
Four security metrics that prove you’re a good bet for cyber insurance
The cyber insurance saga continues. Premiums are high, coverage is limited, insurers are piling on more scrutiny, and it’s tougher to qualify. To help reduce the pressure, we're exploring the security metrics and measures that cyber insurers will expect to see. One year you’re filling out a single-page questionnaire and picking up cyber insurance with ease. The next year, it’s 18 pages and suddenly you can’t answer every question. Jim Doggett, CISO of Semperis and longtime Continuous Controls Monitoring advocate, is fresh off the back of such an experience. Jim highlights the increasing need for cyber insurance: “For most companies, getting cyber insurance is becoming mandatory. Boards, investors and customers apply enough pressure so that virtually every company needs to have cyber insurance.” It also makes good business sense as well, providing additional support in the event of a breach. We asked Jim what cybersecurity metrics organisations should measure continuously so they can answer cybersecurity insurance questionnaires more efficiently. "Cyber insurers need to know key statistics that indicate you're secure overall. It’s impossible for them to do a rigorous audit on every potential customer, so they need to know about specific things that show you have good cyber hygiene.” If these “indicators” of good hygiene are in good order, one can better make the assumption that the overall environment is more secure. Jim gives four examples:
Patching
Effective patch management is an indicator of good cybersecurity practices. “It's still one of the most common problems out there today,” says Jim. “And if you're doing a good job patching, my guess is you're probably doing a good job doing several things besides that.” In an article for Cybersecurity Dive, Jack Kudale (founder and CEO of Cowbell Cyber, which provides cyber insurance for small- to medium-sized enterprises) highlighted patch management as one of the fundamental things that insurers are looking for. There are a handful of useful metrics to measure here, illustrated with examples from the Panaseer