make sure that the applications running in your environment can’t write to their own program directory. That’s a real problem, especially if you’ve never patched it, because it can change executable code.”
Metric: Can users write to their own program directory? Y/N
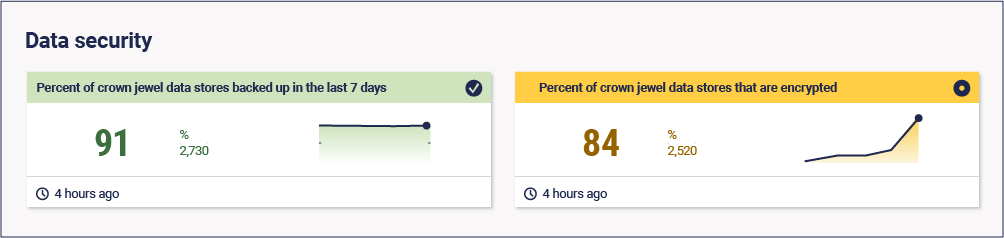
7. Data security
“Fundamentally, what we are trying to do is to protect data. That’s what the bad guys want. Whether they ransom it, steal it, delete it, or deny you access to it.”
But organizations house a lot of data. To make it a bit easier, we can identify our most important data – the “crown jewels”. The 11 herbs and spices, the Pepsi recipe, or missile codes (just to add some danger to what would otherwise essentially be a Happy Meal). These are the things we want to ensure have extra protection, such as the single-use access we mentioned earlier, encryption, and backups.
Metrics:
- % crown jewel data stores backed up in the last seven days
- % crown jewel data stores that are encrypted
The bottom line
Cyber hygiene is hugely important. We’ve looked at seven key areas that the average enterprise security program will likely already address with different cyber control domains – asset management, antimalware, privilege, MFA, patching, application and program management, and data security.
Most organizations already have tools and controls around these areas, so they’ve got what they need to achieve basic cyber hygiene, and therefore stop otherwise preventable breaches. The challenge is that there will be gaps in these tools and controls. A mature security metrics and measurement program helps organizations identify and fix control failures, boosting cyber hygiene and security posture.
If you want to see how Panaseer does exactly that with Continuous Control Monitoring, get in touch.

