
How can CAASM support CIS compliance?
Discover how our CAASM platform helps organizations align their security metrics and measurement to several Critical Security Controls to help with CIS compliance.
CAASM – Cyber Asset Attack Surface Management – is a new technology that helps organizations understand their attack surface with a trusted cyber asset inventory. This can be hugely valuable for security teams when it comes to supporting compliance with various frameworks, such as CIS.
The Center for Internet Security (CIS) is a community-driven non-profit organization providing top-tier thought leadership in the field of cybersecurity, particularly cybersecurity controls with its Critical Security Controls (CSC).
Panaseer has partnered with CIS to support the development of the Controls Assessment Specification, which provides guidance on the security metrics that organizations should measure to assess their compliance with v8 of the CSC. Our CAASM platform offers automated security measurement for asset inventory, vulnerability management, and patch management, which supports compliance with a number of the CSC controls:
In this blog, we discuss how CAASM helps with each of these controls.
Control 01: Inventory and Control of Enterprise Assets
The first critical security control covers the management of enterprise assets. That means tracking and correcting inventories of end-user devices (such as laptops), network devices, IoT, and servers, whether they are connected to the infrastructure physically, virtually, remotely, or within cloud environments.
Organizations need an accurate understanding of enterprise assets that need to be monitored and protected, as well as identifying unmanaged assets to remove or remediate. Control 01 is part of Implementation Group 1, therefore one of the ‘essentials’ for good cyber hygiene, as we discussed with the Senior Director for CIS Critical Security Controls, Phyllis Lee, in our Metric of the Month article on security controls frameworks.
Interestingly, Phyllis mentioned that people used to use the word ‘basic’ about this control. But ‘basic’ implies ‘easy’, which is far from the truth. One of the main ways our CAASM platform supports Control 01 lies in automatically creating trustworthy cyber asset inventories. By pulling data from a variety of security tools that each have some asset information, you gain a centralized cyber asset inventory that holds data about every asset in the enterprise.
Crucially, this inventory is continuously updating and is the basis for measuring the controls in place on all these assets, so you can understand enterprise-wide control coverage and efficacy.
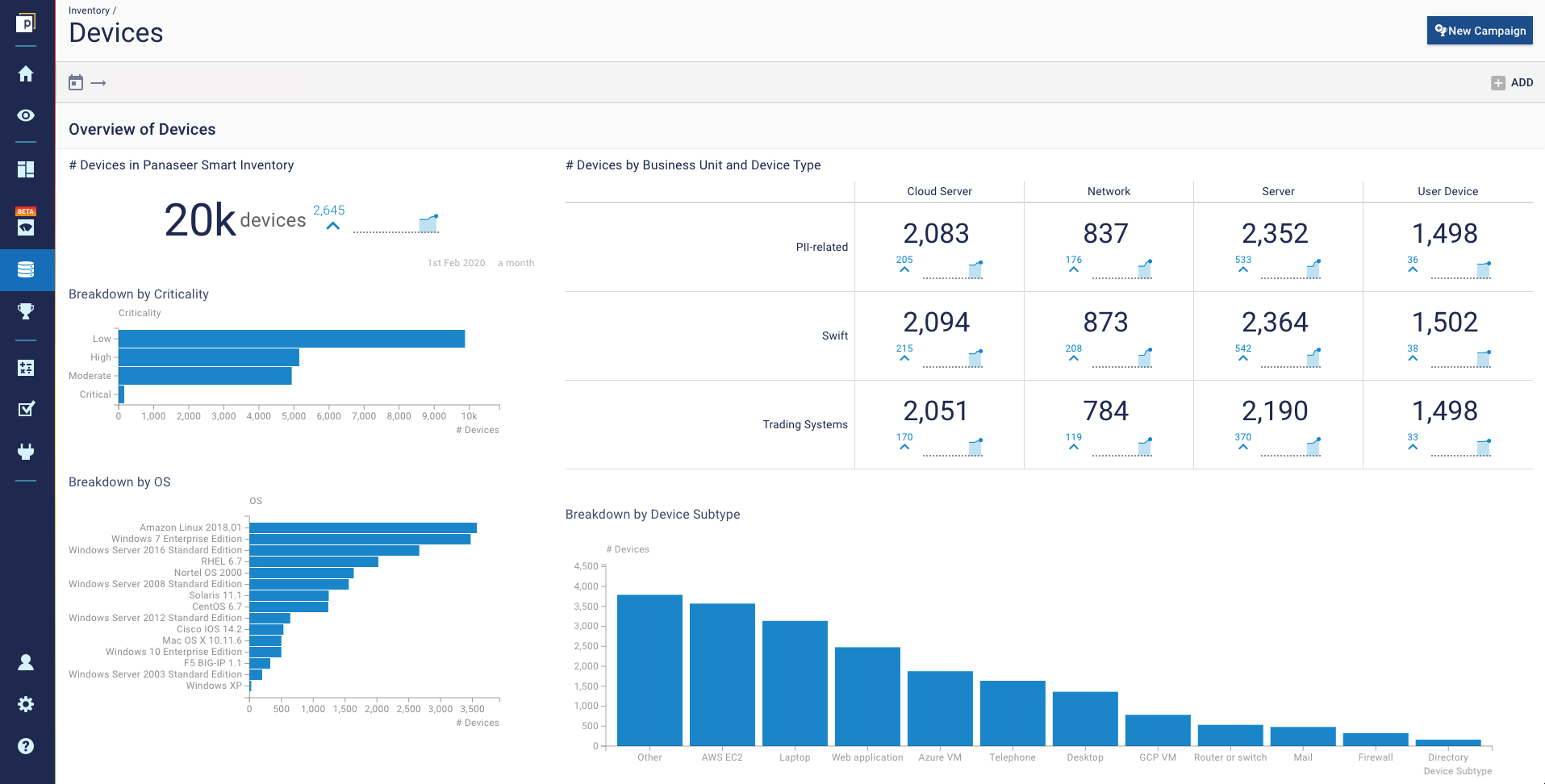
This dashboard provides a typical inventory of devices, with breakdowns such as criticality, operating system, device type, and business process. Indeed, Panaseer can be used like a passive asset discovery tool.
With no probes or agents, our CAASM platform relies on triangulating asset data from multiple sources. That could be current asset inventories, such as a CMDB, Active Directory, or even spreadsheets, but it also utilizes the data from tools like vulnerability scanners, endpoint protection tools, and even HR tools. Where a scanning discovery tool may miss ephemeral assets that spin up and down in between scans, a tool like Panaseer can keep track of those more effectively by triangulating data from multiple sources.
