
Why accountability for cybersecurity risk can't only fall to the CISO
New legislation such as DORA and proposed SEC regulations are putting greater focus on accountability in cybersecurity. There are ongoing challenges with accountability in cybersecurity. “Accountability” often means "who can we blame?".
You may have heard the joke that CISO stands for Chief Incident Scapegoat Officer in the event of a significant breach. But that’s an outdated and flawed approach.
While board members and the CISO are ultimately on the hook for security, the reality is that responsibility for cybersecurity is spread across multiple people, in multiple teams, throughout the company and beyond. That’s why the CISO must drive accountability as well as responsibility for security throughout the organization via security culture and training. In fact, new regulations like the EU's Digital Operational Resilience Act (DORA) are making cybersecurity training mandatory.
And let’s not forget third-party supply chains – they also have a responsibility to their customers to be secure.
With cybersecurity now one of the biggest risks for businesses, it's important to understand both who is accountable for cyber risk and the role everyone has in maintaining a strong security posture.
How do new regulations impact cybersecurity accountability?
In casual conversation, it’s common to use the words “accountability” and “responsibility” interchangeably. If you want to get technical, accountability is about ensuring something is done, and responsibility is about doing the thing.
New cybersecurity regulations, specifically DORA and proposals from the Securities and Exchange Commission (SEC), shift accountability for security risk to the board.
To take the new EU law DORA as an example: the board is ultimately accountable for ICT risk, with the potential risk of penalties to both the organization and the individual. Boards must be educated in the threats and risks stemming from digital and ICT activity, that is to say, they'll need to be more cybersecurity savvy and understand the impact and extent of that accountability. For more on the implications of DORA specifically, check out our whitepaper on What security leaders need to know about DORA.
Similarly, the SEC in the US put out a consultation paper last March proposing, among other things, new requirements around the board’s cybersecurity expertise and oversight of cybersecurity risk. The SEC plans to put more burden on publicly traded companies to give investors better insight into their security posture.
This is part of a broader legislative trend among commissions, agencies and administrations at both a State and Federal level that places more requirements on organizations to measure and evidence cyber risk and associated policies, as well as making board members accountable. This includes Biden's recent announcements on the US National Cybersecurity Strategy.
Additionally, the National Association of Corporate Directors (NACD) and Internet Security Alliance (ISA) jointly released the 2023 Director's Handbook on Cyber-Risk Oversight last week, which aims to empower boards to improve their organization's cyber-risk oversight. In her announcement tweet, Director of the Cybersecurity and Infrastructure Security Agency (CISA) Jen Easterly said: “Cyber risk must be seen as a fundamental business risk — one that is owned & managed by the CEO & Board as a matter of good governance.”
While the handbook doesn’t hold any legislative power, its principles have influenced the National Cybersecurity Strategy.
Who is accountable for cybersecurity risk?
