13 cyber insurance questions you’ll have to answer to get coverage
July 07, 2022
Cyber insurance used to be relatively easy – a few forms, high coverage, low premiums. But times are changing.
It’s becoming increasingly difficult for organisations to get cyber insurance. Capacity for cyber insurance is down but demand is up – causing premiums to rise 27.5% in Q1 of 2022. This is exacerbated by an increase in both the frequency and severity of cyber claims over the last few years.
There’s also been an increase in scrutiny, with cyber insurance questionnaires becoming more complicated. Insurers expect you to be able to evidence strong cyber hygiene across a range of security domains. Would you be able to accurately answer all these questions? And how easy would it be to collect the data?
The risk is that if you provide inaccurate data on your security controls, then the insurer could refuse to pay out in the event of a breach. That’s where real-time cybersecurity metrics are extremely valuable, as you can have confidence you’re giving an accurate picture of your controls status.
Here are 13 common questions from cyber insurers plus some example dashboards that show what a data-driven response would look like. These dashboards from our platform show the effectiveness of security controls for each question.
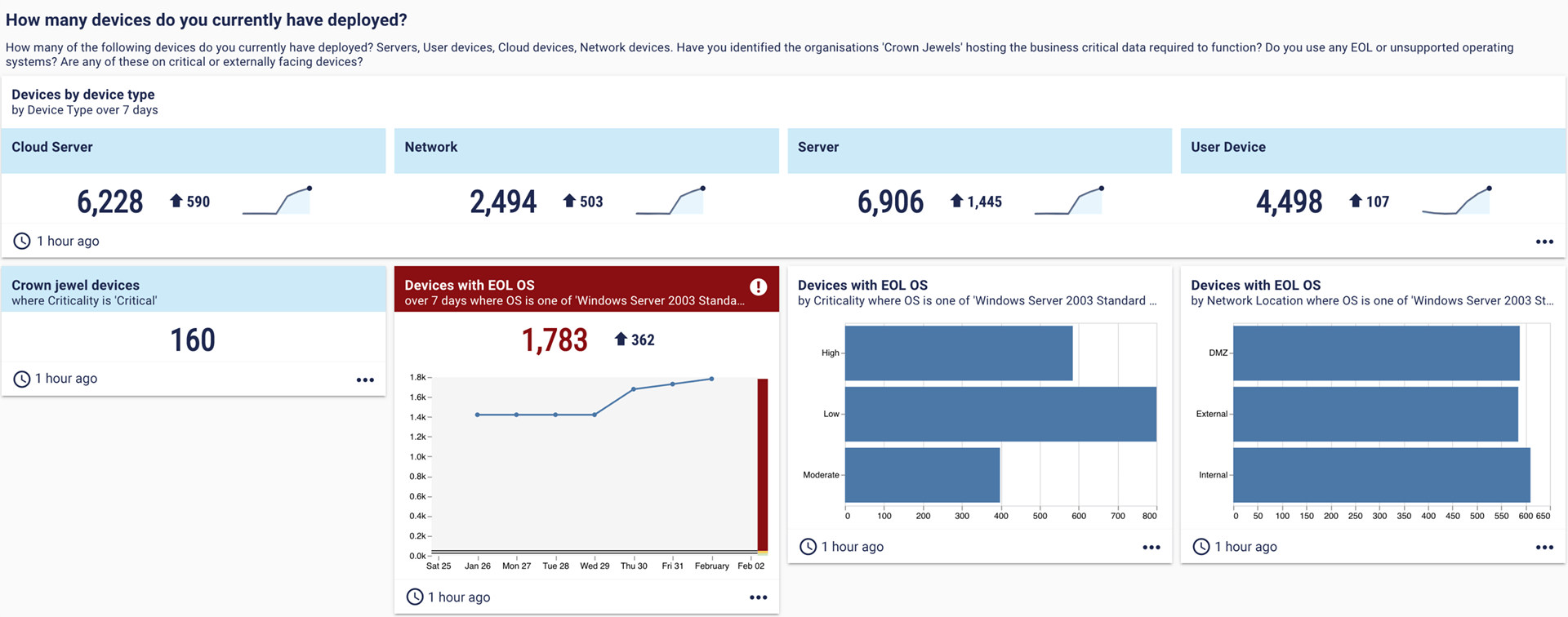
1. How many devices do you currently have deployed?
This is a fundamental cybersecurity metric, whether you’re looking at the context of cyber insurance or your security programme at large. It’s also important to understand device types, and which are the most important – your “crown jewels”.
