
The challenge of active leavers in cybersecurity
'In an ideal world, everything would be easy, connected, and simple. HR and IT would be aligned and know all the accounts this person has, internally as well as externally. Then everything would just disappear, and no-one could use the credentials anymore. Everything would be nice. The reality is often just completely different.' Welcome to the second instalment of our Metric of the Month series. In this series, we want to put a spotlight on a range of valuable and interesting security metrics and measures. We are discussing them with thought leaders in the security and risk industry to share some of their hard-earned wisdom. In this article, we will be discussing active leaver metrics with Andreas Wuchner. Last time, we spoke to David Fairman about Security Controls Coverage. Andreas is a renowned security and risk thought leader and one of Panaseer’s advisory board members. He has over 25 years of experience in senior risk and security roles at global organisations in pharmaceuticals and financial services, including Novartis, Deutsche Bank, UBS, and Credit Suisse.
What are active leaver metrics?
90% of successful attacks start with humans doing something ‘wrong’. If the access rights are also wrong, drama is on the doorstep.
Active leaver metrics are a subset of user-centric security measurements (as opposed to device-centric or network-centric), specifically Identity Access Management (IAM). IAM is a critical part of any enterprise security programme. By defining and managing the access of users, it provides control over who comes in and out of an organisation’s network, which is vital to supporting and securing an environment. Users are the first line of defence when it comes to security. They need and deserve support and training to help protect the organisation. ‘90% of successful attacks start with humans doing something ‘wrong’. If the access rights are also wrong, drama is on the doorstep’, says Andreas. Indeed, zero-day attacks are pretty rare. Most breaches start with a user, whether it’s compromised credentials, clicked links, phishing, or accounts that aren’t properly decommissioned. And here we get to active leavers. Employees and systems with active accounts which are owned by former employees represent a big threat to every organisation. If misused, they can easily allow risks to materialise, like data theft or ransomware-triggered loss of system access. At a really fundamental level, the reason that we measure active leaver metrics is this: people who don’t work for a company anymore, should not have accounts on any company system. Let’s define the term ‘active leaver’. The ‘leaver’ is the person