Metric of the Year: Three crucial security metrics from 2021
December 15, 2021
Our final Metric of the Month for 2021 is a roundup of the most popular metrics we’ve covered this year, based on page views – a Metric of the Year, if you will.
We’d like to thank all our contributors from the past 12 months, who have given us valuable insight into the metrics and measures that help to improve cybersecurity posture. You can explore our full Metric of the Month collection or our Security Metrics Hub for all our security metrics and measurement content.
3rd: Ransomware protection metrics with Andrew Jaquith
For this article we spoke with seasoned CISO and author of Security Metrics: Replacing Fear, Uncertainty, and Doubt, Andrew Jaquith. He’s helped pioneer Continuous Control Monitoring at Goldman Sachs and JP Morgan, and is a member of our advisory board.
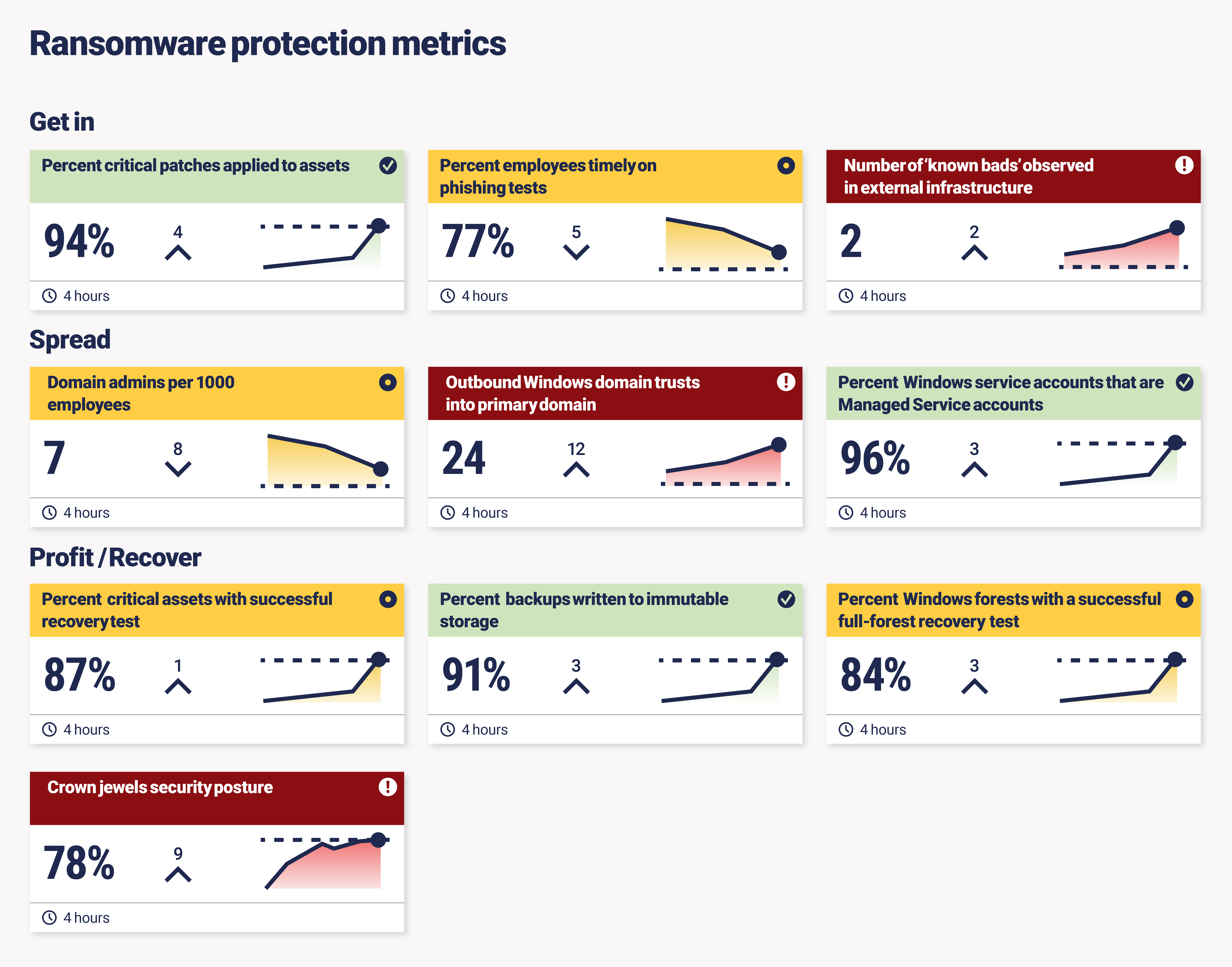
Andy outlines a three-step playbook that attackers use to propagate ransomware:
- Get in.
