
What does the Irish health service ransomware attack tell us about security controls?
The major Irish health service cyber-attack in 2021 highlights the importance of having cybersecurity controls in place, specifically those that mitigate the threat of ransomware. The Conti ransomware attack on the Irish Health Service Executive (HSE) was one of many such cyber-attacks to grab headlines last year.
The ransomware led to 80% encryption on the HSE’s IT environment, meaning short-term disruption to communication systems and crucial medical services, and a long-term recovery effort. In December, the HSE published an independent post-incident review report prepared by PwC that analyzed the causes of the breach and gave recommendations for improving the organization's cybersecurity.
The report highlighted the importance of ensuring fundamental security controls are in place, so we are going to explore the findings for lessons that can be learned by many organizations and the wider security community. We’ll focus on security controls, especially controls that help to mitigate ransomware. This attack was successful due to a lack of controls rather than the attackers doing anything particularly sophisticated.
It's worth noting that the report highlights the willingness of HSE staff members, and other third parties drafted in, to support the efforts needed to overcome the challenges posed by the ransomware attack, whether from a technological or healthcare standpoint.
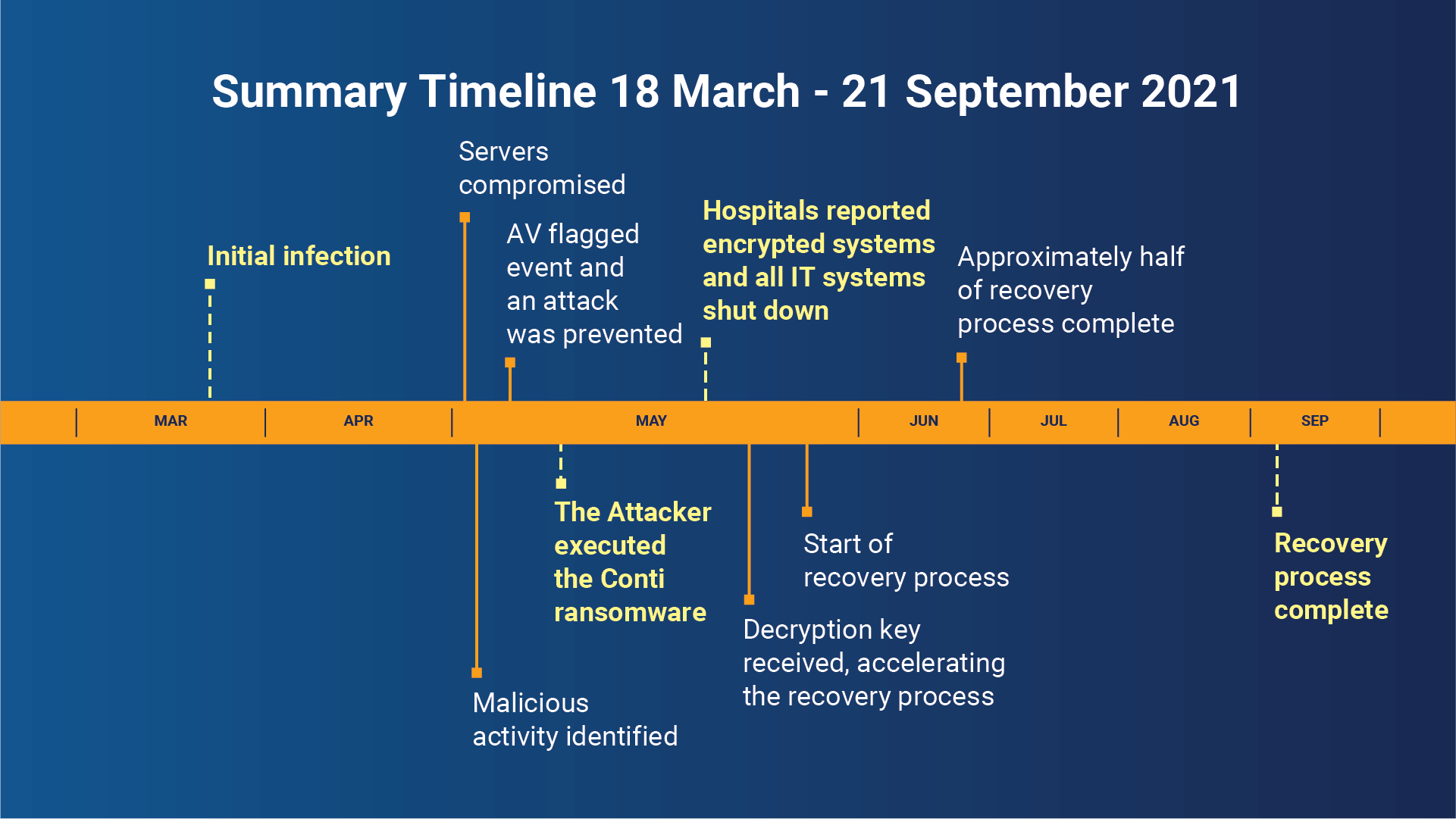
What happened during the HSE ransomware attack?