2. What devices are running end-of-life software?
The above dashboard also highlights any of the devices in your organisation that are running end-of-life software. These pose a risk to vulnerability and patch management because they don’t receive new security updates or patches.
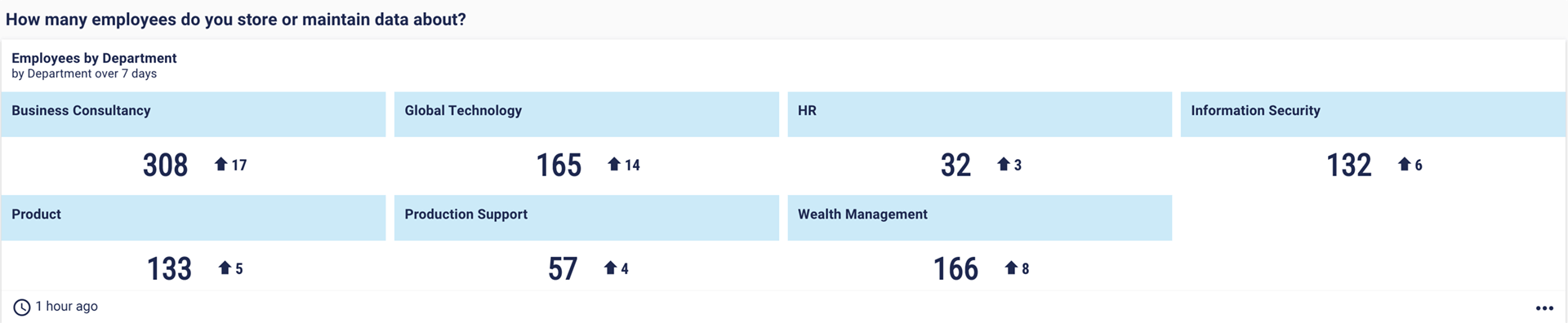
3. How many employees do you store or maintain data about?
You’re liable for all the data your organisation stores and maintains. Insurers therefore want you to know about and protect important data such as the personal identifiable information (PII) you hold about your employees.
Here, the number of employees is broken down by business department.