platform. Patching metric examples The coverage metric measures how many of your devices are missing from your patching tool. It’s worked out by comparing the assets covered by the patching tool to the overall asset inventory. It’s common for organisations to find gaps in this kind of coverage and it can be particularly challenging if the asset inventory isn’t continually updated. 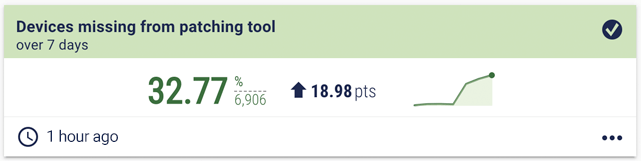 Average time to patch. This shows if you are patching within your policy thresholds.
Average time to patch. This shows if you are patching within your policy thresholds. 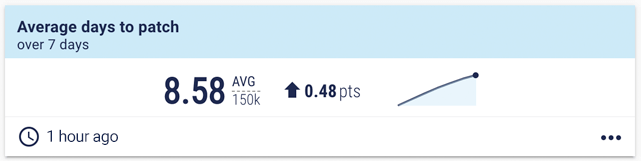
Inventory
“When I talk to people about security, inventory is always near the top of the list. We've said this for years, but I’ll say it again. You can't secure what you don't know is there,” says Jim. An up-to-date asset inventory is crucial not only to securing your environment, but also to measuring the effectiveness of your cybersecurity programme. As shown in the patching tool coverage metric, it's crucial to have an up-to-date inventory, not just so you know what assets you are protecting, but also as a baseline for many of your security metrics and measures. Almost all your security metrics start with the question of coverage. If your tool doesn't cover the entire landscape, how effective is your programme? Inventory metric examples The metric here is “How many devices do you currently have deployed?”, and we've split them by device type. 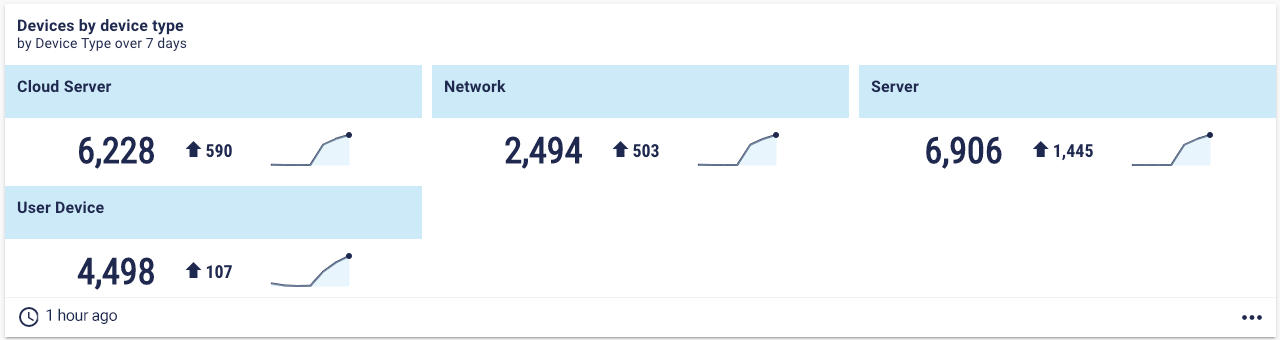 But assets aren’t the only thing you need to inventory. It’s also important to have an inventory of your applications. This dashboard shows the number of applications split by what business process they relate to and the region they are used in.
But assets aren’t the only thing you need to inventory. It’s also important to have an inventory of your applications. This dashboard shows the number of applications split by what business process they relate to and the region they are used in. 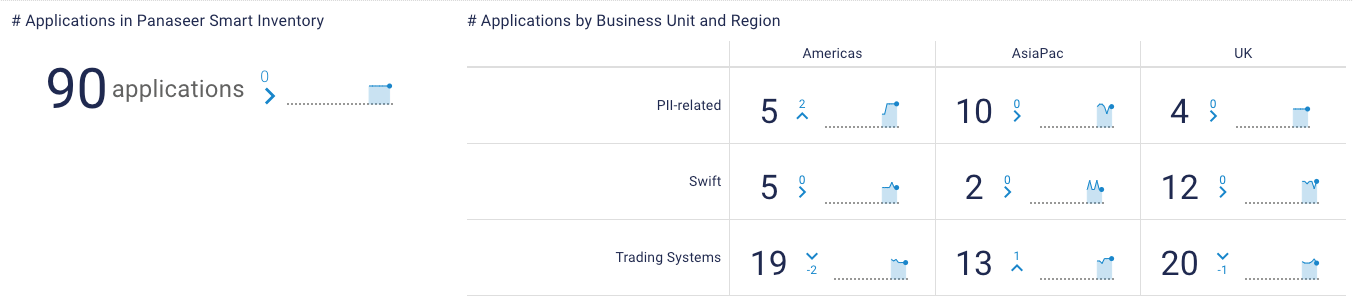
Access control