Control 02: Inventory and Control of Software Assets
Just like enterprise assets, organizations also need to actively manage software assets, such as applications and operating systems. This is to ensure only authorized software can be installed or operated on the network, and that unauthorized software can be identified and removed.
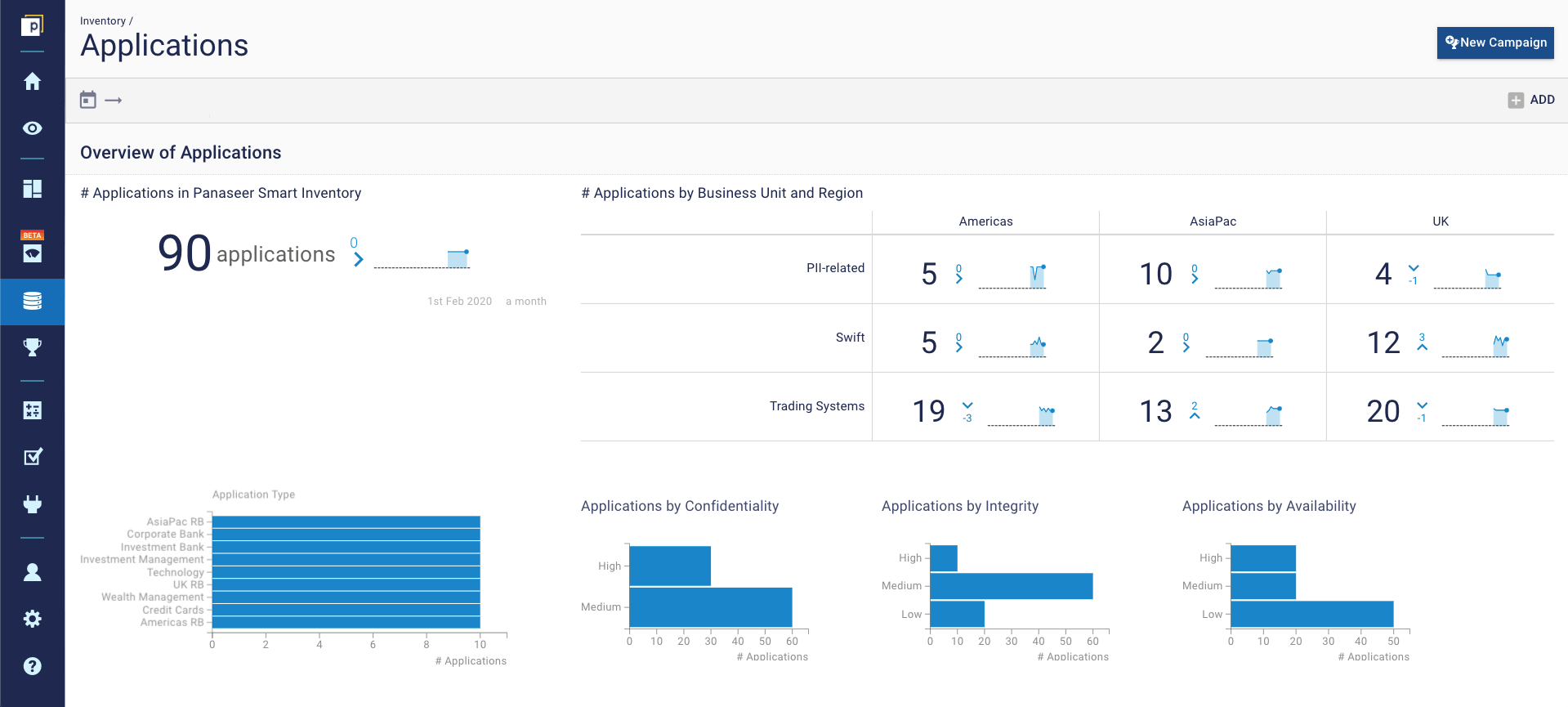
This dashboard shows not just an inventory of applications, but some of the business context around them. This business context is the crucial element that our CAASM platform brings to inventories. Because the platform ingests data from a variety of tools, including those outside security, you can see contextual data for enterprise and software assets. For example, you can see applications by geography, business unit, business process, confidentiality, and more. The context in itself is valuable, but it really helps when it comes to remediation, because you can prioritize based on these factors. If two assets need attention, but one is part of a business-critical payments process, that one is the priority.
Control 07: Continuous Vulnerability Management
Vulnerability management is crucial to the success of any cybersecurity program. Enterprise security teams must deal with an immense amount of vulnerable data, which they need to continuously assess and track on all assets in the organization. That way they can better remediate vulnerabilities.
