
How do you use cybersecurity frameworks to improve security measurement?
In this blog we’ll explore the benefits of security frameworks, the differences between framework organizations, and how they’re used in the Panaseer platform.
Cybersecurity is a critical risk for all organizations, however, research shows that most breaches are preventable with the right controls. In fact, our 2023 Security Leaders Peer Report found that 79% of organizations have been caught out by an attack that existing controls should have prevented. To improve your cybersecurity posture and reduce the risk of a breach, you can follow the guidance on security controls that's available from recognized security framework organizations.
What is a security framework?
A security framework is a set of guidelines or best practices designed to help organizations manage their cyber risk. With a framework in place, it becomes much easier to manage risk, reduce vulnerabilities, and focus your cybersecurity efforts.
What are the differences between security frameworks?
Security frameworks come with different degrees of complexity and scale. While many of them share common foundations and approaches, they're not interchangeable, so it’s important to know which one (or more than one) is best suited for your organization.
Choosing the most appropriate security framework can be influenced by your industry and the standards and regulations your organization is subject to. Indeed, organizations working internationally might need to implement more than one security framework.
There is no inaccurate security framework, the only bad choice would be not using any of them. It’s also important to note that framework organizations don’t provide advice on how their guidance and standards should be implemented.
Our platform enables you to measure your security posture against three of the most important security frameworks.
CIS: The Center for Internet Security Critical Security Controls
The CIS CSC is a list of technical security and operational controls that can be applied to any environment. It focuses on reducing cyber risk and increasing resilience by using automated controls. CIS uses benchmarks based on common standards like HIPAA or NIST.
Who is it for?
CIS is relevant for all organizations. It’s structured in self-assessed categories called Implementation Groups (IGs), which help organizations classify themselves and focus their security resources by CIS Controls best practices. The IG categories are:
- IG1: This is for small to medium-sized organizations with limited IT and cybersecurity knowledge.
- IG2: Companies in this category operate on a medium-scale and store sensitive information regarding clients and the organization. They usually have a dedicated cybersecurity team.
- IG3: This IG is the most complex to implement and requires cybersecurity experts that specialize in different areas.
Pros: Ideal for organizations that want to mature their security practices over time. CIS offers operational simplicity and an emphasis on protection and mitigation.
Cons: Since CIS standards apply widely to organizations regardless of industry or country of operation, its guidelines are not comprehensive as they are less concerned about regulation and more focused on defense and mitigation.
NIST: The US National Institute of Standards and Technology
NIST provides a flexible framework that any organization can use for creating and maintaining an information security program. It was designed to protect America’s critical infrastructure (e.g., dams, power plants) from cyberattacks. NIST has influenced other standards and guidance, such as NCSC and MCSS.
Who is it for? NIST cybersecurity framework (CSF) is a subset of NIST 800-53 and shares controls found in ISO 27002, but is not inclusive of both. This makes the NIST CSF a common choice for smaller companies that need a set of "industry-recognized secure practices" to align with, whereas ISO 27002 and NIST 800-53 are better for larger companies or those that have unique compliance requirements.
Focus: Comprehensive and personalized security weakness identification. NIST outlines five functions that help organizations spot and respond to cybersecurity events in a timely manner:
- Identify: This function helps organizations have full visibility into their digital and physical assets and to understand their current risk exposure.
- Protect: This is mostly a proactive phase of an organization’s cybersecurity as it supports the ability to limit or contain the impact of a potential cybersecurity event.
- Detect: This function supports an organization’s ability to discover any occurrences of a cybersecurity event in a timely fashion.
- Respond: If a breach is detected, this function helps organizations apply appropriate procedures — understanding the breach, fixing the vulnerability, and proceeding with the recovery.
- Recover: This identifies appropriate activities to restore any services that were weakened due to a cybersecurity incident and helps maintain a plan for resilience.
Pros: NIST offers a complete, flexible, and customizable risk-based approach to secure almost any organization. It is also approved by the US government.
Cons: Small or medium-sized organizations may find this security framework too resource-intensive to keep up with. It often requires expert guidance for implementation.
MAS: The Monetary Authority of Singapore Technology Risk Management
While CIS and NIST are recommended security frameworks that any business can adhere to and reference, MAS is a legally binding requirement for the financial sector in Singapore.