“I split access control into two categories – regular access, and privileged access.” When it comes to regular access, Jim mentions the importance of provisioning and deprovisioning. A good example would be measuring accounts that are no longer needed, for example if an employee leaves the organisation. These metrics include:
- Number of active accounts that should have been deactivated
- Average time to disable former employee accounts
- Time at risk from active accounts
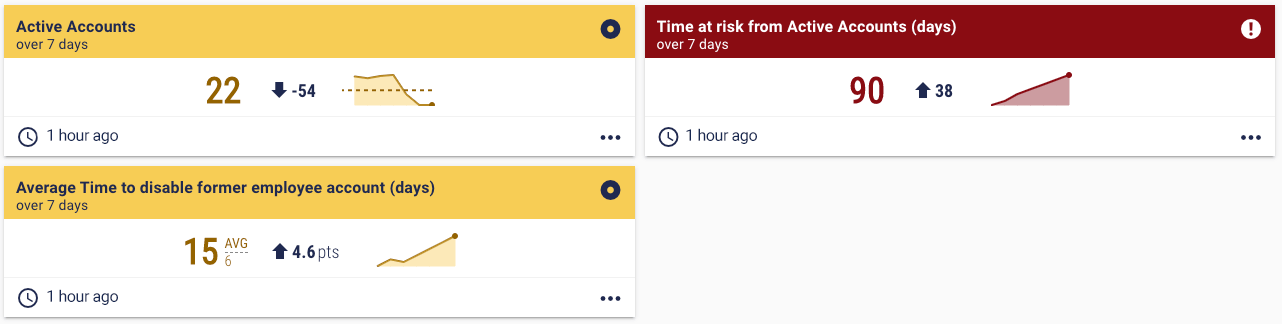 For more detail, we have discussed active leaver metrics before in this series. Then we come to privileged access. The first question to ask, says Jim, is “Have you separated out privileged access from regular access?” In other words, do your users have separate accounts for privileged activities versus regular activities? Good privileged access management is how you help mitigate many cybersecurity threats such as ransomware. “I don’t need privileges to use the internet and send emails, so why should I have them? Privileges should only be usable as and when required. They need to be separate. Almost every breach starts with an individual being compromised. And if they have privileges, it can be catastrophic.” Here are some basic metrics for privileged access:
For more detail, we have discussed active leaver metrics before in this series. Then we come to privileged access. The first question to ask, says Jim, is “Have you separated out privileged access from regular access?” In other words, do your users have separate accounts for privileged activities versus regular activities? Good privileged access management is how you help mitigate many cybersecurity threats such as ransomware. “I don’t need privileges to use the internet and send emails, so why should I have them? Privileges should only be usable as and when required. They need to be separate. Almost every breach starts with an individual being compromised. And if they have privileges, it can be catastrophic.” Here are some basic metrics for privileged access: 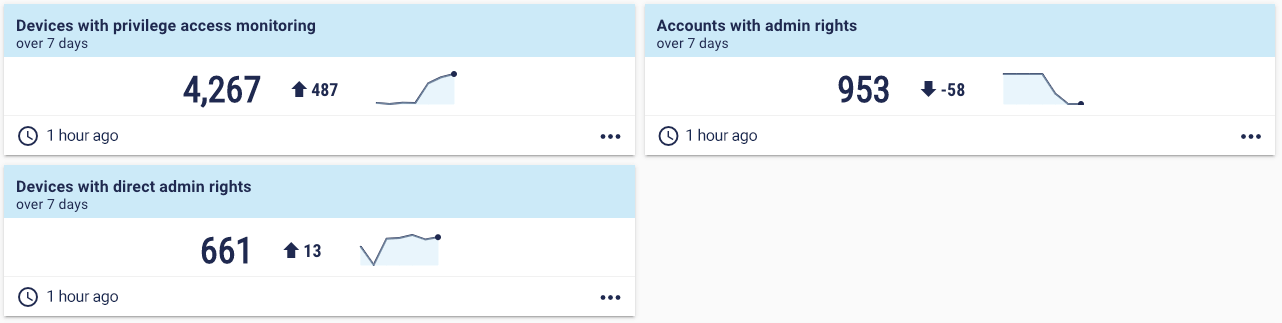 For greater detail, read our deep dive on privileged access metrics.
For greater detail, read our deep dive on privileged access metrics.