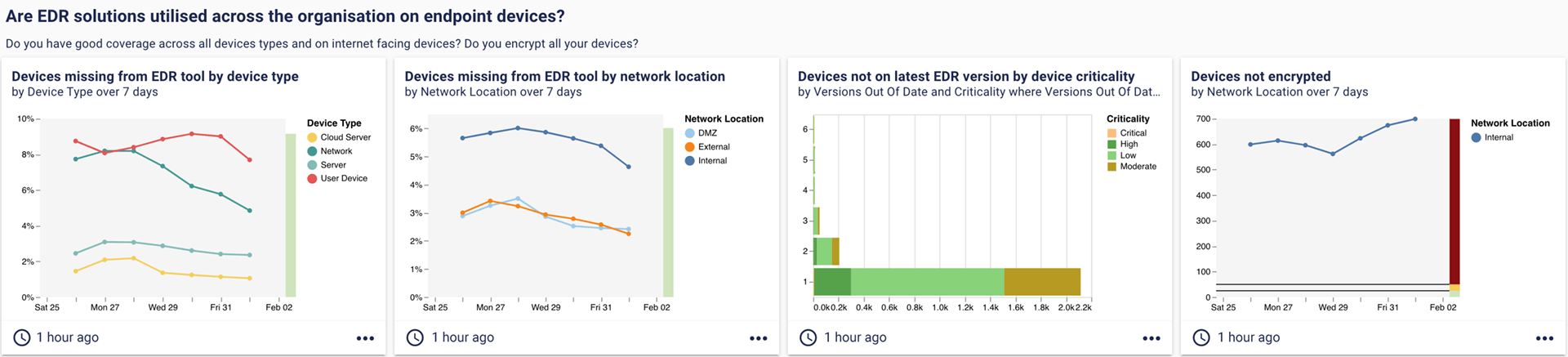
4. Are EDR solutions used across all endpoint devices?
Insurance brokers point to EDR coverage as one of the main indicators of a secure network, noting that it is essential to “impress underwriters”. Each of these views shows the breakdown of EDR coverage split by a different filter – by device type, network location, or device criticality.
5. Are your endpoint devices encrypted?
The eagle-eyed will have spotted an encryption dashboard under the EDR question above. While EDR and encryption are not the same, both are valid ways to secure your endpoints, and may come up in cyber insurance questionnaires.
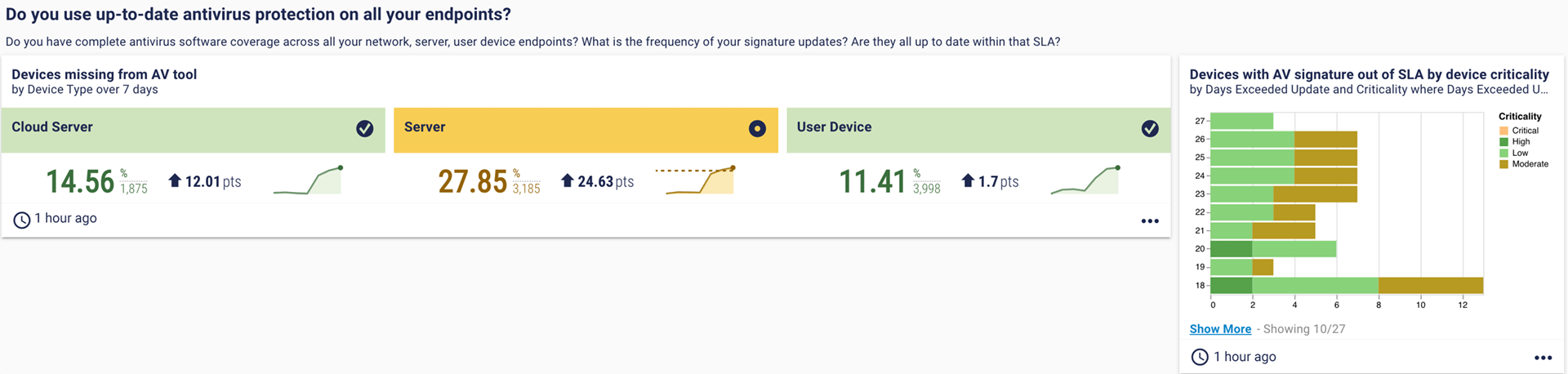
6. Do you use up-to-date antivirus protection on all your endpoints?
Similar to the EDR question, but with AV. Looking at AV coverage across your devices, split by device type. The card on the right shows the number of devices with an out-of-date AV signature, split by device criticality.