Cybersecurity responsibility is shared by every employee in the organization. Everyone needs to have a basic understanding of threats and how to avoid them – using MFA, good password hygiene, spotting a phish, and more. Organizations should have a training and readiness plan in place (in fact, DORA mandates cyber training for all staff, so it is a legal requirement for many companies). On top of that, the security team has a responsibility to protect the organization with security processes and controls, and to fix problems that arise.
But if it all goes wrong, who is accountable?
Too often it’s the Chief Incident Scapegoat Officer. Gartner research found that accountability for cybersecurity risk sits with the CIO, CISO, or equivalent in 86% of organizations.
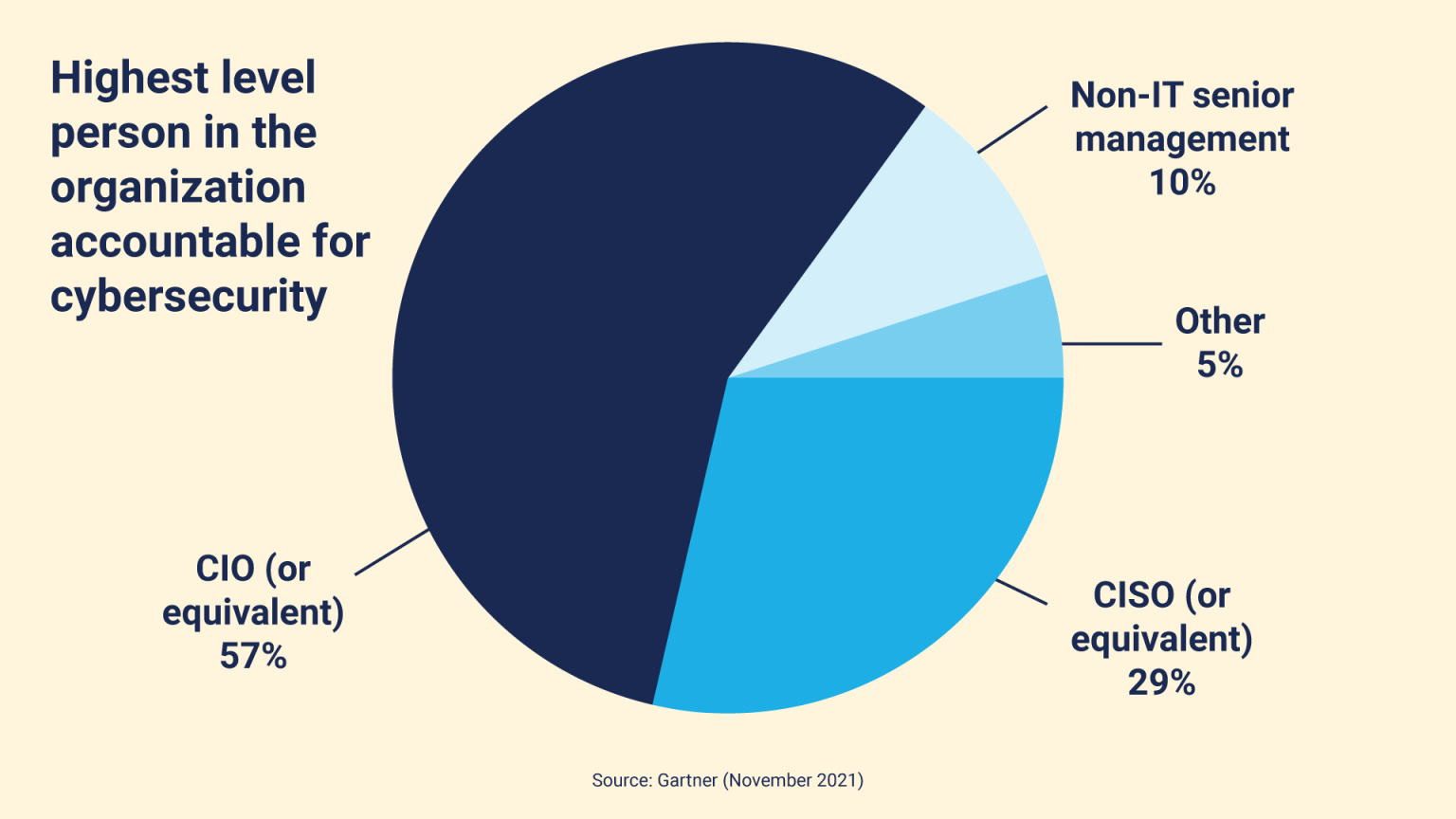
The Gartner research noted that: “IT and security leaders are often considered the ultimate authorities for protecting the enterprise from threats. Yet, business leaders make decisions every day, without consulting the CIO or CISO, that impact the organization’s security.”
The report found that 88% of boards recognize that cyber risk is a business risk, and that is likely to increase further thanks to incoming regulation. As noted, boards at financial services firms operating in the EU will be held accountable for cybersecurity risk. And chances are, such regulations will lead the way globally, and we may see similar legislation cropping up in the next few years.
Who is accountable for day-to-day cybersecurity?
The board may be accountable for the organization’s overall cybersecurity risk, but they certainly aren’t “doing” security. Boards are accountable for cybersecurity externally, but internally that accountability can be pushed down the hierarchy.
The board may hold the CISO accountable for cybersecurity, who can delegate accountability for separate parts of the business to BISOs (business information security officer), and then onto the teams and individuals responsible for day-to-day cybersecurity.
But then come the inevitable questions. Who owns x? Who is responsible for y? Who needs to fix z?
As people are responsible for more and more devices, applications, accounts, it can become difficult to keep track of it all, let alone who is accountable for individually securing all those assets. Organizations often lack visibility across ownership of assets thanks to incomplete inventories. There is rarely a centralized hub or single source of truth that records unequivocally who is accountable for what. This lack of visibility hinders not only the influence of security leaders, but also the day-to-day running of security and IT teams.
Driving positive change through security accountability
When you’re talking about responsibility and accountability in cybersecurity, many people jump immediately to: “Who is to blame?”
This is perhaps more of a cultural problem within enterprises. An effective cybersecurity culture isn’t just about employees being able to spot a phish or password hygiene. It’s also about having a supportive ethos around cybersecurity and recognizing that one person can rarely be the sole cause of an incident. It’s better to establish a fix-first attitude, rather than a blame-first attitude.
As with security posture management, there are active and reactive approaches to cybersecurity accountability. These can fall into positive or negative approaches.
For example, with active security the positive approach is to seek ways to improve your security posture...
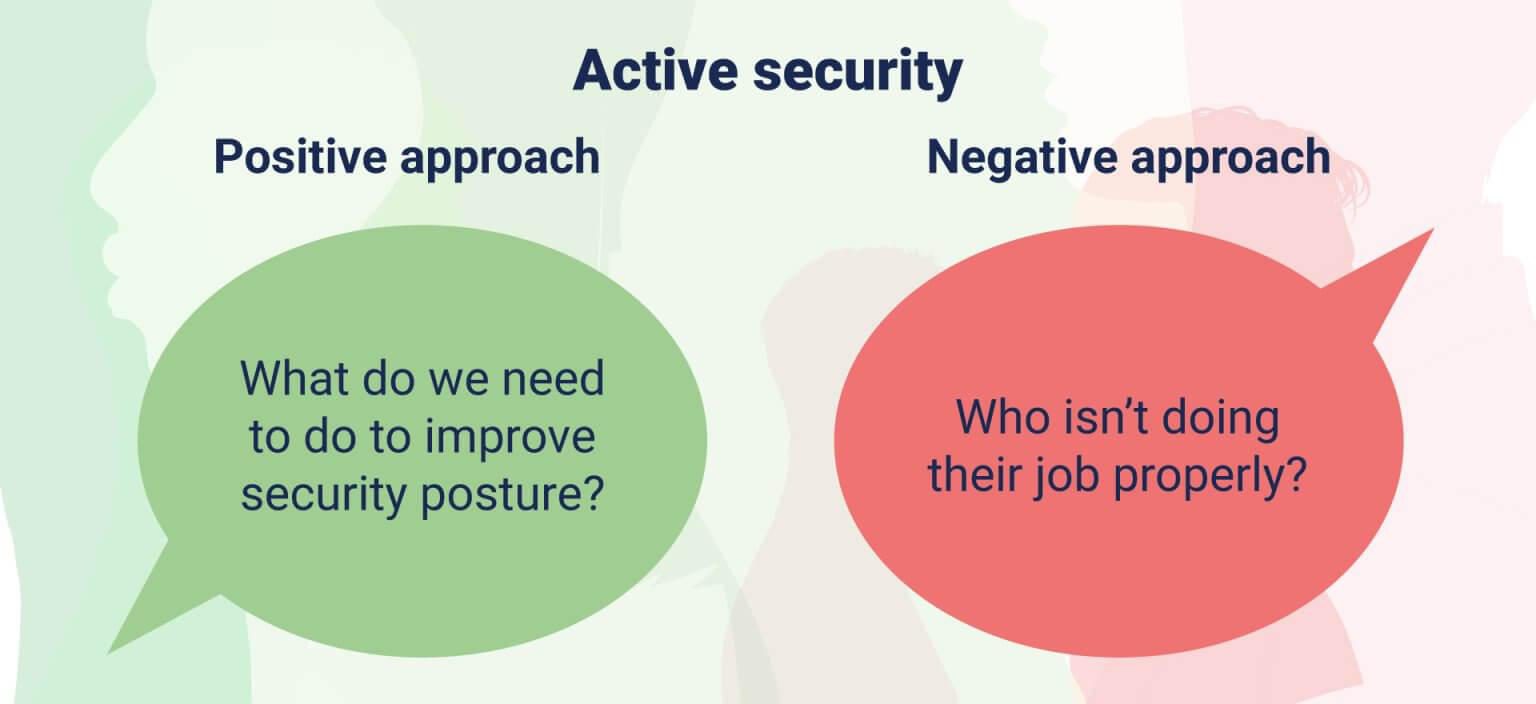
...and similarly with reactive security it's better to think about how to learn from problems rather than start a witch hunt.

