
Nine essential cybersecurity metrics for the new CISO
What metrics does a new CISO need to measure? When joining a new organization as a security leader, it’s imperative to prioritize essential cybersecurity metrics. For this Metric of the Month, we spoke to a CISO who will remain anonymous.
Suffice it to say, he is a well-established cybersecurity leader with 20 years of experience in financial services, currently holding a leading role at a Fortune 500 bank. We caught up to discuss what a CISO needs to measure when they’re joining a new organization, both before they’ve taken the position, and after they land in the new role.
The prospective CISO must prepare
“Before joining an organization,” says our contributor, “I like to case the joint.” That means, in short, using tools that are readily available to assess the attack surface of the organization. “A company cannot live in a bubble, but a company with a good security program will try to minimize the number of exposed web portals. But this isn’t always the case.” There will always be something you can look into:
- They need a website: companyname.com.
- Maybe their customers need a login platform: support.companyname.com.
- Employees might need to log in too: remote-access.companyname.com.
- Partners, corporate clients, and non-general users might also need to log in.
Companies can create a proliferation of exposed internet services. Sometimes the business demands it, but it can also be down to a lack of standard security principles like zero trust and least privilege.
“When I joined a previous organization, I was shocked, shocked, at what I had to secure. There were close to 40,000 live addresses exposed to the internet. “These are the kind of systems my mum could find. They are eye candy to a threat actor because they can be found easily with a script key or open-source tools. This information is freely available on the internet. “When someone attacks a company with real intent, they don’t do it opportunistically. They do the homework. The same goes for a potential CISO looking to step into a company.”
By getting an understanding of the attack surface from an attacker’s perspective, you have an advanced idea of their security program and the ability to prioritize once you become the new CISO.
Metrics to measure when you’re a new CISO
When you’re at the company, you will (hopefully) have a set of enterprise security tools at your disposal. The priority, according to our contributor, is to focus on the perimeter – the internet-facing systems, “because that’s where the bulk of the threat and risk comes from.” It’s really valuable to have a baseline that tells you what your perimeter looks like to threat actors. “I want to see the attack surface area of my most critical risks, because that’s the priority of where our protection needs to be.”
Here's a list of nine metrics our contributor suggests for a new CISO to prioritize:
1. Number of assets
Although a complete asset inventory is foundational and valuable, you should prioritize specifically the assets that represent the attack surface area. It’s not easy to get complete visibility across the estate, but utilizing tech like Cyber Asset Attack Surface Management (CAASM) and Continuous Controls Monitoring (CCM) makes life much easier for the new CISO looking to shine a light on a new environment.
2. Average days to resolve a critical vulnerability on internet-facing systems
Is it 15, 20, 30 days? Naturally, there will be a level of criticality of each system, and probably a matching average. “Ideally, I would want to remediate all critical vulnerabilities on internet-facing systems within seven days.” For more on patching the most important vulnerabilities, check out our previous article on vulnerability prioritization.
3. Authentication on internet-facing systems
If you want to have access controlled by usernames and passwords on internet-facing systems, the more the better. That's a hygiene bullseye target for any threat actor.
4. Staff with privileged access
Privileged access management and identity access management are whole areas of security in their own right, but understanding who has admin access to endpoints, systems, or production is valuable to your overall hygiene knowledge. And as another dimension of that…
5. Staff with privileged access who are using multi-factor authentication (MFA)
The higher the better. MFA provides that extra level of protection for particularly sensitive privileged accounts, such as administrators.
6. Average days to crack an enterprise password
It’s key for security leaders to look at that. Many passwords can be cracked within a week, so they should be a priority.
7. Number of policy or control exemptions
This can often be ignored or swept under the rug, but it is really important. “When I have joined organizations, I always ask for three years of audit findings and policy exceptions. I think it provides an understanding of the culture of the organization – whether they truly fix things or kick the can down the road.”
8. Internet-facing systems in the CMDB
This relates back to the number of assets. It’s not always enough to know how many internet-facing assets you have, but also to document it in the CMDB and provide some context. Which systems in the CMDB are internet-facing? These are the priority systems. But it can be difficult to work this out because you need to stitch together data from multiple systems – firewalls, scanners, and asset inventories.
9. Reconciling internet-facing systems with intrusion prevention
Intrusion prevention is one of the standard controls to run on your systems. “In one organization I joined, intrusion prevention had been purchased, they had blinking lights on in the data centers, and the project was ticked off as complete. Once I started my measurement program, though, the measurement didn’t show intrusion prevention systems online or active on the correct internet-facing systems. They had basically bought the flashing lights and never plugged them in.” The moral of the story is you can’t just spend millions on technology and expect to be protected. How do you know it's running effectively and completely? You need to develop a discipline to do assurance and measurement. Only then can you truly call your technology controls effective.
We generally call this discipline CCM, as mentioned above. This final metric typifies the concept of controls coverage. You need to make sure the right security controls are present and effective on the appropriate systems. And remember, controls aren’t just a bunch of cyber tools. A control also takes into account whether the tool is deployed, but also operational, effective, with an up-to-date version.
