
Why security teams need to measure cloud misconfigurations
“Speed over security shouldn’t be a question.” But with cloud configuration, that is often the case. This leads to an important risk that needs to be measured and understood: cloud misconfigurations. For this article, I caught up with “friend of the show” Andreas Wuchner. Andreas is a renowned cyber and risk expert with over 20 years of experience, having held CISO roles across multiple industries.
Why are organizations moving to the cloud?
Cloud computing provides affordable network storage and quick-to-deploy computing resources (servers, storage, apps, and more). While someone could easily write a book on this question, I asked Andreas to briefly summarise why organizations are moving to the cloud. “There is pressure to be fast in the digital world.
At the same time, the cost of IT is increasing. In the enterprise, IT is seen as an enormous, slow-moving machine. If you want to achieve anything, there is so much formality that it takes forever. What does it cost to have a server and instance running internally? With a cloud service provider, you just need a credit card and some developers.”
Additionally, the COVID factor can’t be ignored. The shift to cloud and change in the way people work started before the pandemic, but it skyrocketed in 2020. Working from home is part of it, but many companies now require employees to have access to all work functionality from any place at any time.
That means increased use of applications, rapid scaling, and shifting the location of data centers. This last challenge has been put into perspective by the invasion of Ukraine. Cloud can provide enormous flexibility when organizations want to minimize the impact on their operations from crisis events. It’s cheaper, faster, and easier. So, what’s not to like? The shift to the cloud has its challenges for many organizations. One of the big factors is the common occurrence of cloud misconfiguration.
What is cloud misconfiguration?
As we said at the top: “Speed over security shouldn’t be a question.” But unfortunately, it is. When you spin up a cloud instance, it is easier and sometimes quicker to ignore much of the available security functionality.
“There is a certain complexity that puts people off secure configuration,” says Andreas. “The big CSPs [cloud service providers] – AWS, Google, Azure – give a lot of security options and tools. If you configure those correctly, it is a safer place to do business than on-premises. It can scale more effectively and bring a range of possibilities. The question is: are you using those security options?”
“There are many security features that people will probably want to say yes to, but then they are shown a page asking for a whole bunch of information they don’t know – credentials, ports, etc – and then they just choose not to use that security feature. The easier things are, the more relaxed people will be. You can spin up a container in two minutes, with a few clicks and a credit card number.”
“It’s rarely malicious. People don’t mean to do it. However, cloud customers and users are not always IT or security professionals. Security isn’t always top of their to-do list.” According to Andreas, this type of behavior is more common in organizations with less mature security programs, or in those facing less stringent regulation. “In a major bank, people will get grilled and fired for doing things like that,” he explains.
Common examples of cloud misconfigurations
Here are a few common examples of cloud misconfigurations that Panaseer users measure:
- Unrestricted inbound ports
- Unrestricted outbound ports
- Disabled monitoring and logging
- ICMP (internet control message protocol) left open
- Unlimited access to non-HTTPS/HTTP ports
- Overly permissive access to virtual machines, containers, and hosts
- Enabling too many cloud access permissions
Beyond these, Andreas highlights more basic metrics to measure for cloud assets: “Identity and access management. Complex passwords. Patching. Logging. Encryption. Endpoint. Everything that you have on the machine under your desk, you also have to look at in the cloud.”
Why do we need to measure cloud misconfiguration?
There are numerous studies that show the risks associated with cloud misconfiguration:
- A research survey of over 300 CISOs found that cloud misconfiguration was the top concern associated with cloud production environments.
- The Independent reported that 90% of organizations are vulnerable to security breaches due to cloud misconfigurations.
- According to research by Trend Micro, cloud misconfigurations are the top cloud security risk as 65%-70% of all cloud security challenges arise from cloud misconfigurations.
- Gartner predicts that by 2025, 99% of cloud breaches will be attributed to human error.
As cloud misconfiguration is so common, security teams need to understand when and where it is happening. This means they are a crucial part of any mature cybersecurity measurement program.
How do we measure cloud misconfiguration?
“In theory, it is quite simple,” says Andreas. “In a cloud system, you have an interface that provides reports about the compliance of each instance against whatever standard you have set. And you can get certain tools that access this interface and provide great insight.” But when you have a very complex environment, with multiple cloud providers, a mixture of private and public cloud environments, and an on-premises environment, it can be a challenge to get an accurate understanding of your security posture.
The CCM (Continuous Controls Monitoring) approach is to pull data from all these environments to give a single view of misconfigurations across all cloud accounts. Data from multiple cloud sources, including cloud security posture management tools (CSPMs), is combined with additional data sources and enhanced with business context to give a complete picture of key risk areas.
