
Toxic combinations of privilege in cybersecurity
‘The term ‘toxic combinations’ alludes to pharmacology in the sense that if you put two drugs together, you can kill the patient. In the risk world, it refers to people that have been granted privileges that should not have been put together because they create risks.'
Continuous Controls Monitoring (CCM) sits above your existing security tooling, ensuring that all controls are fully operational and all assets are protected.
Welcome to our Metric of the Month series. In this post, we discuss toxic combinations with Andrew Jaquith, the man himself. If you work with security metrics, chances are you will know that Andrew literally wrote the book on security metrics. He’s been a great supporter and innovator of Continuous Controls Monitoring for several years, having served in executive security and risk roles at several global financial service institutions.
What are toxic combinations in cyber security?
Toxic combinations can be a little difficult to define. I have seen two different concepts labeled as a ‘toxic combination’. The first was identifying a combination of risks that could make an individual potentially exponentially dangerous. For example, if a person had the following risks, that would be a toxic combination:
- Privileged access to a business-critical application;
- Multiple failed phishing tests;
- Unpatched vulnerabilities on their device;
- And EDR isn’t covering their device.
The second was used specifically for toxic combinations of privilege, whereby someone would have multiple privileges that could make them potentially dangerous to the organization.
The term ‘toxic combinations’ alludes to pharmacology in the sense that if you put two drugs together, you can kill the patient. In the risk world, it refers to people that have been granted privileges that should not have been put together.
So, I asked Andrew to clarify. Toxic combinations are more in the realm of risk rather than security specifically, something that Andrew calls very basically ‘a dangerous set of privileges’. An individual that fits the first definition of toxic combinations would be more appropriately assigned as a 'high-value target', or HVT. But more on that in a later issue. Here’s what Andrew had to say:
"The term ‘toxic combinations’ alludes to pharmacology in the sense that if you put two drugs together, you can kill the patient. In the risk world, it refers to people who have been granted privileges that should not have been put together because they create risks that are highly inappropriate or breach a boundary within the firm. What I've seen in the industry is that a ‘toxic combination’ is tech privileges that a person possesses that could cause them to undermine the integrity of a core process, that is forbidden by law or statute."
That means we’ll be shifting slightly away from a security focus and more into the realm of risk.
An example of toxic combinations in cybersecurity
The classic example for risk leaders in financial services is Sarbanes-Oxley section 404 (or S-Ox). There was essentially collusion between accountants and business people, who created fraudulent accounts at companies like Enron and WorldCom. The idea of S-Ox is to prevent that. As Andrew put it, "the job of S-Ox is to prevent corporate crooks from cooking the books."
"S-Ox requires CEOs and CFOs to attest quarterly that financial results are true and accurate and that there are controls in place to prevent them from being undermined. In this context, a toxic combination would be a set of privileges that collectively could give rise to doubt that."
To try to illustrate a further example, here’s a mock-up dashboard from our platform based on the way one of our customers is measuring toxic combinations of privilege and segregation of duties. Our customer measures risks around these challenges like ‘manipulation of performance’, ‘erroneous or unauthorized trades’, and ‘failure to achieve best execution’, which can all have different levels of risk severity. For example, the severity may change depending on the books the risk might be on.