For the sake of example, we have mocked up a CISO metrics dashboard in our platform to see what some of these metrics might look like:
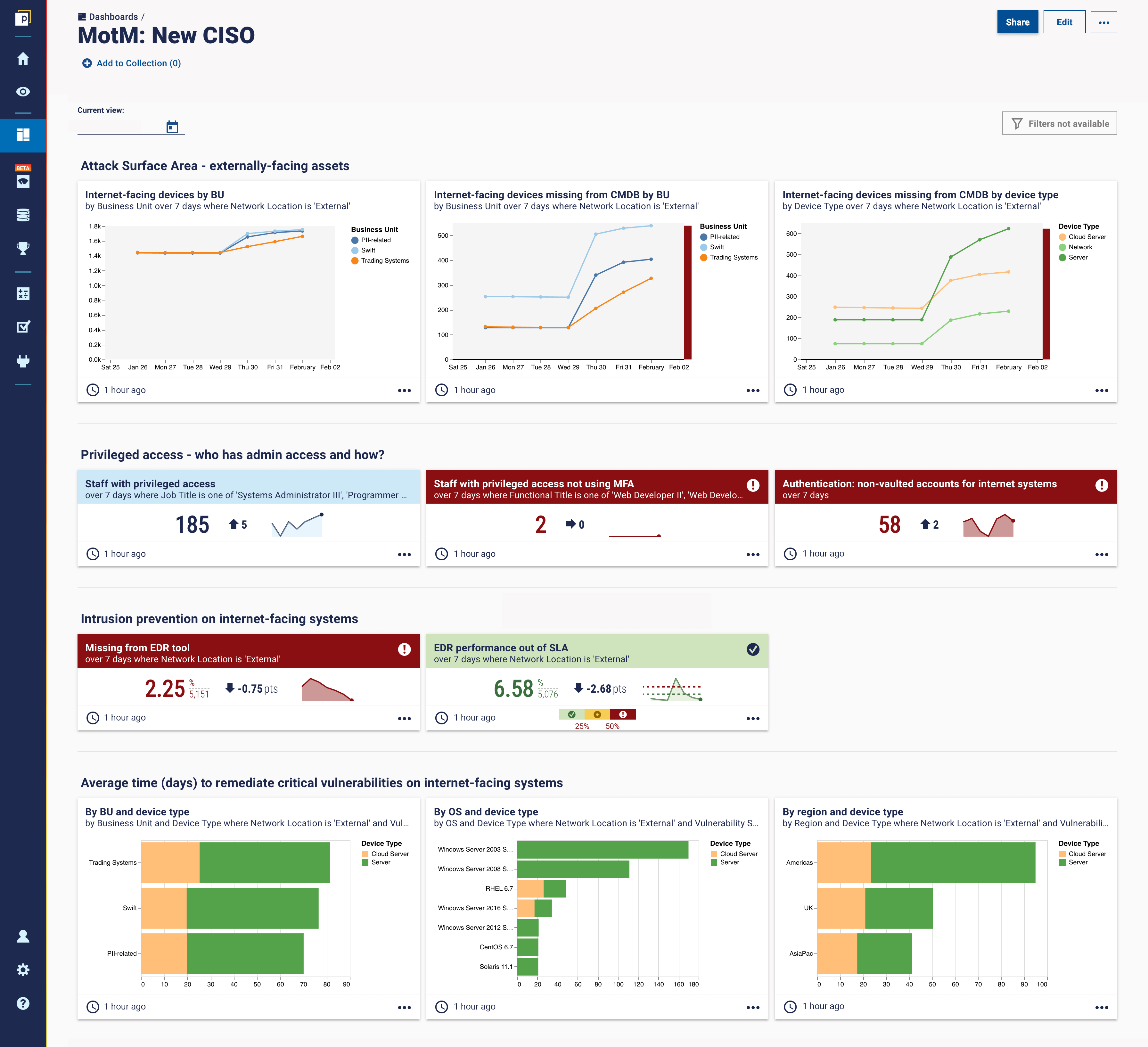
If you’re interested to see how you might be able get this dashboard or something like it, please reach out or book a demo!
Advice for the new CISO
Taken all together, these metrics will tell you a lot about your attack surface and what you need to protect as a new CISO. The key is to focus on what the threat actors can see from the outside – your internet-facing systems. “If your mum can find it, the bad guys can find it and exploit it.” There are a few new technologies out there that can really help with this concept, especially looking at the attack surface. H
ere at Panaseer we offer CAASM – Cyber Asset Attack Surface Management – as a key part of our platform. It provides a trusted cyber asset inventory and unprecedented visibility into your attack surface. Beyond the attack surface, the next stage of our platform’s technology, Continuous Controls Monitoring (CCM), provides assurance of controls on the assets making up that attack surface, and automates security measurement with hundreds of out-of-the-box metrics. This allows you to understand your cyber posture across your organization based on geography, business unit, or business process.
That way you can prioritize remediation and shift your cybersecurity approach from reactive to proactive.