Who is it for? Financial institutions with operations in Singapore. But this high-level requirement is also useful as a standard for other regions.
Focus: Establishing robust governance in technology risk management. Even if you’re not looking at being certified compliant, it's still important to ensure a mature cybersecurity program is in place to address the highest areas of risk of your business. The more controls you meet, the more prepared your organization will be to face and respond to digital threats.
What does a security framework look like?
Cybersecurity frameworks generally use a similar structure. Let’s take CIS as an example.
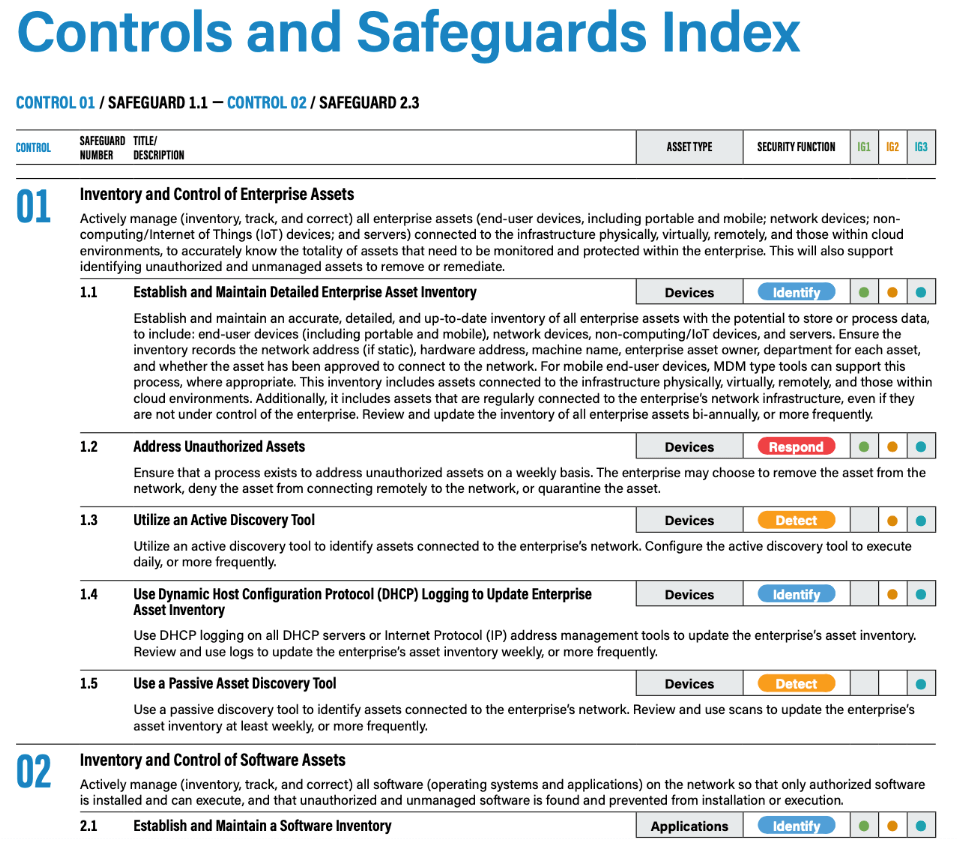
The document is divided into Controls. In CIS version 8 we can find 18 different Controls, a set of recommended actions that aim to protect organizations from cyber-attacks. Each Control comes with:
- a description of why its implementation is critical;
- a table of the specific actions (Safeguards) that organizations should take to implement the control;
- procedures and tools that enable implementation and automation;
- the type of asset the Safeguard is protecting (applications, data, devices, network, users);
- the security function the Safeguard is covering.
How are security frameworks implemented in the Panaseer platform?
The Panaseer platform automates security metrics and measurement so organizations can get a true picture of their security posture, as well as actionable insights on where to prioritize resources. Before showing how security frameworks are presented in our platform, it’s important to make a distinction between Control Checks and Metrics:
- Control Check: A codified test of a security standard that customers can use in our platform. It’s applied to an individual record and its output can only be pass, fail or not applicable.
- Metric: Security frameworks are best practices that organizations should follow to manage cybersecurity risk, but they don’t come with full instructions on how to apply them. Our platform overcomes this problem by providing you with list of metrics that answer key questions about how well your organization is managing security risks. A Metric is a mathematical operation, usually with the purpose of summarising by counting, summing etc. that will apply the Control Check and give a numerical output.