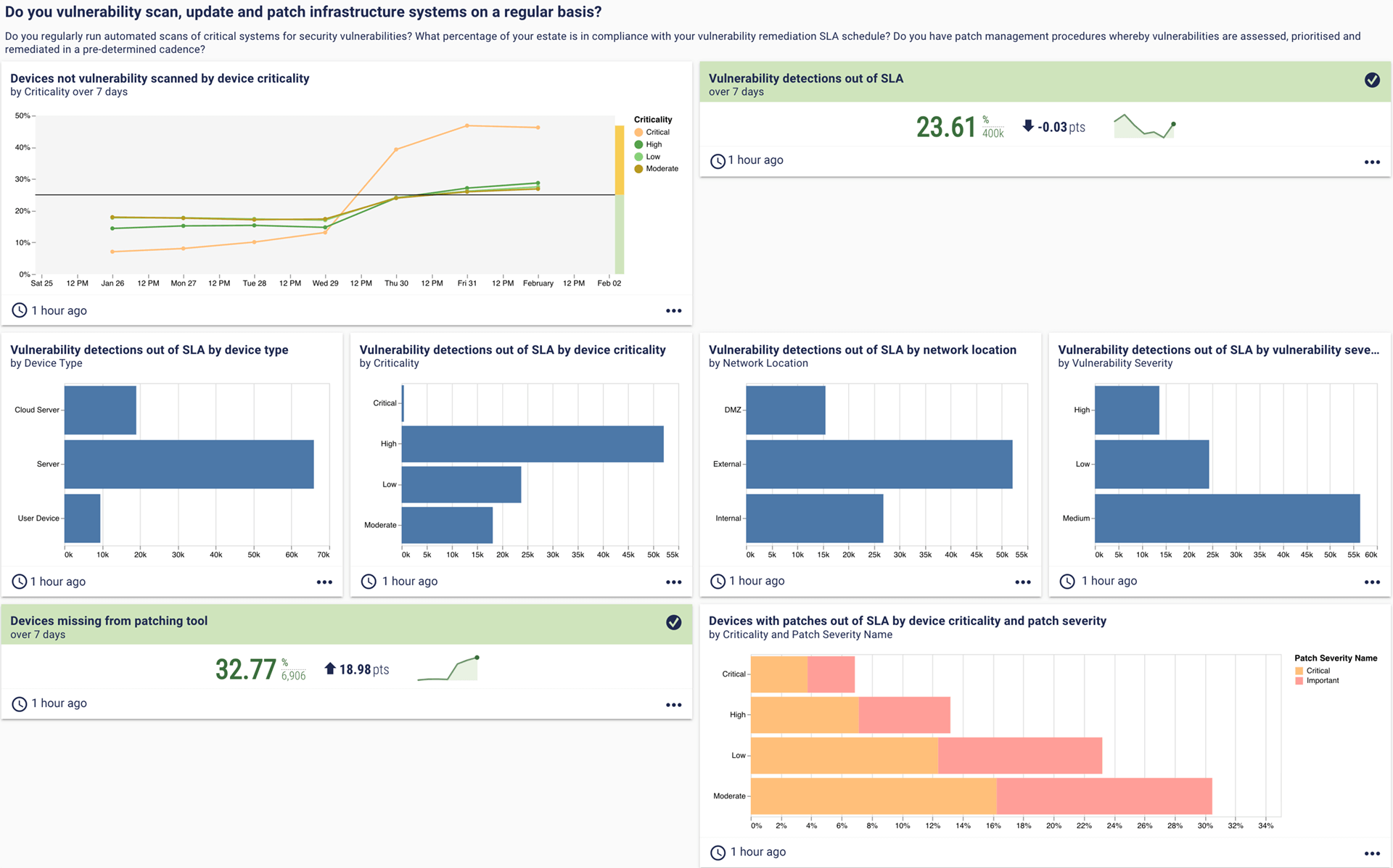
7. Do you vulnerability scan, update and patch infrastructure systems on a regular basis?
In an article for Cybersecurity Dive, Jack Kudale (founder and CEO of Cowbell Cyber, which provides cyber insurance for small- to medium-sized enterprises) highlighted patch management as one of the fundamental things that insurers are looking for.
This dashboard shows coverage of your vulnerability scanning and patching tools as well as additional insight into both domains. Cards like the bottom right – “Devices with patches out of SLA by device criticality and patch severity” – highlight priority areas for remediation to improve security posture.