- Spread.
- Profit.
To protect against threat actors getting in, Andy suggests looking at metrics that represent maintaining a good security posture. That means measuring external exposure and eliminating what he calls ‘known bads’, such as ensuring your patching is up-to-date and phishing test completion rates.
For the ‘spread’ section, Andy highlighted metrics that help to reduce the risk of ransomware propagating within the organisation. This is a focus on privilege, managing service accounts, and ensuring you have multi-factor authentication in all the right places.
And finally, we come to ‘profit’. It’s unfortunately already too late for you if the attackers are profiting, but Andy shares some metrics that will help in recovery, such as the completeness of your inventory for ‘crown jewels’ and tracking successful backups.
Here’s a dashboard we mocked up:
It takes an average of five control failures for a ransomware attack to be successful. That means you need to continuously measure and monitor your security controls to make sure they are running as expected.
We’ve created a ransomware dashboard with a similar structure in our platform so our customers can not only measure their ransomware protection levels, but also present them to an increasingly cyber-savvy board.
2nd: Security controls frameworks with Phyllis Lee
Thanks to Panaseer’s partnership with the Center for Internet Security (CIS) around the Controls Assessment Specification, we spoke to Phyllis Lee, one of the leading experts in security controls frameworks. Phyllis spent decades working for the US government in cybersecurity and in the last few years has turned to providing controls guidance for the global security community as Senior Director for the CIS Critical Security Controls.
We explored what makes a good security framework – they should be achievable, provide prioritisation, and, crucially, prove that what you are doing is right. Often, frameworks are generic, with loose language, and don’t always provide great guidance on how to implement them.
That brought us onto the Controls Assessment Specification, which provides more specific, prescriptive guidance for organisations on metrics to measure to effectively use the controls framework. It’s a relatively new concept for a framework to give such detail in advising organisations what to measure and what good looks like.
Phyllis also considered the future of frameworks, highlighting the importance of automation to continuously monitor your controls. This is not just to ensure compliance with a framework, but to make sure your metrics are within thresholds and you are doing what you need to do to stay secure.