ending their employment at the organisation or moving departments. The ‘active’ refers to the accounts that are still active (i.e. not yet de-commissioned). So, an active leaver is a person who leaves the company or moves departments, where some or all of their accounts and privileges will need to be changed or removed. Measuring active leavers is a key part of IAM measurement, more specifically around joiner-mover-leaver measurement. There is some element of finesse when it comes to ‘movers’ (people moving roles between departments), as Andreas pointed out: ‘It can be a big problem when people move around because they often take their access rights with them’. The key measurements are things like ‘number of active leaver accounts’; ‘time to revoke access since the person has left the company/moved department’. Here’s an example lifted from our platform:
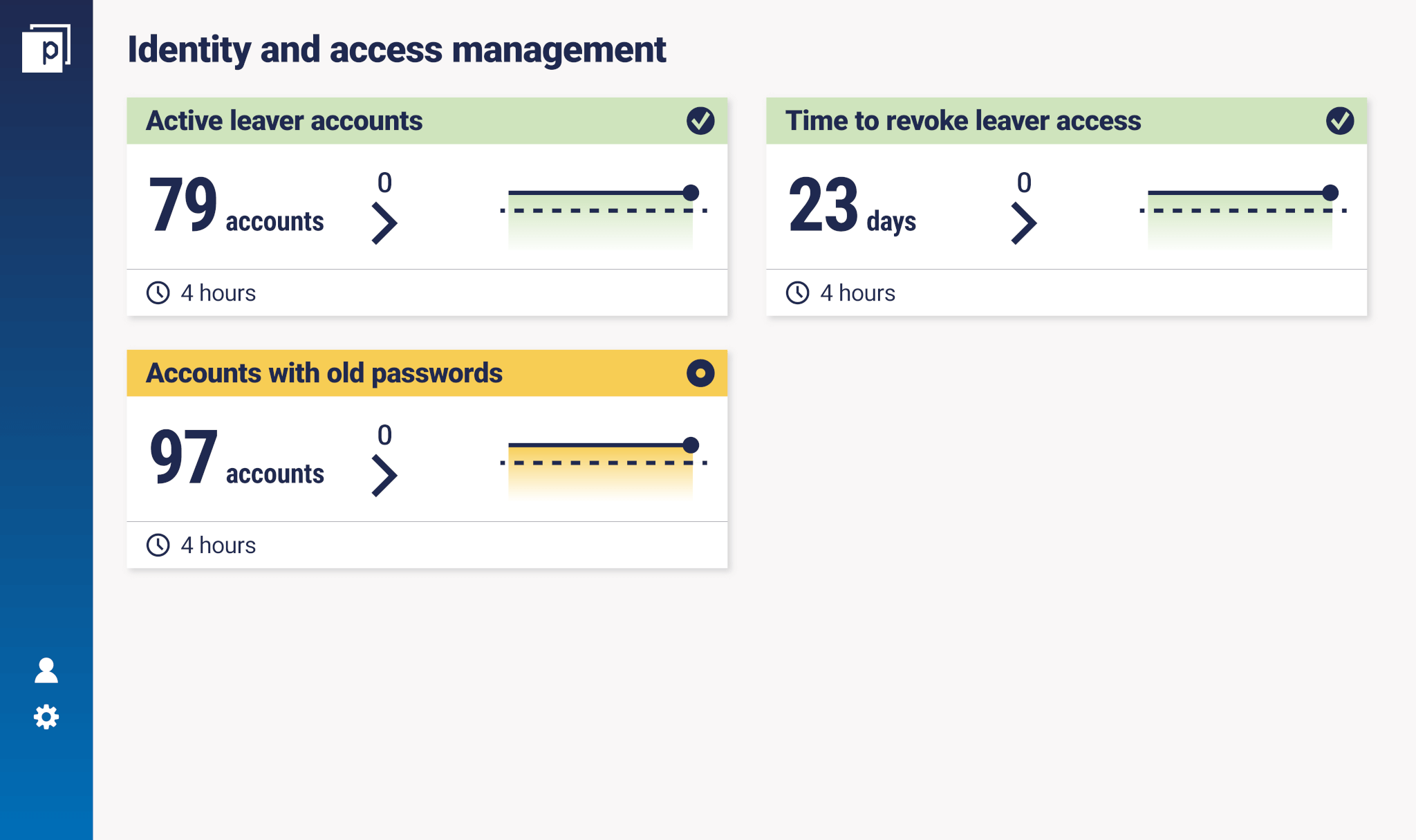
Andreas’ team uses active leaver metrics primarily as a detective control. In some ways, it may be overlooked because it’s not very flashy. ‘Active leaver controls are not necessarily about healing and fixing the world’, as Andreas noted. Instead, it is an essential double-check: ‘This control is about constant learning and having a second pair of eyes on a control which may not be working optimally.’
Why are active leaver metrics challenging?
With that, measuring active leavers seems relatively simple. Just de-commission appropriate accounts when someone leaves the company or moves department. Right? In reality, it can be a challenge to work out. I asked Andreas why:
‘In an ideal world, everything would be easy, connected, and simple. HR and IT would be aligned and know all the accounts this person has, internally as well as externally. Then everything would just disappear, and no-one could use the credentials anymore. Everything would be nice. The reality is often just completely different.
The reality is distributed systems that are not integrated. Third party systems and services where internal IDs are used but not managed through internal central teams. No single team or application knows where or how many different accounts a person has.
I’ve been doing this for 26 years now. I’ve never seen a company that’s had IAM fully under control.
There is also the challenge of users having different identities, because there is often a lack of standardisation. And even if they are standardised, then they still have Wuchner, admin_Wuchner, IT_Wuchner, SAP_Wuchner. If you go into an enterprise you can easily find that people deliberately have several identities. While you find up to 70 accounts per user, you often find IT people that have up to five different identities too.
