
Why are security control failures one of the biggest challenges in cybersecurity?
Enterprise security teams need to recognise the risk posed by control failures and ensure they aren't caught out. A recent blog by Phil Venables, CISO of Google Cloud and security thought leader, highlighted the risk of security control failures. It builds on ideas he shared on Twitter several years ago, which incidentally inspired one of my first blog posts – Continuous Controls Monitoring 101. Phil's original post was somewhat ahead of its time, as last year Gartner’s Emerging Risks report ranked control failure as the number one emerging risk. The core of both articles still rings true: “Many incidents are not due to a lack of conception of controls but due to failures of expected controls.” This encapsulates the concept behind the Panaseer platform and the Continuous Controls Monitoring category we’ve been pioneering. Most security incidents happen not because of advanced threats or zero days, but because organisations haven’t properly implemented their security controls.
What is a security control?
According to NIST, a security control is “a safeguard or countermeasure prescribed for an information system or an organisation designed to protect the confidentiality, integrity, and availability of its information and to meet a set of defined security requirements.” Put simply, each security control is basically a statement of intent to protect your organisation from cybersecurity risks. For example, the first CIS Critical Security Control is: “Actively manage all enterprise assets.” (Well, a shortened version of it anyway). It’s broad and requires a lot of effort to execute properly. Perhaps a better example might be Safeguard 1.1 in that framework: “Establish and maintain a detailed enterprise asset inventory.” It can be common for people to conflate tools and controls, but they are not the same thing. They may be closely intertwined, but they are separate. For example, the above control, “Establish and maintain a detailed enterprise asset inventory”, describes the overall goal. You then need to use several tools to achieve that goal, such as a CMDB or Active Directory. But none of these tools is technically a control. 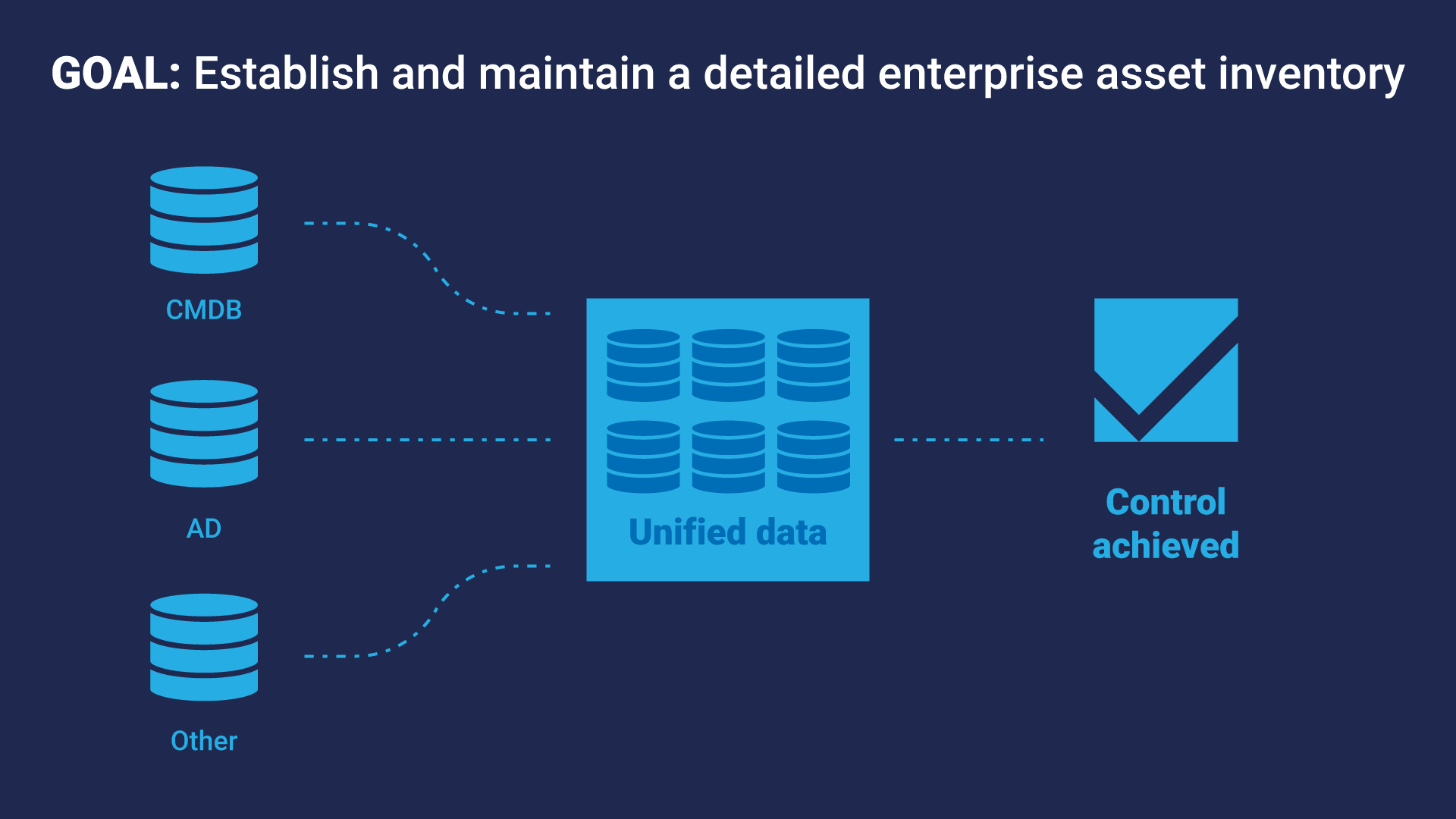 But some controls, such as safeguard 1.5: “Use a passive asset discovery tool”, explicitly require the use of a tool. Hence there may be some confusion.