This dashboard from our platform, for example, shows which CSPs have the most misconfigurations and provides a visualization showing which specific areas (along the x-axis) hold the most risk broken down by CSP (y-axis). That way users can prioritise remediation in specific areas that pose the biggest risk.
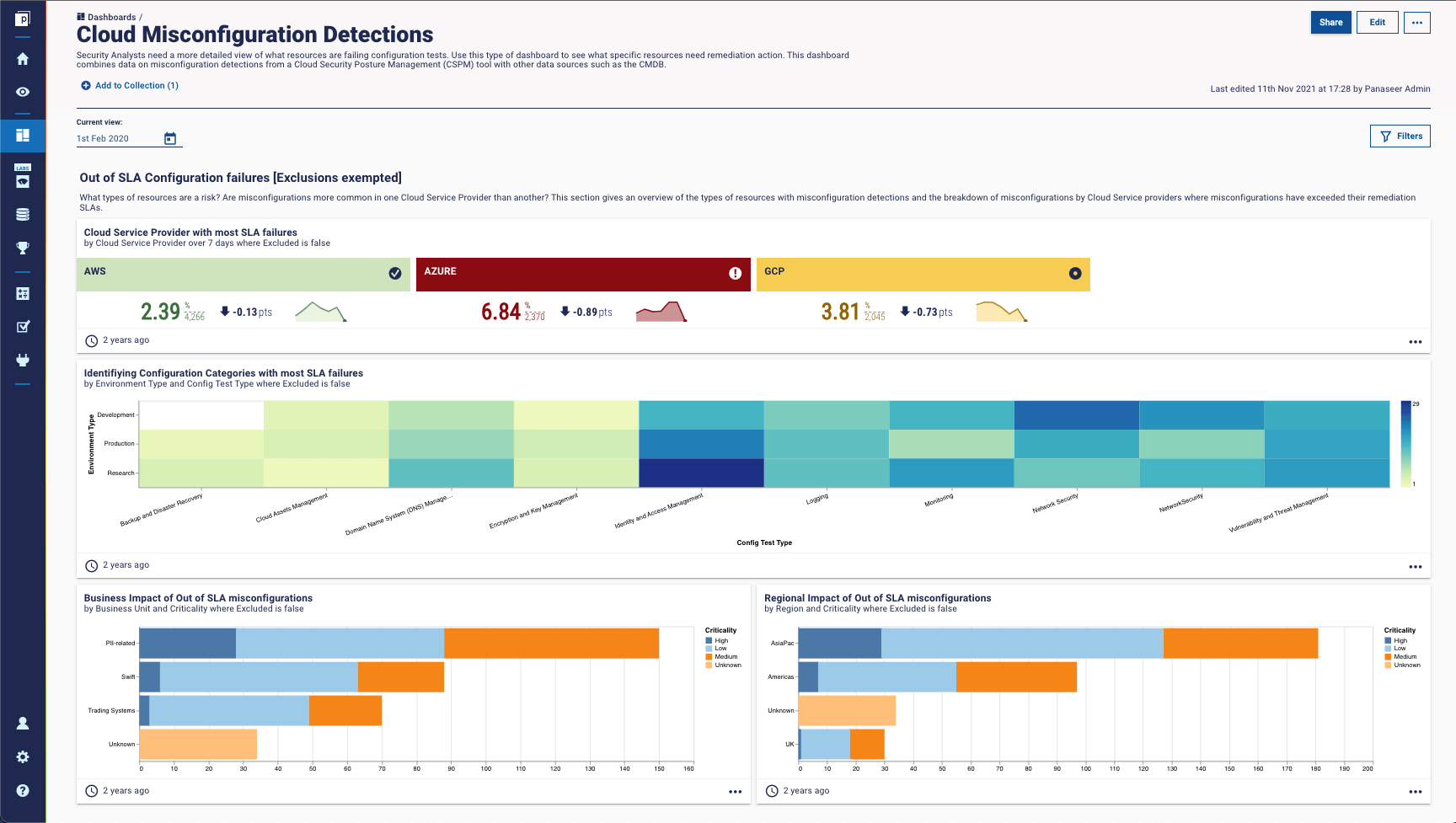
This is a great value add to a holistic cyber measurement program, as it can help to provide a more complete view of security posture across hybrid environments. If you want to see how it works on our platform, get in touch.
The final word
Cloud is more important than ever. And that means cloud security is more important than ever. While there are great options for secure cloud configuration, some users may overlook them in favor of ease and speed. That’s where cloud misconfigurations are born. These are an important cyber risk that security teams need to understand and rectify.