I’ve been doing this for 26 years now. I’ve never seen a company that’s had IAM fully under control.’
In our experience of providing security metrics and measures for large companies, we have seen time and time again that they struggle with active leavers. As Andreas highlighted, there are disparate systems or functions that do not communicate in an adequate way. While HR would know someone has left or moved department, that has to be sent to the people responsible for decommissioning access to their various accounts. This can be a manual and messy problem, prone to human error.
Why are active leaver metrics important?
When I asked Andreas about the importance of these metrics, he reiterated the importance of IAM more generally, and that a high percentage of attacks come down to human error, which can combine with poor access management to cause, as we said earlier, ‘drama’.
You will find that people with 25 years in an organisation will still have access rights for a team that they left 10 years ago. You may be lucky enough that, while the access is still there, the technology itself isn’t.
Then he outlined a high-level look at his approach to security and risk controls based on NIST. Of the plethora of NIST controls, he identified 140 that are can be used to measure the effectiveness of any security programme. Of those, 50 were selected as focus controls. From these controls, control effectiveness is measured and monitored on an ongoing basis. As part of IAM controls, active leaver metrics are an essential part of the joiner-mover-leaver measurement cluster. There are many risks to the organisation if these measures aren’t in place and working effectively. As we noted previously, one of the risks comes when people are moving around within an organisation. ‘You will find that people with 25 years in an organisation will still have access rights for a team that they left 10 years ago’, Andreas noted, ‘You may be lucky enough that, while the access is still there, the technology itself isn’t’. While this sounds amusing in the context of access rights outlasting the tech itself, it can be a big problem in the wider scheme of things. A lot of people take access rights with them, especially within IT. If someone is a UNIX administrator, then moves onto a cloud role, and then makes a shift to finance or treasury, this could be a huge problem. The access rights of such a person would be extensive, and the majority of those rights should not be available to that person anymore. This person likely has enough access that they have accrued throughout their tenure at the company to manipulate and change data without anyone else knowing. Maybe they are malicious, maybe they get phished, or maybe they get some malware. All these can open doors into the organisation. It’s not just that though, says Andreas, it’s also a legal and regulatory issue: ‘In the financial services world, for example, there is a principle that a researcher isn’t allowed to act with a trader. If this person is a trader who worked in research before and kept access or privileges, then the organisation is in violation of a serious financial services regulation. So, it’s not just a security risk, but an infringement of global banking law.’ On top of that, unnecessary access is just that – unnecessary. It runs against the principle of least privilege. Granting wide access as essential to fulfilling a job role is a necessary calculated risk. Unnecessary access means unnecessary risk. Another point rears its ugly head in the current COVID-19 working environment. There are plenty of companies that are well-equipped, whether it’s with work laptops that you can take home or remote session capabilities, so that’s not a huge problem. But a lot of companies have missed that. When it comes to the new working style, says Andreas, ‘the less control you have on the end-point, the more user-centric controls like active leaver measures, are important’. This is particularly notable when it comes to BYOD (bring your own device). All of a sudden, your well-protected environment has to be opened up to whatever the BYOD people have on their devices. Hopefully, you can give VPN access or remote sessions, which grant better levels of security. But the issue still stands. If a potential BYOD ‘super-user’ leaves the organisation and their accounts are not decommissioned in a reasonable timeframe, then the risks are potentially even greater than with on-premise devices. There is also a problem around account sharing. Measuring active leaver metrics is really important to giving visibility into these issues. Andreas highlighted extended absences and production lines as a familiar use case: ‘It just takes someone being on parental leave or sick leave for a few months. Their accounts should not be used. And all of a sudden it gets used. Why? Because people share accounts. Especially in a production environment. Often you may have a production line with one computer and one account, but ten people are using it. It shouldn’t be, but that is the reality.’
What is the audience?
