
Why CAASM is the future of cyber asset management
CAASM – Cyber Asset Attack Surface Management – is a new category that takes your cyber asset management to the next level. The market is developing at a record pace, with increases of 138% in investment. Asset management is the backbone of any effective cybersecurity strategy. To address security issues effectively, you need to understand your attack surface. But that attack surface is constantly expanding, so our approach has to improve.
The problem with basic cyber asset management
Basic cyber asset management is becoming outdated. Gartner highlighted attack surface expansion as one of the top trends in cybersecurity for 2022. It said that organizations “must look beyond traditional approaches to… manage a wider set of security exposures.” With the onset of risks linked with things like hybrid working, IoT, cloud, and complex supply chains, attack surfaces are harder to understand.
Done manually, cyber asset management is a huge drain on resources. It takes a lot of time and effort to create inventories, and even more so to keep them consistently up-to-date. You’re reliant on agents or scanners, which can suffer from configuration issues, or may be failing to scan the whole environment.
In fact, our 2022 Security Leaders Peer Report found that security teams are spending 54% of their time on reporting. It all means that with current efforts, organizations struggle to gain complete visibility of their attack surface. Inventories and CMDBs are notoriously incomplete, so security teams inevitably struggle to take direct and precise steps to mitigate areas of weakness in the attack surface. “You can’t protect what you can’t see” rings true.
What is Cyber Asset Attack Surface Management?
One of the ways to overcome this challenge is with CAASM – a powerful technology that helps cybersecurity teams understand all the systems in their environment and discover security coverage gaps. It applies advanced data science and automation to create a more holistic view of an organization’s attack surface.
By combining data from various security sources such as vulnerability scanners and endpoint tools, as well as HR tools and any existing inventories, CAASM creates a complete cyber asset inventory. In turn, it compares the coverage of individual tools or controls to the full inventory to highlight gaps.
This can help to prioritize remediation and thus prevent security control failures – one of the biggest challenges in cybersecurity today. All this together means organizations get a consolidated view of their assets. Not just devices, but people, accounts, and more. This means you have total visibility of your attack surface, and can use it to improve the organization’s total security posture. It’s all about a proactive approach to security. An improved level of visibility can help reduce preventable breaches.
Understanding where your control gaps are allows you to plug those gaps and thus ensure that the controls you believe to be in place are actually working as intended. This is a major challenge – 82% of security leaders have been surprised by a security event, incident, or breach, that evaded a control that they thought was in place.
Your CAASM tool shows you a coverage gap. There is a group of devices that don’t have an endpoint tool running. The CAASM tool also highlights that they are part of a business-critical process. You can take quick steps to remediate – whether that’s reconfiguring the EDR or removing them from being externally facing. This helps to reduce the attack surface and improve security posture.
Does your business need CAASM?
To answer whether your business needs CAASM, there are a few questions you can ask yourself.
- Do you know all the assets on your network? If not, CAASM is an extremely effective way to gain that visibility. As soon as it is deployed, it can provide immediate value with an automated inventory of assets.
- Are you manually tracking and creating inventories? If yes, then the automation that CAASM brings can be a huge benefit to your security program. As mentioned above, manual reporting and data collection are a huge drain on resources, so automating that away is the next step.
- Do you have too many security tools? Our research found that enterprise security teams have an average of 76 tools. CAASM can help to get some much-needed visibility across the deployment of a large range of your tools, such as inventory, vulnerability, patching, and endpoint. All in a single pane of glass, giving you all the asset info you need in one place.
- Why is CAASM better than my SIEM and/or CMDB? Some organizations will be using a SIEM and/or CMDB to fulfill a similar function to CAASM. That might work in theory, but in practice, your SIEM can only tell you about assets that it knows about. It can’t tell you about assets it doesn’t cover. And if your CMDB isn’t fully accurate and up-to-date, your SIEM will only know about a fraction of your total estate.