But some controls, such as safeguard 1.5: “Use a passive asset discovery tool”, explicitly require the use of a tool. Hence there may be some confusion.
What is a security control failure?
A security control failure is when a security control is expected to be in place, but actually isn’t. Cyber and risk expert Andreas Wuchner highlights that control failure goes beyond the simple statement that a control isn’t working: “Security control failures happen when applied cybersecurity controls are flawed. They are either not functioning properly or are not covering everything they should. As a result, an organisation has a larger attack surface than they are aware of, and management makes decisions based on information that does not reflect reality.” There are plenty of reasons that may be the case: operational errors; incomplete deployment, implementation or migration; or “other faults/breakage”, as Phil puts it. Stuff breaks. Things go wrong. Especially when manual processes are the norm. There are many things that could be considered a security control failure.
- Your asset inventory is incomplete.
- An admin has too many privileges.
- An employee has left the company and their accounts are still active.
But realistically, there are tolerances. There are few enterprises with a 100% complete asset inventory. Privileged access management is no stroll in the park. And is it realistic to deactivate every account of every person that leaves a company within an hour? Of course not. Coverage controls like inventory, endpoint, or scanner coverage, are given an acceptable threshold. If your risk tolerance allows for 90% coverage, then anything below that would be considered a control failure. For other controls such as access, patch and vulnerability management, the tolerance would be set for a remediation threshold. Has this action been taken within 7/14/30 days? If not, that’s a control failure.
Why are security control failures important?
It comes back to Phil’s point: “the control or controls that would have stopped the attack (or otherwise detected/contained it) were thought to be present and operational but for some reason were actually not – just when they were most needed.” As mentioned above, Gartner’s Emerging Risks report ranked control failure as the number one emerging risk for senior risk executives. This aligns with research from our Security Leaders Peer Report which found that 82% of security leaders have been surprised by a security event, incident, or breach that evaded a control thought to be in place. On top of that, the report also found that on average, an event, incident or breach is the result of five control failures. It’s no wonder then, that 99% of security leaders believe it’s valuable to know all controls are fully deployed and operating within policy. To take a real-life example, the Irish Health Service Executive (HSE) published an independent post-incident review report that analysed the causes of its 2021 ransomware breach and gave recommendations for improving the organisation’s cybersecurity. One of its key findings was the “lack of cybersecurity controls”, listing a range of control failures including patch management and endpoint controls.
What can you do?
Phil’s blog recommends eight tips, including implementing Continuous Controls Monitoring. CCM provides automated cybersecurity metrics and continuous assurance that security controls are working as expected. But, as with anything in cybersecurity, it’s easier said than done. The first step requires advanced data science and automation to combine data from across all your security tools, creating a unified and complete asset inventory. Phil references this inventory triangulation as one of his 10 Fundamental (but really hard) Security Metrics. As he notes: “Other metrics [in this case, the measurement of controls effectiveness] rely on a set of inventories and rely on those being accurate. Inventories are rarely accurate unless they are actively used in a process that would apparently fail without such accuracy.” The other big step in reducing control failures is treating them the same way you would treat a security incident – reporting, escalation, review, analysis – whether or not the control failure actually resulted in a security incident. Organisations need to understand and recognise the risk posed by control failures. Andreas commented: “Undetected control failures are super dangerous. While risk dashboards show all green, the reality may be very different. Risk-based decisions are only as good as the quality of the underlying source data. Therefore, it is important to not only monitor the controls themselves and their thresholds, but also the coverage, the spin and the correctness and suitability of the control itself.” To improve overall security posture and proactively reduce cyber risk, organisations need to continuously monitor their security controls for consistent effectiveness. Book a demo to find out how Panaseer's Continuous Controls Monitoring platform reduces the risk of control failures.