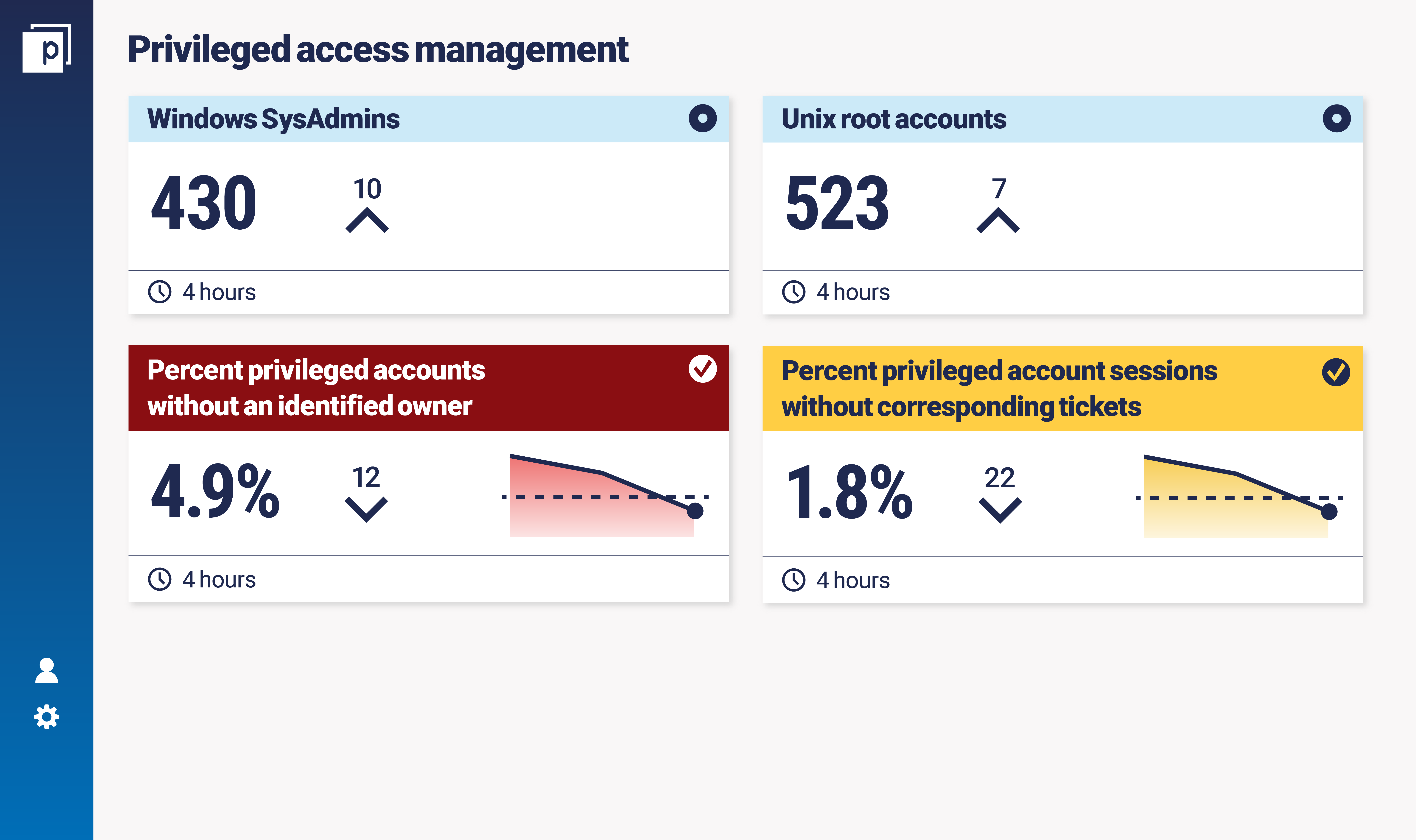
Our winner: Privileged access management metrics with David Fairman
In this instalment of Metric of the Month, we caught up with David Fairman to discuss privileged access management. David is an experienced CISO, having run successful enterprise security programmes in various industries across the globe. He’s a valued member of our advisory board, Continuous Controls Monitoring advocate, and security metrics expert.
He highlights some particularly useful privileged access management metrics, such as privileged accounts that don’t have an owner, or privileged account sessions that don’t have a ticket.
Here’s how that looks in a mock dashboard:
David also outlines a five-step guide to improving your PAM programme:
- Define ‘privilege’ based on your risk appetite.
- Discover all your privileged accounts.
- Separate duties around the creation, management, and use of privileged accounts.
- Ensure all privileged accounts have owners.
- Implement enhanced controls on your privileged accounts.
Cybersecurity in general isn’t easy, but PAM can be one of the tougher things for an organisation to keep on top of. This article provides you with insight into some useful privileged access management metrics and best practices.
The final word…
To get more interviews and discussions with security leaders and measurement experts in 2022, sign up for our Metric of the Month newsletter using the form below.