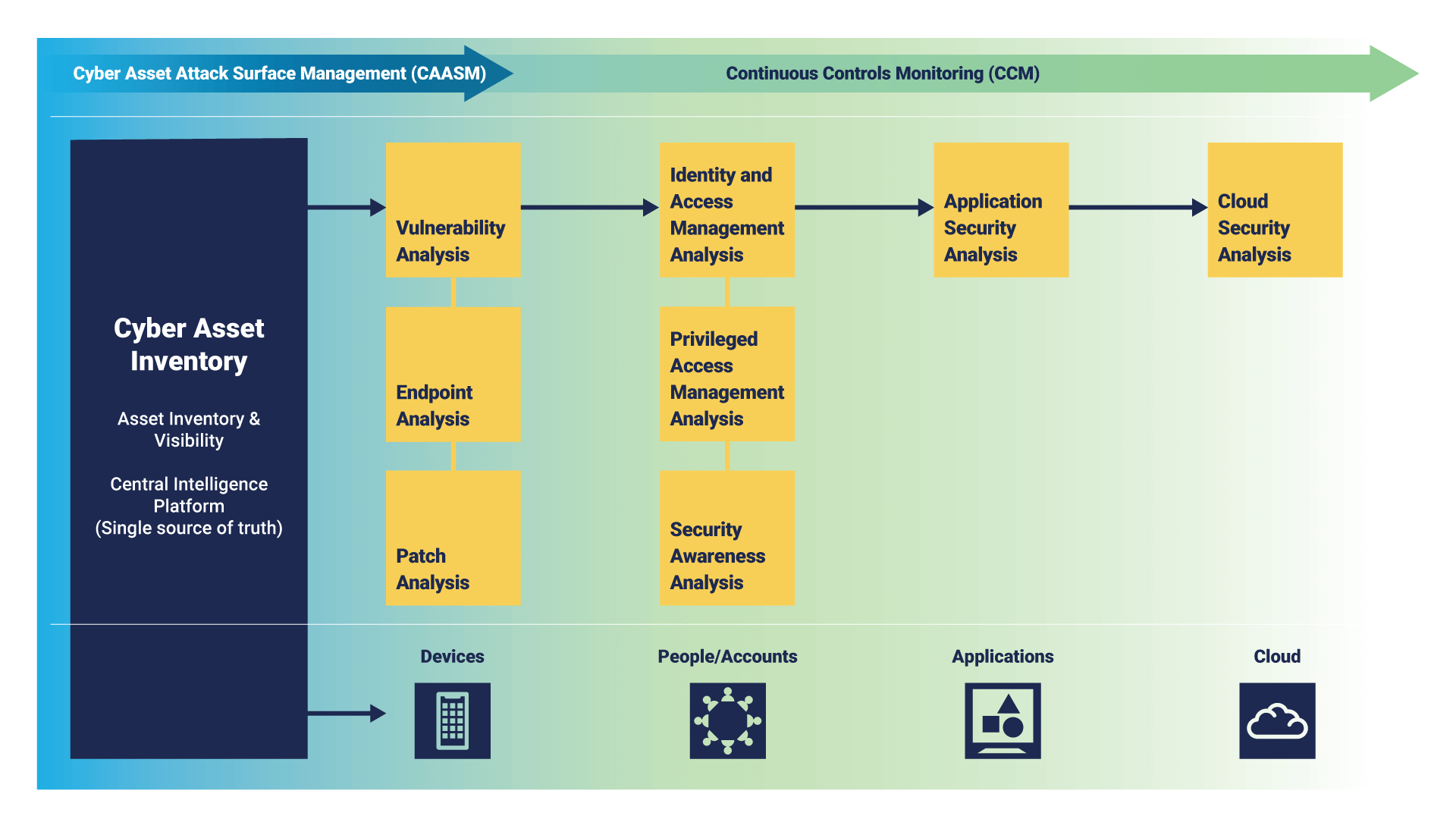
CAASM is the foundation for Continuous Controls Monitoring
While CAASM gives you improved visibility across your environment, it is only the first few steps towards a more comprehensive approach to proactive cybersecurity – Continuous Controls Monitoring. Our CAASM offering supports analysis of vulnerabilities, patching, and endpoint deployment, but with CCM you can gain this confidence across multiple security domains. From PAM and IDAM to user awareness, AppSec, and cloud.
The final word
CAASM is the essential next step in the evolution of cyber asset management technology. The uptake in users and investment, combined with the increasing challenges associated with expanding attack surfaces, shows that CAASM is an essential tool in the cybersecurity arsenal. If you’re interested in a tailored walkthrough of how CAASM or CCM can help your business, get in touch.