The attack originated on 18 March 2021 when a user opened a malicious Excel file attached to a phishing email sent two days previously. The attacker was able to gain unauthorized access to the HSE’s IT environment and spent around eight weeks moving laterally across the organization and operating inside until the Conti ransomware was activated on 14 May, causing considerable disruption.
The attackers took advantage of a “significant number” of privileged access accounts, as well as 180 systems across various domains and organizations, allowing them to exfiltrate data.
According to the PwC report: “The aim of the attacker was to disrupt health services and IT systems, steal data, and demand a ransom for the non-publication of stolen data and provision of a tool to restore access to data they had encrypted.”
The HSE’s processes led to the decision to switch off all IT systems to try to contain and assess the impact of the attack. It meant that healthcare professionals lost access to IT systems that are essential to caring for patients – patient information, clinical care, and laboratory systems. Similarly, regular communication channels such as email and networked phone lines were lost, forcing HSE to revert to pen and paper or fax machines.
Healthcare services across Ireland were disrupted, “with real and immediate consequences for the thousands of people who require health services every day,” as the report notes.
Lack of security controls
Control failure, whether failures in expected controls, gaps in controls, or incorrectly deployed controls, is one of the biggest challenges in cybersecurity today. Most breaches are not due to a new zero-day attack, but failures of fundamental controls.
In fact, our own research found that 82% of security leaders have been surprised by a security event, incident, or breach, when they believed they had an appropriate control in place.
Among the strategic recommendations and findings, the PwC report recommends the HSE must improve the maturity of its cybersecurity program because of “the lack of cybersecurity controls in place at the time of the incident.”
Like many organizations, the HSE’s security policy was extremely outdated, having been written in 2013 and updated a year later. As the report suggests, it therefore “does not reflect the controls required to manage cyber risk in 2021.”
PwC highlighted several cybersecurity controls as lacking, including patch management and endpoint controls. In particular, the HSE relied on a single antivirus tool that was not monitored or maintained effectively. It was poorly deployed and configured, meaning it couldn’t block malicious activity within the server estate.
To top it off, the initial entry workstation hadn’t had an antivirus update for a year. This highlights the need for organizations to not only establish cybersecurity controls but to monitor them continuously. That way, gaps like these can be found and fixed. Indeed, the report found: “The HSE did not have a centralized cybersecurity function that managed cybersecurity risk and controls. There was no centralized team to set the vision and tone for security and perform critical security functions, most notably security monitoring and cybersecurity control assurance activities.”
Continuous Controls Monitoring (CCM) is a technology designed exactly for such a purpose. It utilizes data from tools across the IT estate to provide automated security metrics and measurement, focusing on the continuous assurance of controls.
Define and defend thresholds
One of the main challenges the HSE faced was a lack of formalized thresholds or service level agreements (SLAs). SLAs are essential to any effective security program because they establish the minimum requirements for each control, or for IT services more generally. In the case of an endpoint control, some example SLAs or acceptable thresholds might be:
- An endpoint tool must be present on every asset.
- Tool version updates must be rolled out within seven days.
The report recommends that the HSE define the minimum acceptable level for security controls and establish a program to monitor and enforce compliance to those SLAs both for the HSE itself and any organization connecting to its network. Establishing SLAs is a crucial part of any effective security control and monitoring them is important to any quality security program.
The Panaseer platform uses Control Checks to help overcome this challenge. It allows users to define thresholds in the platform and prove to any given stakeholder exactly where security control SLAs are not met. This helps them defend their program and hold other stakeholders accountable.
Monitoring ransomware security controls
Alongside poor security controls at a strategic level, the HSE lacked any specific controls aimed at preventing ransomware attacks. There were “high-risk gaps” relating to 25 out of the 28 controls that comprise PwC’s ransomware readiness framework.
For example: there were “very high” risks around automated and continuous vulnerability scanning, multi-factor authentication, and endpoint detection and response tooling. The HSE board was made aware of security control gaps leaving them susceptible to ransomware as early as November 2020, but had failed to take the necessary action to secure the organization.
To mitigate the increasing risk from ransomware attacks, PwC recommended that the HSE should perform a cybersecurity assessment specifically around ransomware. This helps to provide assurance in the areas where the organization is protected and highlights areas that require investment or improvement.
A preventable attack
Analysis of the report suggests the HSE cyber-attack would have been preventable with sufficient controls in place to counter ransomware.
The HSE’s outdated policies and controls were overcome by an attack that was not particularly sophisticated. This attack and subsequent report indicate that organizations can’t afford to neglect the security controls that help mitigate the risk of ransomware.
There are huge costs involved with rectifying the damage from a ransomware attack, whether you pay the ransom or not: downtime, investment in resources, brand damage, opportunities lost, and potential regulatory fines.
Panaseer’s CCM platform can help organizations overcome many of the challenges that led to this breach by measuring and monitoring the effectiveness of their security controls, especially around ransomware.
Find out more in our blog on how to mitigate ransomware using Continuous Controls Monitoring.