By adopting a positive, supportive mindset, you can encourage people to take more accountability for cybersecurity across your organization. This can in turn lead to improvements in your overall security posture management.
How Panaseer improves accountability in cybersecurity
Panaseer can help security and IT teams overcome issues around accountability for security controls and remediation. The Panaseer platform continuously updates asset inventories to provide a near real-time view of ownership across all your IT assets.
This single source of truth provides data you can trust by drawing on traceable data sources from your existing security tools. Stakeholders are given a transparent view of the data journey and understand why it’s reliable.
And beyond that visibility, Panaseer also helps with prioritization. So not only can you effectively show who is responsible for what, but also what they should work on first.
It enables CISOs to improve accountability responsibility within the security team and exert influence across the wider business. Because the single source of truth can be split by function, a CISO can assert, with evidence that the business has already agreed upon, that specific functions are responsible for x, y, or z.
In the platform, customers can look at an asset, in this case a server (1); then identify and prioritize any problems on that device (2); and then who owns or manages it (3); and any other devices they manage (4).
1 – The status of a device.

2 – The vulnerabilities on that device – sorted by priority.

3 – The manager of that device...

4 – ...as well as any other devices they’re responsible for.

But… it’s not about blame
With so much focus on accountability in cybersecurity, there's an opportunity to change the blame culture that often overshadows security posture management.
It begins with being able to celebrate successes — don’t single out individuals for punishment when a group has challenges. If a team has patched 99% of vulnerabilities, that’s a huge win. Celebrate it. Don’t criticize the 1% that’s not patched.
We have an “amnesty” implementation approach at Panaseer. When an organization switches on the Panaseer platform for the first time, they’re almost always surprised what the data reveals about the true state of their security posture. But the tool isn’t there to show how bad everything is and identify who to punish. The opposite in fact.
It’s there to promote good security posture management and prioritize actions to improve that security posture. Crucially, it also helps to drive accountability for security posture across the organization by identifying asset owners, managers, and who is best placed to action those improvements
To find out how Panaseer can improve collaboration and accountability for cybersecurity in your organization, get in touch to book a demo.


