
Crossing the CAASM: Panaseer featured in Hype Cycle for Network Security
In the space of a year, Panaseer has been featured as an inaugural vendor for pioneering two new Gartner Hype Cycle categories. The latest is Cyber Asset Attack Surface Management (CAASM). In July 2020 Panaseer was featured as an inaugural vendor in the new category of Continuous Controls Monitoring (CCM) for Risk Management.
Within a year’s time, we are now thrilled to be included as an inaugural vendor in the new category of Cyber Asset Attack Surface Management (CAASM) for Network Security.
CAASM brings together cyber asset management and vulnerability analysis, creating a trusted cyber asset inventory that enables IT and security teams to more efficiently identify control gaps and prioritize remediation efforts.
What is CAASM?
Gartner describes Cyber Asset Attack Surface Management (CAASM) as 'an emerging technology focused on enabling security teams to solve persistent asset visibility and vulnerability challenges,’ while CCM measures and evaluates overall organizational security control effectiveness to advise on underperforming controls.
It’s a testament to our remarkable customers and an innovative data science approach to security that industry experts recognize the impact of better understanding the basics of cybersecurity – whether that’s through monitoring and assuring your security controls or improving visibility in asset and vulnerability management.
Why is Cyber Asset Management so important in CAASM?
The value of CAASM lies in:
- Getting full and persistent visibility into an organization’s device asset attack surface.
- Quicker and more accurate audit and compliance reporting.
- Access to consolidated asset views for multiple stakeholders and purposes across the organization.
- Uncovering and gaining security visibility into shadow IT.
The Cyber Asset Management Challenge
Cyber Asset Attack Surface Management is replacing manual and time-consuming collection and consolidation of device asset inventory data. Understanding the assets in the organization is fundamental for IT security. The adage rings true: ‘You can’t protect what you don’t know’.
But there is also the important element of context. In an article on measuring asset inventory, security analytics expert Raffael Marty explained that almost everything you measure that’s related to security must be put within the context of the assets or devices in your environment: ‘If there are 100 vulnerable devices on our network, is that good or bad? If you have 100,000 devices, it’s good. If you 102 devices, it’s really bad.’
Combining CAASM and CCM
Both emerging technologies, Continuous Controls Monitoring and CAASM, go hand-in-hand. CAASM helps organizations understand the existing attack surface, and CCM identifies and advises on corresponding underperforming controls, and the specific metrics, policies, and thresholds that should be used to measure them.
As an experienced CISO and security metrics expert, David Fairman said in an article about controls coverage metrics and how they relate to CCM: ‘If there are control gaps or failures, you have exposure and that’s where the incidents are most likely going to occur.’
Combined, CAASM and CCM provide visibility into the total cyber exposure of an organization and give security teams confidence that their controls are in place and working. This provides a comprehensive view across all areas of security, aligned to any framework, and with a continuous view of current status against both internal and external policies. The below diagram illustrates how we see the new CAASM and CCM categories advancing an organization’s security program.
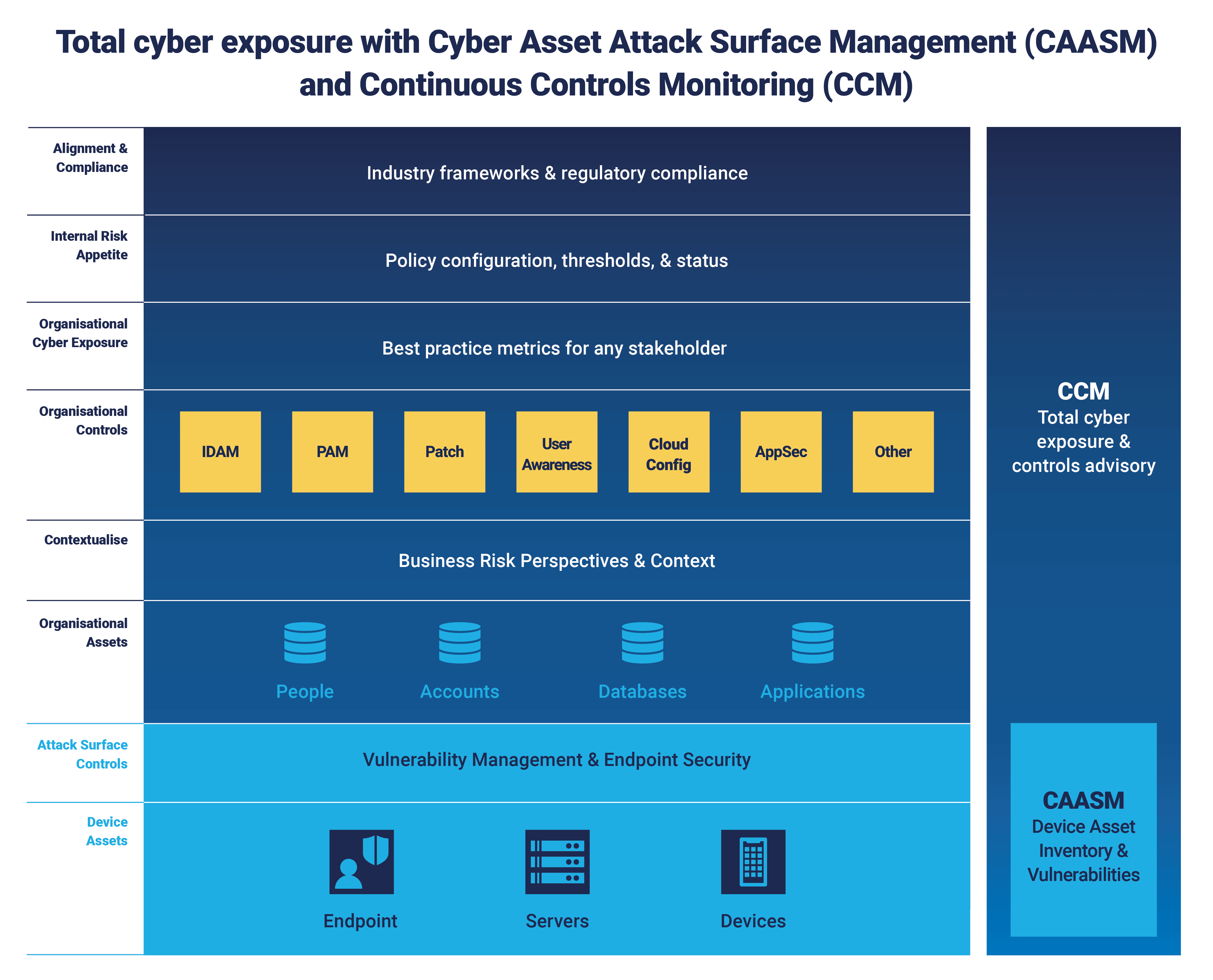
"The new CAASM and CCM categories are the cornerstones of a mature and effective security program. They provide a foundation for better understanding an organization’s security posture and total cyber exposure. Implementing these new emerging technologies will put organizations in a stronger position to protect themselves, prioritize their internal security efforts, and view security contextualized to the business." says Panaseer’s Chief Marketing Officer, Sean Goldstein.
If you are a Gartner client, you can read the entire Hype Cycle for Network Security, 2021 report on their website.