CAASM provides customizable and automated data queries which enable you to identify security control gaps and prioritize remediation campaigns, so you can focus on protecting your business rather than wasting time on manual reporting. Here is an example CAASM dashboard that can help support your continuous vulnerability management efforts and CIS compliance.
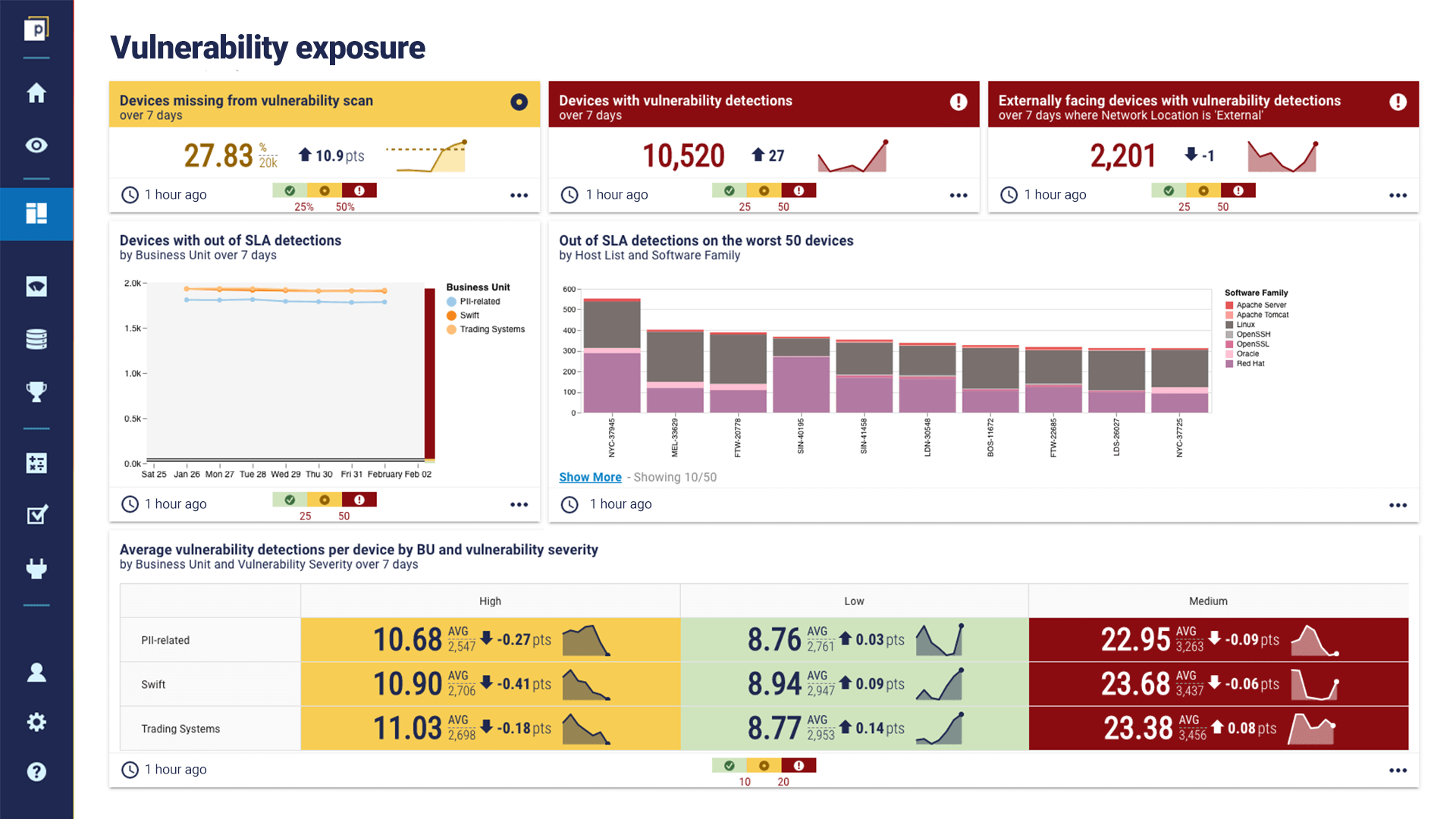
The dashboard above highlights a few of the metrics available in the CAASM platform, including:
- Devices missing from a vulnerability scan.
- Devices with vulnerability detections. Plus which of these are externally facing or end of life, making them particularly risky.
- Devices with detections outside of an established Service Level Agreement (SLA). In this case, split by business process, which enables improved remediation based on that context.
- Out of SLA detections on the worst 50 devices. This can help to identify some of the vulnerabilities that are more pervasive in the environment. Targeting these using vulnerability outlier analysis can also be particularly powerful for remediation.
- Average vulnerability detections, split by business unit and severity.
Recently, many of our customers utilized these kind of metrics to monitor and remediate against Log4Shell, one of the biggest vulnerability threats in recent times.
Control 10: Malware Defenses
Organizations need to prevent or control the installation, spread, and execution of malware on enterprise assets. One of the key capabilities of our CAASM platform includes the coverage of endpoint tools, such as anti-malware, across the cyber asset attack surface. By highlighting gaps in this coverage, users can easily see where to remediate to become not just compliant, but better protected.