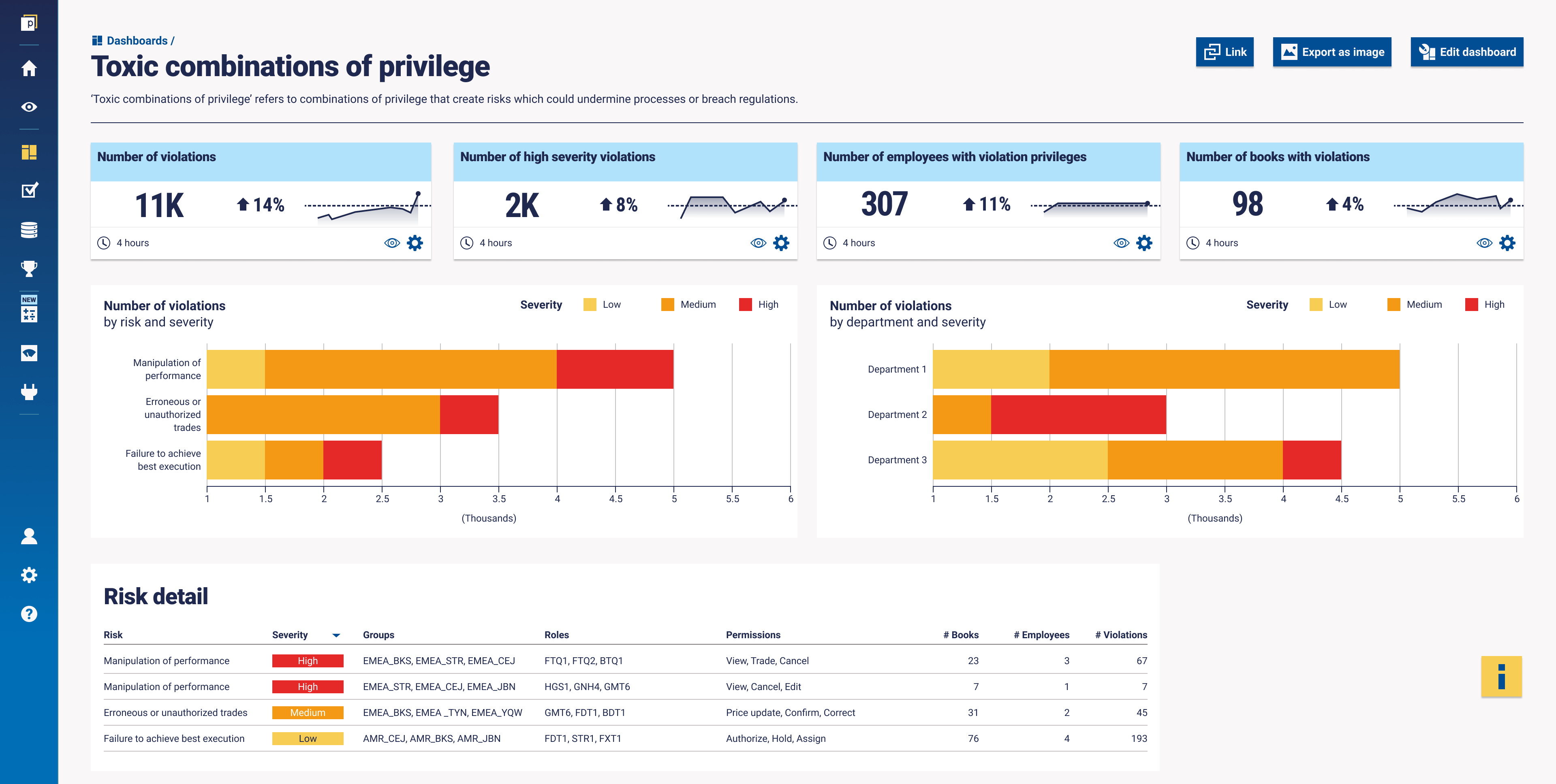
How have you measured toxic combinations during your career?
As part of a risk and compliance program, Andrew has managed data science teams that were responsible for measuring toxic combinations. They maintained a scope of S-Ox-related assets, such as books and records, trading, settlement, client accounts management, onboarding clients, etc. These need to be assessed for toxic combinations of privilege. Part of that meant looking at the concept of ‘front-end’ and ‘back-end’ access.
When you have business and developer entitlements on systems that are upstream of books, records and financial statements, you now have the ability to influence or corrupt the integrity of those systems.
In other words, the team had a set of ‘known bad’ toxic combinations of privilege. These included on one hand the front-end ‘write’ privileges, meaning that a person had user entitlement to a system and could create or modify financially influencing information about a customer or trading or accounting. On the other hand, it also included back-end ‘write’ privileges, meaning they were a system administrator, DBA, or they had code commit rights on the underlying code that the system is built on. This means they could both use the system and ‘fiddle with results’.
"When you have business and developer entitlements on systems that are upstream of books, records, and financial statements, you now can influence or corrupt the integrity of those systems," says Andrew.
People with both of these privileges could potentially be in a place where they could undermine financial results, which, as we noted above, is bad. Either one alone is not problematic. Being able to see something isn't nearly as big of a problem as being able to change something. But then does someone with admin rights immediately become ‘toxic’? ‘No, as long as they have a business reason for those privileges’. But it can be the case that some combinations are required for people to do their jobs. That perhaps contributes to why it is so important to measure toxic combinations.
Why do toxic combinations present a security challenge?
While it may sound pretty simple in concept – don’t give people access that allows them to commit fraud – ‘it’s actually quite complex’.
It assumes that you have a complete inventory of employees and their privileges.
How so? Well, ‘it assumes a few things’, says Andrew. "It assumes that you have a complete inventory of employees and their privileges’. This is something that many organizations struggle with. We discussed Identity Access Management a little in our last Metric of the Month with Andreas Wuchner. Without investing in automation, no single team or application can reasonably know where or how many different entitlements a person has. There is also the challenge of users having different identities. 'It can be challenging enough to get an accurate and up-to-date inventory of all employees, with identities and privileges on top of that adding an extra layer of difficulty."