To make aligning to security frameworks easier for you, we link all our metrics and Control Checks to the corresponding security framework policies and procedures.
For example, you can find all the security frameworks and the Control Checks that link to them under the Control Check Catalogue section.
Each security framework is structured just as in the original documentation. Continuing with our previous example on CIS, the platform screenshot shows the security framework is divided in Controls and Safeguards:
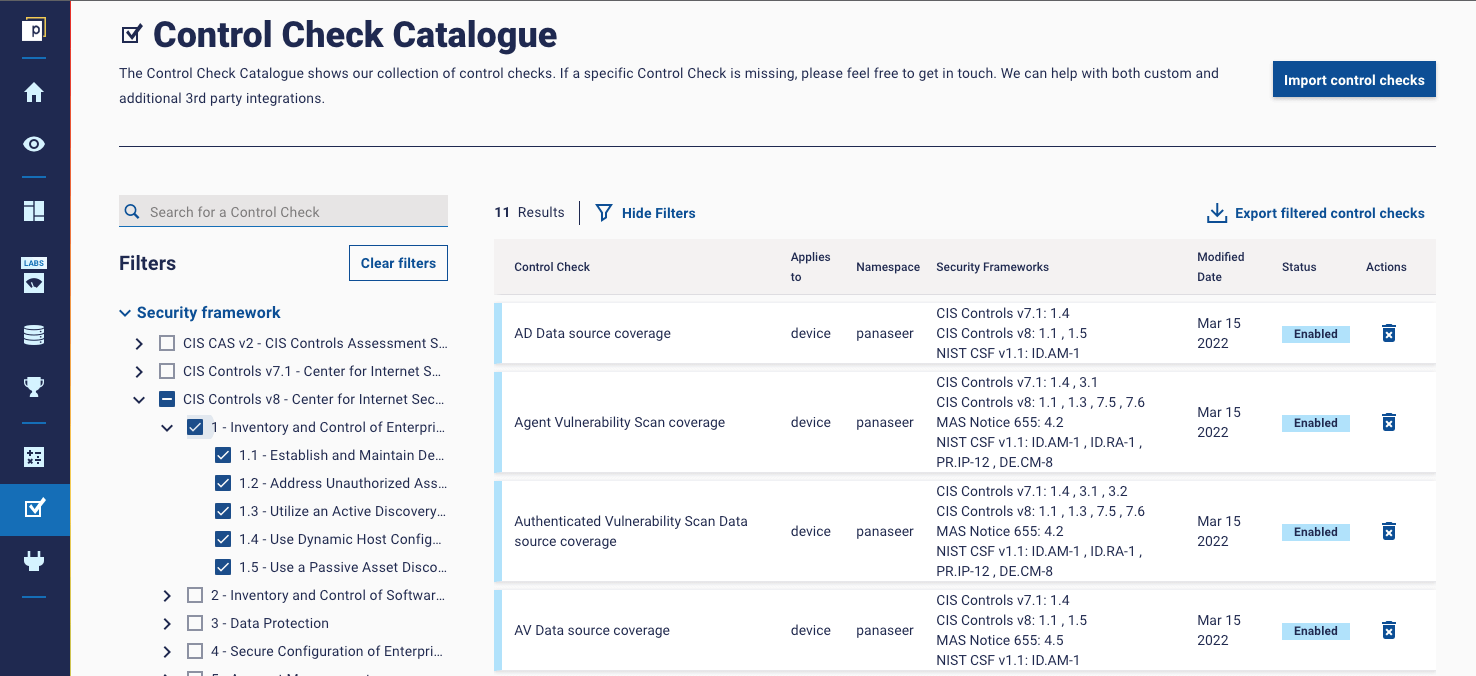
When a specific Control or Safeguard is selected, the corresponding Control Checks will appear on the right-hand side. This will help organizations easily choose and implement the required measures to secure their business and comply with the security framework guidelines.
The final word
Implementation of a security framework is essential to mitigate risk and ensure that organizations have a solid foundation for their security posture.
The Panaseer platform’s automated metrics and Control Checks make it simple for customers to view their security posture aligned to the framework of their choice.