Endpoint protection
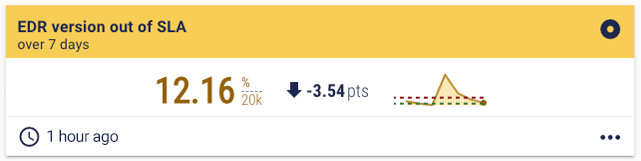
Insurance brokers point to EDR coverage as one of the main indicators of a secure network, noting that it's essential to “impress underwriters”. Jim notes that it’s important to measure the coverage of your endpoint tools, such as AV or EDR, to see if any devices lack the protection required by your policies. And not only that, but also ensuring your endpoint tools are running the latest version. Endpoint protection metric examples Devices missing from AV and EDR may sound like a straightforward metric, but it can be hard to work out. The first step is the all-important up-to-date inventory. Then scan data is needed from your AV and EDR tools, which can be difficult to manage if you have more than one of each tool. The scan data is then compared to the inventory, so you can pinpoint how many devices in your inventory do not have AV or EDR coverage. This is a powerful metric that highlights compound risk. 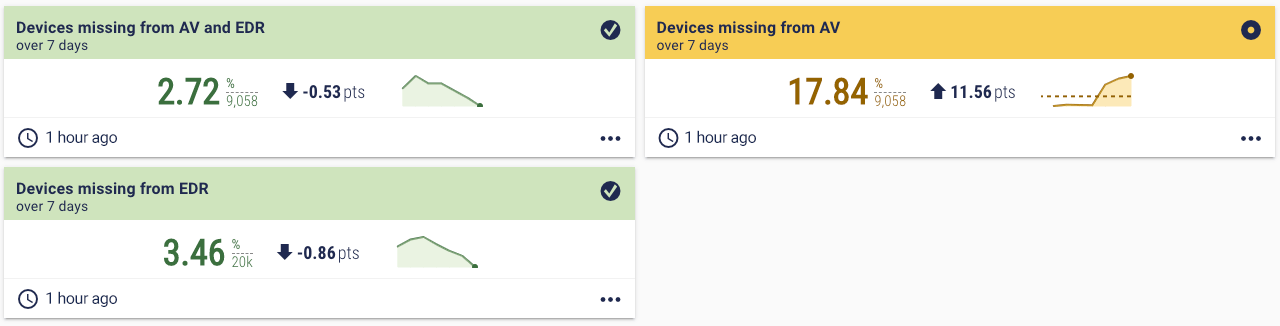
The future of cyber insurance
Beyond these metrics, Jim provides predictions for the future of cyber insurance. First, he thinks that cyber insurers will demand more certifications, such as SOC 2 or ISO 27001. And second, Jim has been championing Continuous Controls Monitoring (CCM) for several years now. He sees it as a technology that can be used by security and compliance to answer questionnaires for insurers or regulators with speed, confidence, and accuracy. “The objective of the insurance questionnaire is to understand that you have sufficient security controls in place. CCM is the best way to do that. It proves that you’re continuously monitoring your security controls, and that your security efforts are effective.” Jim believes that in the future, cyber insurers will offer better premiums to companies using CCM. “They can’t afford to audit every possible customer. They’re going to lean towards those companies that measure these things on a continuous basis and are willing to share measures on their security controls.” Our recent cyber insurance research found the same: 89% of insurers believe it would be valuable to have direct access to customer metrics and measures proving the status of their security controls. Eventually, questionnaires have to go away. “It’s not that people answer incorrectly or directly lie. It’s that a questionnaire rarely provides the full picture of a company’s security posture. Many answers are yes/no.” For example, it asks: Do you use AV and EDR? Yes. But is your AV and EDR running on every endpoint? Probably not. “Insurers will start to demand a better process,” says Jim. “As threats like ransomware increase the dollar cost of an incident, they need better understanding of a company’s security posture so they can make a calculated risk, while not charging a ridiculous premium.” If you want to find out how Panaseer's platform helps with the cyber insurance challenge, get in touch for a demo.
Learning from cyber insurance
Most mature cybersecurity programmes are already doing what Jim highlights here: patching, inventory, access control, and endpoint protection. But you have to be able to prove you’re doing them effectively, whether that’s to cyber insurers or regulators. Not every organisation will be running continuous measurement on these practices. Doing so could be the difference between getting cyber insurance and not getting it. Jim provides a piece of advice for those struggling to get cyber insurance: “Use the questionnaire as a tool to learn from.” They tend to cover the crucial areas of cybersecurity, so it can act as a blueprint that indicates areas you can improve.