Then, once you have that inventory of employees and privileges: ‘It assumes you know which of these are ‘write’ privileges, meaning you can modify something, and ‘read’ privileges, meaning you can see something’. But there’s more contextual information needed about the privileges, such as when they were granted and if they were granted appropriately. And all this together needs to be ‘complete, accurate and regularly updated’, according to Andrew. As Continuous Controls Monitoring advocates, it would be remiss of us not to mention that this is just one of the CCM use cases – automatically updating inventories of employees and access.
Toxic combinations are 'known bads'. You need to stop them and get rid of them right now. With toxic combinations, you need to focus on the kinds of cases where you can draw a straight line between the incident and potential financial loss, whether via crime or sanction.
Why is it important to measure toxic combinations?
Some risks need to be measured because of policy (the high-value targets mentioned earlier, for example). However, some risks need to be measured because of law. Regulations like Sarbanes-Oxley require organizations to look into, measure, and remediate toxic combinations. Not doing so could result in fines from regulators, or the risks themselves that the regulations are in place to avoid. ‘Toxic combinations are ‘known bads’, says Andrew. ‘You need to stop them and get rid of them right now. With toxic combinations, you need to focus on the kinds of cases where you can draw a straight line between the incident and potential financial loss, whether via crime or sanction’. While it can be a mature concept for some organizations, a lot of auditors want to see the measurement of toxic combinations. It works in a two-pass system, says Andrew: ‘In the first pass, the auditor will say: ‘Ok, company. What are your controls? Where are they applied?’ Some controls you might expect here are things like incident management controls, change management controls, and all your typical general IT controls. If you have a toxic combinations control, then that’s great and they can audit it here. If not, they will probably look at it as a risk-consult decision.
‘Auditors want to see that you have visibility into your toxic combinations. It’s up to you how you measure it. They won’t tell you how to do it, but they will express an opinion as to whether they think it’s sufficient.’ There are so many potential toxic combinations, though, that the question arises: 'Where do you stop?' Well, Andrew answered in a Metric of the Month panel discussion.
How can Continuous Controls Monitoring help with toxic combinations?
This control is all about understanding your risk threshold, what you are willing to tolerate, and managing that risk down continuously.
To answer this question, Andrew took a step back to look at the basics. First: what is a control? ‘A control is a process that includes a feedback loop and a corrective action. A sensor needs to collect some data about a thing. That thing has a tolerable operating range. When you breach the threshold, you take action to correct it.’ If you are implementing toxic combination monitoring as a control, that means you need to regularly identify toxic combinations.
Then identify how many of them you can tolerate as a fraction of your total privileges, whether that’s 1%, 0.5%, or managing them to zero. ‘This control is all about understanding your risk threshold, what you are willing to tolerate, and managing that risk down continuously. No auditor or regulator is going to tell you what that number should be, but you will be judged by the level of thoughtfulness in your control designs, as well as the degree of rigor in control execution.’ So how can Continuous Controls Monitoring help? While CCM as a category is relatively new, in many Tier One financial organizations, Continuous Controls Monitoring disciplines are well established. ‘But of course, it's all craft brewed’, Andrew notes, meaning institutions have developed primarily customized solutions.
‘The opportunity is to streamline and make proven approaches work for the companies that don’t have the resources of a bulge-bracket bank. And some institutions are planning to re-engineer their in-house efforts anyway, because their first and second efforts may not be doing everything that they want’.
Think of CCM as an evidence collection system that shows your controls are operating with integrity, and that the underlying data is trustworthy. The clearer the paper trail, the more trustworthy it’s going to be.
Andrew says that "the value of CCM is from eliminating the drudgery of collecting controls performance information regularly, and in presenting data in a way that has integrity, regularity, and traceability."
"Think of CCM as an evidence collection system that shows your controls are operating with integrity, and that the underlying data is trustworthy. The keys are consistency and cadence. Document your scope. Demonstrate the chain of custody of the data. Show the lineage: how you got it and where you got it from. Describe what you did with it: how you transformed it, how you handled it, and what you did in all the intermediary steps. The clearer the paper trail, the more trustworthy it’s going to be."
While they aren’t made to be read in order, check out security controls coverage with David Fairman and active leavers with Andreas Wuchner for some more metric goodness. Click here to learn more about how CCM can solve your cybersecurity challenges.