So, who looks at these active leaver and joiner-mover-leaver measures? Andreas gives two key examples. First is the operational audience. These are the people responsible for actually decommissioning the accounts that need to be decommissioned, whether they are at the helpdesk, IT or HR. Second is the security and risk teams. If you have a control cluster that looks at identities and active leavers, risk and security teams can use these measures as part of a wider measure to answer questions like: ‘How effectively do we handle people leaving the company?’ It’s not just about who is looking at the metrics, but how they are presented. ‘The dashboard for risk people needs to have different information than one for ops people’, says Andreas, ‘If I’m a high-flyer looking at the big picture, coming up with new theories, looking at scenarios and simulations and all that stuff, then I don’t need the same information as the team looking for operational excellence’. The operations dashboard needs information about failures, alarms, and reaction. Whereas the more strategic overview needs to look at data in aggregate over time.
How are active leaver metrics used as part of an effective security programme?
That brings us nicely onto a great point Andreas made about aggregating across sources over time so that you can use metrics like active leavers to create a more effective security programme.
‘From a dashboard point of view you can see two problems here and they get fixed. But they are only symptoms, it’s not the root cause. In day-to-day operations you often fix symptoms, not causes. With the level above, you can see root causes over time and see why problems are happening and theorise about fixing them. That doesn’t happen overnight. It develops over a period of time, and you can only see it if you aggregate data over time.’
It is the aggregation over time that allows you to get that ‘level above’. That way, your security programme can go from a reactive approach – seeing issues and fixing them – to a proactive approach – looking for the reasons the issues occur and getting to the root cause. Andreas used an interesting ‘flat tyre’ analogy. If you get a flat tyre as you are driving down a road, you change the tyre and continue. You are not likely to talk to the people responsible for the road upkeep and tell them it needs more maintenance. But if you look at the ‘level above’, you can see the problem with the street itself over time.
The context of ‘point in time’ versus ‘over time’ makes a big difference when it comes to finding and fixing the root cause of problems.
On a normal street, you might see one or two flat tyres per month. But on this street, you have 20 or 30 every month. Those 20 or 30 individuals may just fix their tyres because they don’t see the data over time. Why is this road particularly dangerous to tyres? Once you answer this question, you are really getting to the root cause of the problem. Andreas added: ‘The context of ‘point in time’ versus ‘over time’ makes a big difference when it comes to finding and fixing the root cause of problems.’ It comes back to a state of reactive versus proactive. The reactive – ‘point in time’ – responses can be seen as the day-to-day necessities, but the proactive – ‘over time’ – strategy is necessary to improve the overall quality of the security programme. Bringing this back to active leaver metrics, you might see the odd discrepancy and fix it on the spot. But aggregating results over time allows you to look at your joiner-mover-leaver processes more widely and understand the root causes of any problems. So, you can fix those and improve the effectiveness of the security programme overall. ‘Again that’s the importance of aggregating data, not just looking at one little failure’, says Andreas.
How can Continuous Controls Monitoring help to improve active leaver challenges?
When it comes to active leavers, Continuous Controls Monitoring can be extremely valuable. By aggregating data from multiple sources, CCM provides valuable contextual information on basic active leaver metrics. ‘I have a whole team doing Continuous Monitoring of Controls,’ says Andreas. With this technology, when you are looking at movers and leavers, you get a more enriched view: ‘You can see that a specific function, location or platform has a particular problem’. Continuous Controls Monitoring allows you to overlay multiple metrics and measures to create the control clusters we spoke about earlier: ‘How many systems am I looking at? How many cases do I have of active leavers looking at stuff? You have more KPIs which you cluster together. As you cluster these things together, you can look at how many people have left the company where their account was not decommissioned, on which platforms, is there a separation of on-prem or off-prem, in the cloud?’ This provides so much valuable contextual insight. Andreas gave the example of an outsourced critical vendor – maybe they are failing on certain aspects of this metric, which is a particular problem because they work with your data but you don’t have direct security control over them. Then you can prioritise that risk and take steps to remediate. The value of Continuous Controls Monitoring for active leavers is in the aggregation of data across sources. That way you can look at trends over time, with the added value of contextual information – providing you with a much more informed view of the metric.