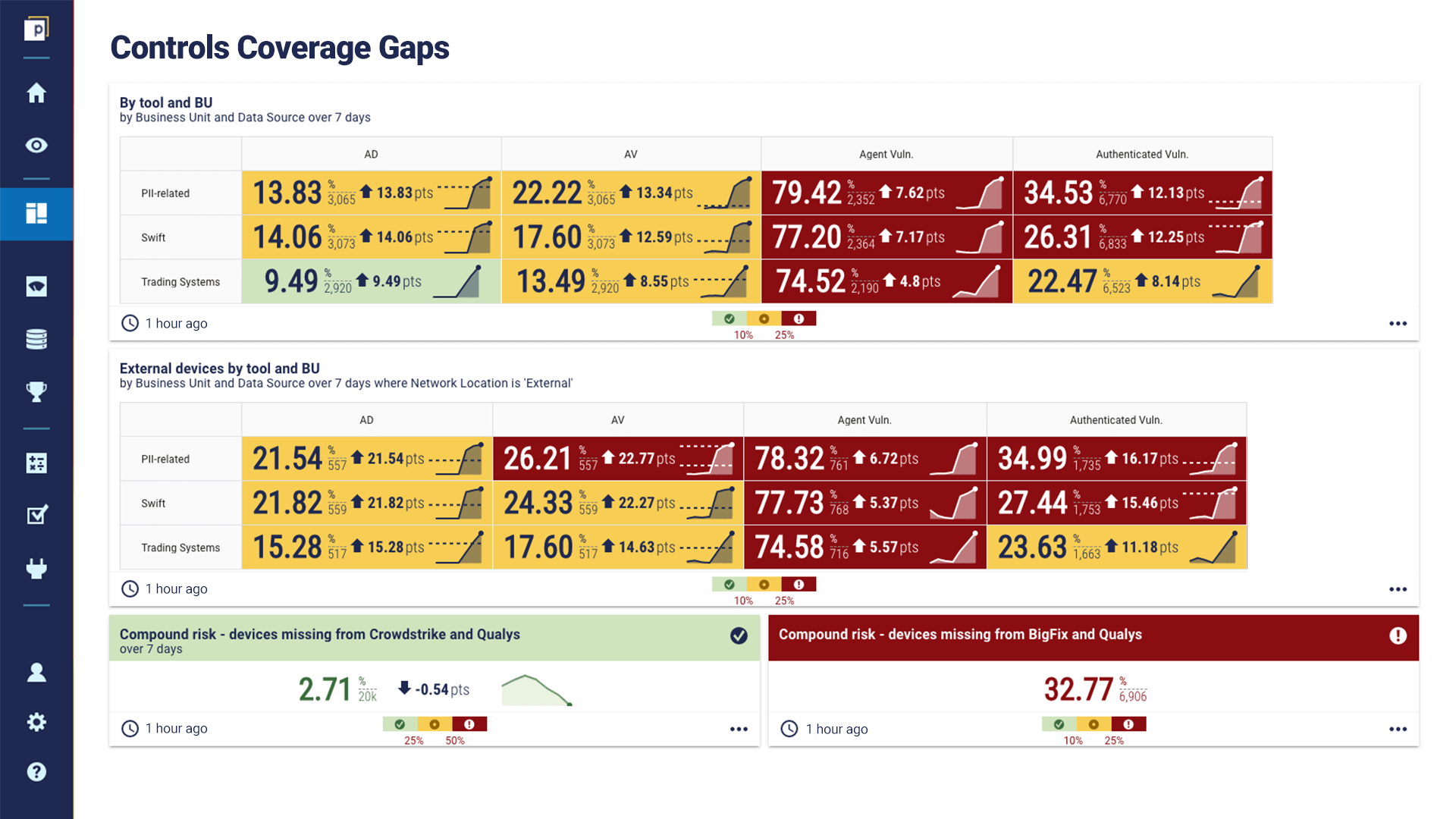
This dashboard gives some examples of controls coverage gaps for anti-malware tools like antivirus. The view is split by business unit, so you can see where the gaps are in specific areas of the organization, which helps to prioritize remediation. Another notable metric provided here is compound risk.
By combining data from multiple sources, the CAASM platform lets you know devices missing from two key sources. While it isn’t ideal, it may be tolerable to have a small percentage of devices without one level of protection (such as Qualys), but it poses a much larger risk if they are missing two levels (such as Qualys and Crowdstrike). Again, a good place to start remediation.
The final word
As we have seen, CAASM is a hugely valuable technology for assessing several of the Critical Security Controls and CIS compliance. In particular, the advantages of an automated inventory are hugely beneficial for Controls 01 and 02, especially given the difficulty of consistently updating any inventory manually.
As CAASM aligns vulnerability and malware data sources to this inventory, you also benefit from a greater understanding of those areas of security, as well as compliance with Controls 07 and 10. CAASM is the foundation of a high-quality security metrics and measurement program. It is the first step towards establishing a full Continuous Controls Monitoring (CCM) platform. Automated inventories, vulnerabilities, patching, and endpoint protection are only the tip of the iceberg when it comes to a complete, world-class security metrics and measurement program, which is what you get with CCM. If you want to find out more about CAASM or CCM, get in touch or book a demo.