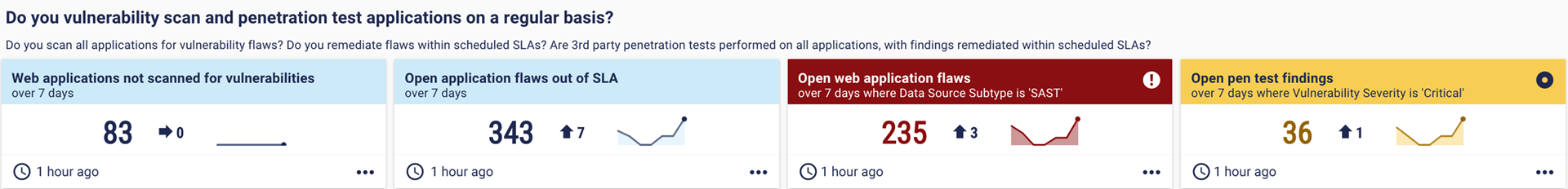
8. Do you vulnerability scan and penetration test applications on a regular basis?
Unauthorised access to an application can be particularly damaging, so application security controls are a top priority for both cybersecurity leaders and insurers.
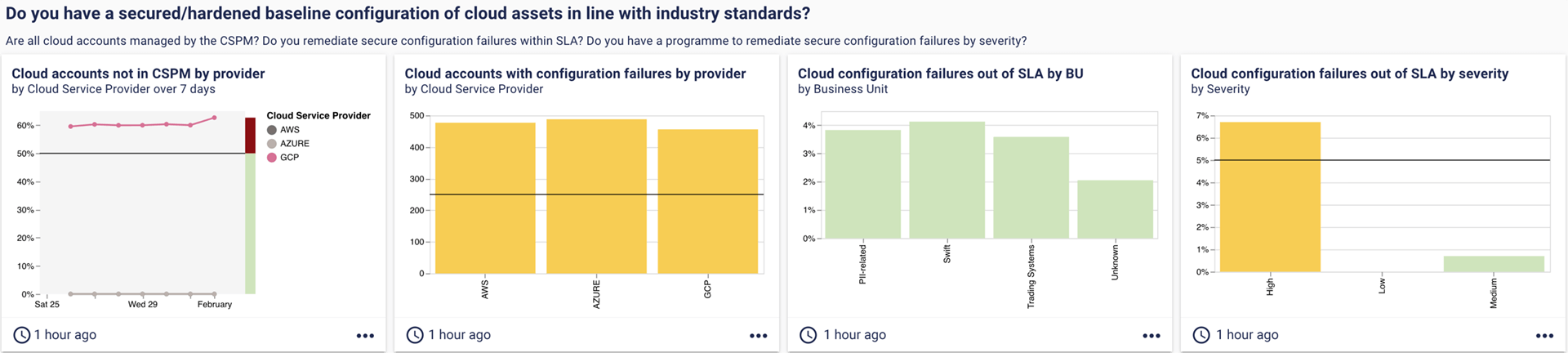
9. Do you have a secured/hardened baseline configuration of cloud assets in line with industry standards?
According to one report, the proportion of companies with most or all of their IT infrastructure in the cloud is expected to increase from 41% to 63% in the next 18 months. This rapid shift to hybrid environments has led to a rise in cloud misconfigurations – a metric that has become increasingly important to measure.
This dashboard explores the problem and highlights configuration failures across providers, business units and severity.
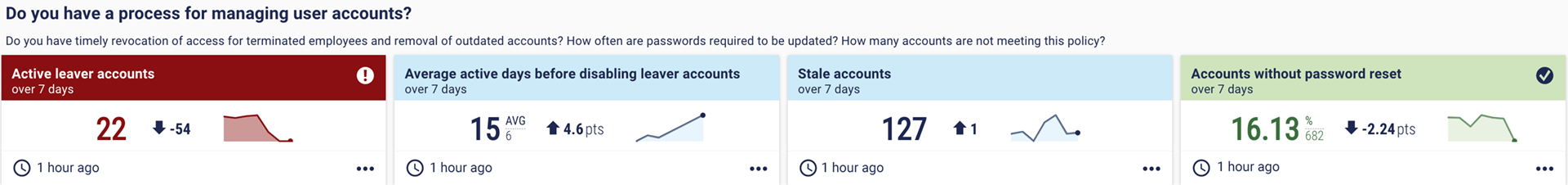
10. Do you have a process for managing user accounts?
Joiner/mover/leaver security can be a hassle, especially in large organisations. But any access or privileges that are available to someone not still with the company (or team) pose a considerable risk.
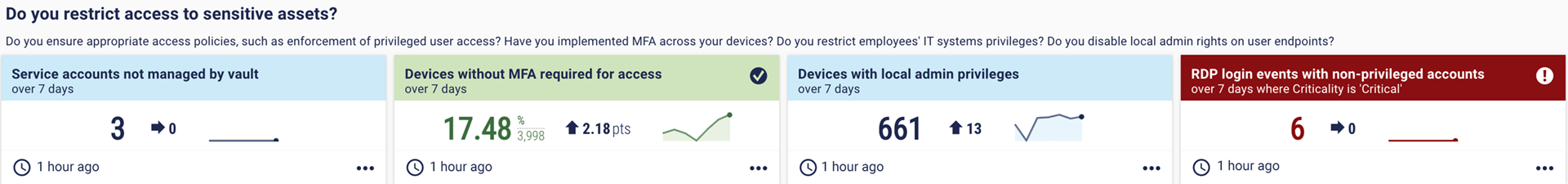
11. Do you restrict access to sensitive assets?
Privileged Access Management is an essential part of any cybersecurity programme. Insurers will want to be aware of your practices. This dashboard looks at service accounts managed by a vault, devices with local admin privileges, and remote (RDP) login events, as well as MFA.
12. Do you have multi-factor authentication in place on relevant devices?
MFA is crucial for cyber insurers. According to the Council of Insurance Agents and Brokers (CIAB), insurers require MFA, or the potential policyholder is deemed “virtually uninsurable”, and a quote is refused.
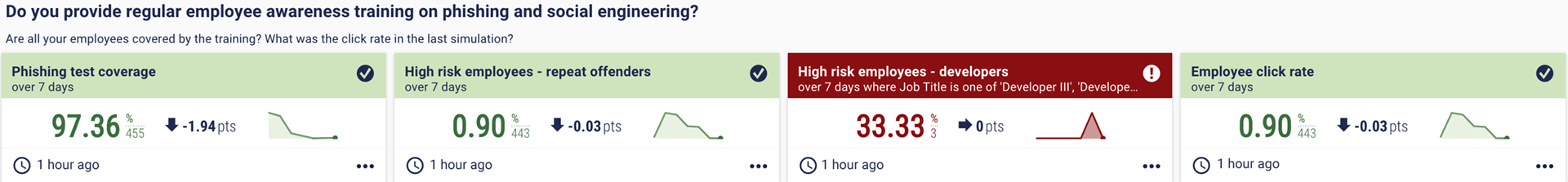
13. Do you provide regular employee awareness training on phishing and social engineering?
The CIAB said something similar about awareness training – it’s a must-have for cyber insurers. A strong cyber awareness culture is a powerful tool for your security posture, but it can be hard to measure. That’s why we’ve included phishing test metrics, such as test coverage, click rate, and high-risk employees that repeatedly click on phishing links.
The final word
These examples should provide insight on not only the kind of questions that cyber insurers will ask (there will be more!), but also how you can answer them with trusted cybersecurity metrics.
Our customers can use CCM (Continuous Controls Monitoring) to demonstrate cybersecurity posture to cyber insurers in a more complete and data-driven way. It becomes much easier to pull all the relevant data together and gives you confidence the information is accurate.
Our platform also allows you to provide access to the dashboard with secure permissions, so insurers can view the exact metrics and data you intend to show them. On top of that, you can also share continuous monitoring of security controls with historic trend data, to give an exact picture of security posture at a specific point in time. That means in the event of a breach, you can highlight the offending device, and show the controls in place at the time.
If you’re interested in seeing how it works on a demo, get in touch.